Hi Everyone
I’m back with another blog on how Vishing Campaign is carried out in a Red Teaming Engagement.

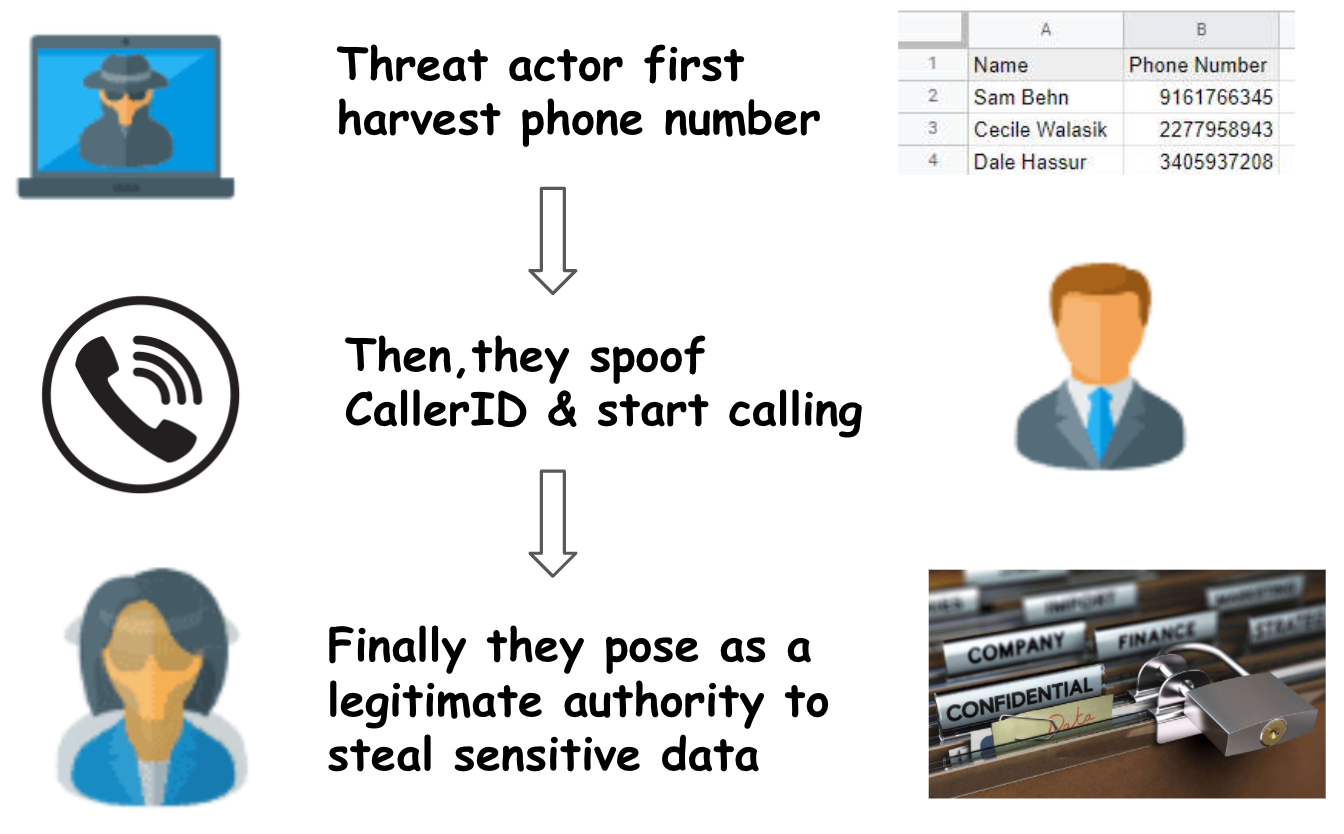
What is Vishing ?
- Telephone phishing, also known as vishing, is similar to email phishing performed over a telephonic call to gain information from the target victim.
- It involves the exploitation of a potential victim over the phone by Impersonating as another entity/person/company and eventually convince the person to share Sensitive Information.
Flow Chart of Vishing
Tools and Apps used for Vishing:
Caller ID Spoofing:
- The Basic idea behind Caller ID spoofing is to change the information that is displayed on the caller ID display.
- Most spoofing is done using a VoIP (Voice over Internet Protocol) service or IP phone that uses VoIP to transmit calls over the internet.
Useful Situations for Caller ID Spoofing:
These can be used in a vishing campaign to display that a call is coming from:
- A remote office
- Inside the office
- With partner organization
- From Co-worker
- A superior
- Delivery company
SIP & Virtual Number Providers
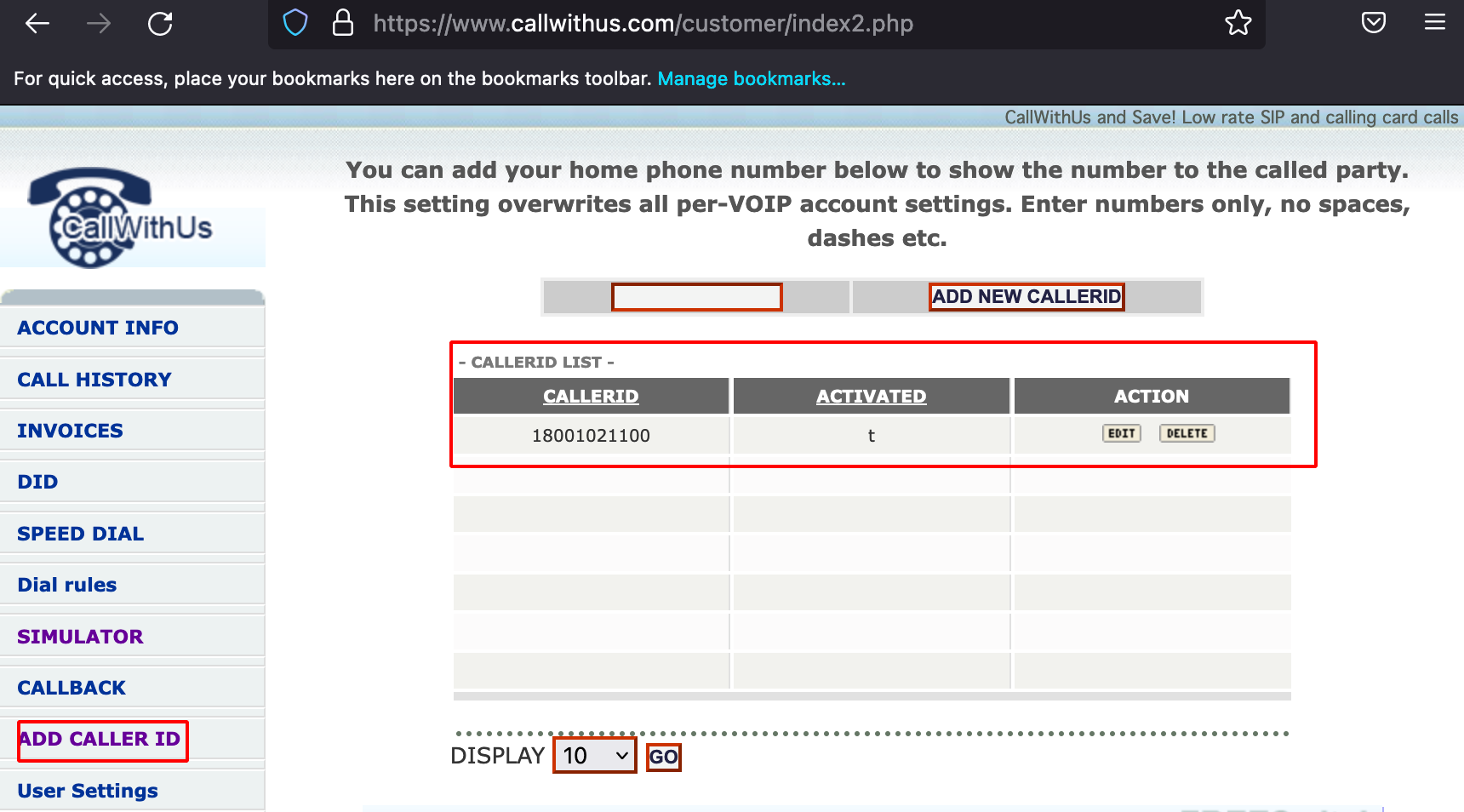
- CallWithUs - Calls to your DID (phone number) will be redirected to your SIP phone, regular PSTN or cellular phone. You don’t need a VoIP client to have calls to your DID redirected to your PSTN or mobile phone number.
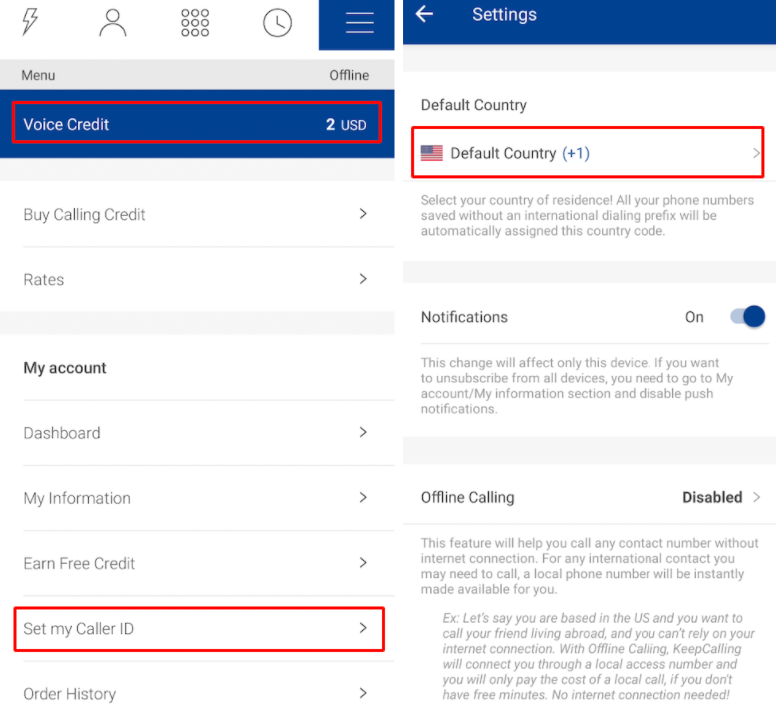
- KeepCalling - It is a Virtual Number provider, allows the user to buy credit and make International phone calls to different countries.
Configuring SIP Account with Zoiper
-
After successful purchase of SIP Account, download Zoiper Android or IOS.
-
Navigate to Settings –> Accounts –> + –> Yes –> Manual Configuration –> SIP account.
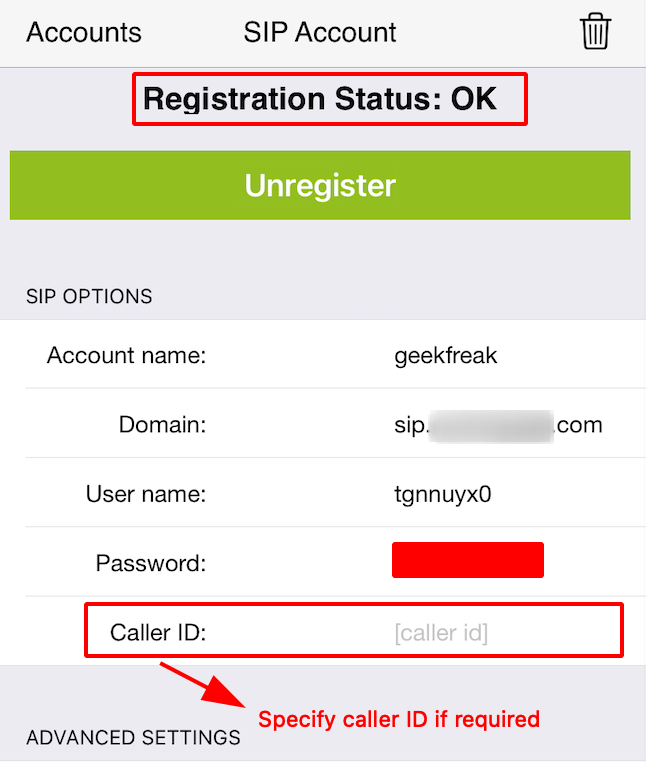
- Registration Status OK shows that the configuration is successful.
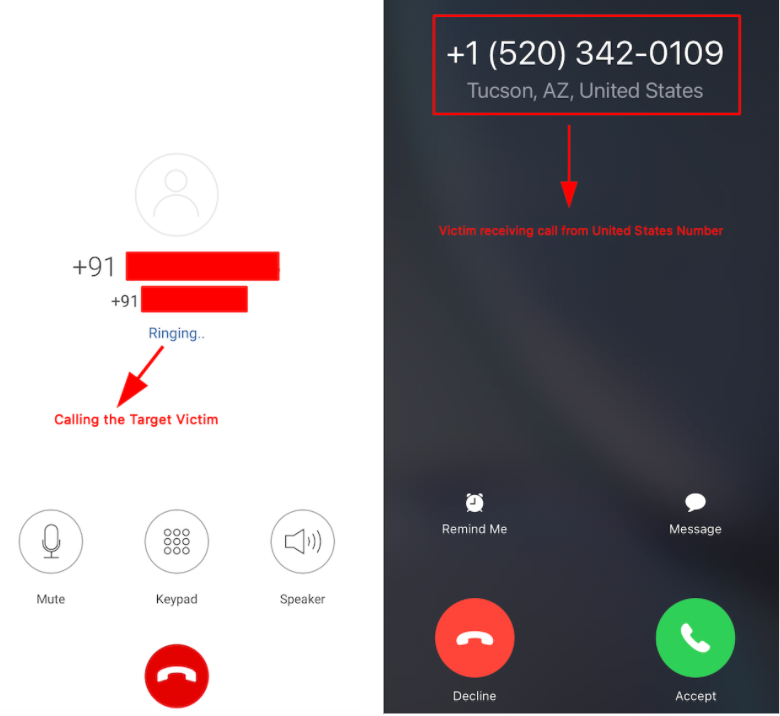
Demonstration of Vishing Scenario
Prevention for Vishing:
- Remain Vigilant and Pay Attention during Phone calls.
- Verify the identity of those who ask for your information in person or over the phone before you release any information.
- Be Suspicious of Unrecognized Phone Numbers.
References:
Attack Vector - Vishing
Caller ID Spoofing
Caller ID Spoofing: How to do it :)
Tutorial - How to Setup Asterisk Caller ID Spoofing (to troll scammers)
Dragnet: Your Social Engineering Sidekick

This post is only for Educational Purposes.
NOTE- “Do not perform vishing on the target company that you do not have permission for.”
Thanks a lot for reading !!!.