Hi Everyone
I’m back with another blog, i will cover the basic Jail Break Detection Bypass using Hopper Disassembler.
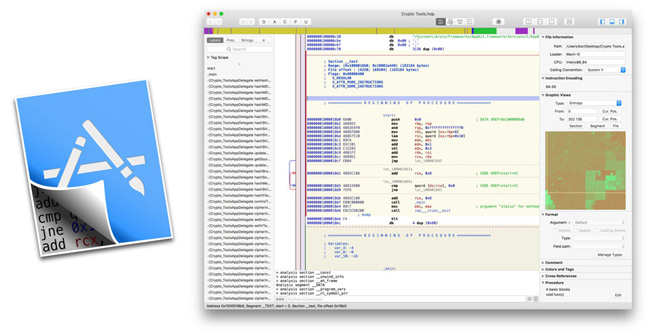
What is Hopper Disassembler?
Hopper Disassembler, the reverse engineering tool lets you disassemble, decompile and debug iOS applications.
Different ways to Bypass Jail Break Detection:
- Objection
- Frida
- Hooking
- Tweaks(A-Bypass, Liberty etc)
- Reverse Engineering(Hopper Disassembler, etc)
Note : Make sure your device is Jail Broken and Cydia is Installed.
Bypassing Jail Break Detection using Hopper Disassembler:
Step 1: Download the SecureStoreV2 .ipa file and install the application.
Note: Since the application has jailbreak detection mechanism in it, it crashes and closes whenever the user tries to open the application, hence disabling the user to use this application on a jailbroken device.
Step 2: Unzip the SecureStoreV2.ipa using the following command.
unzip SecureStorev2-resigned.ipa
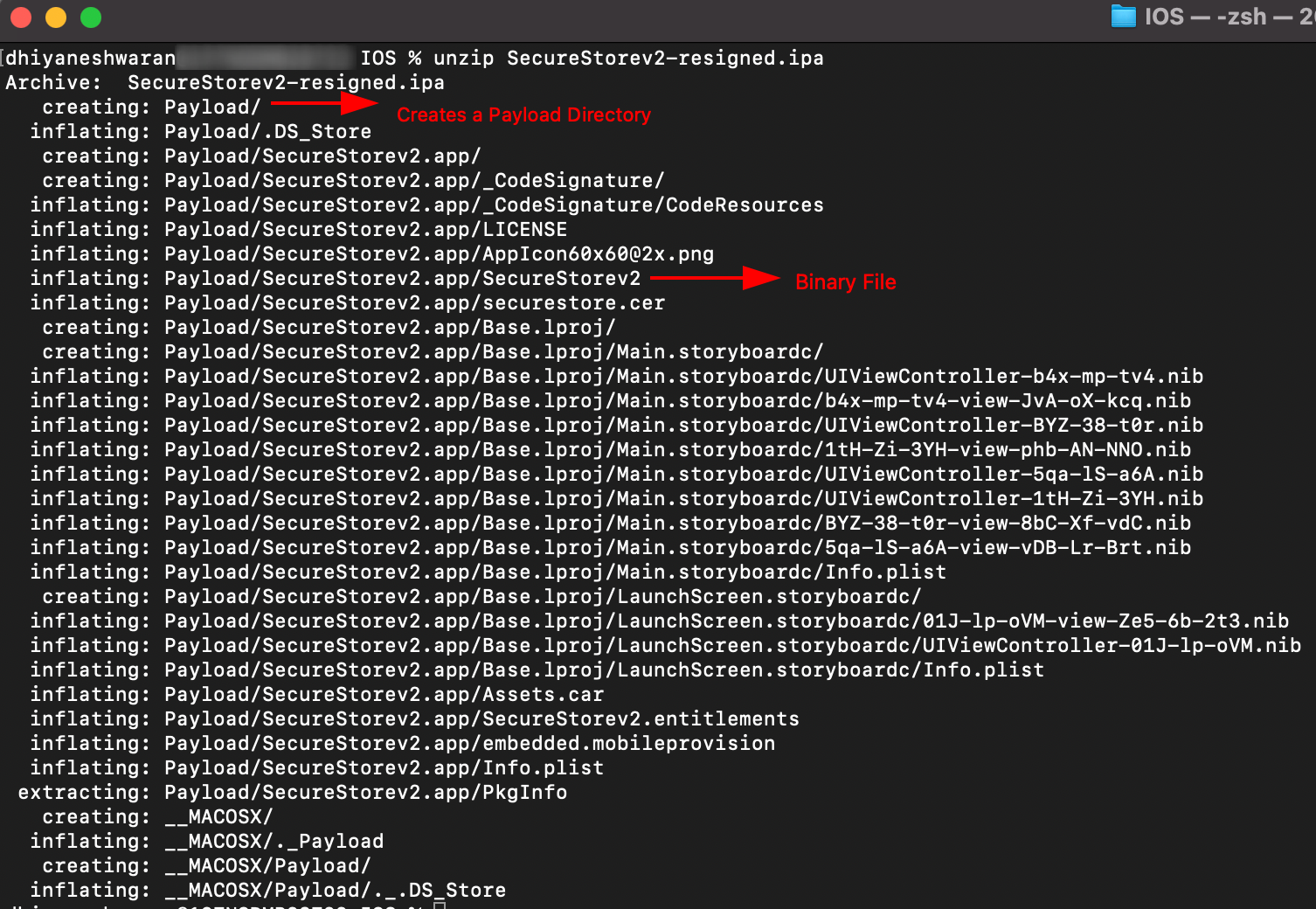
Step 3: Navigate into the Payload -> SecureStorev2.app Directory.

Step 4: Drag and Drop the SecureStorev2 Binary in the Hopper Disassembler.
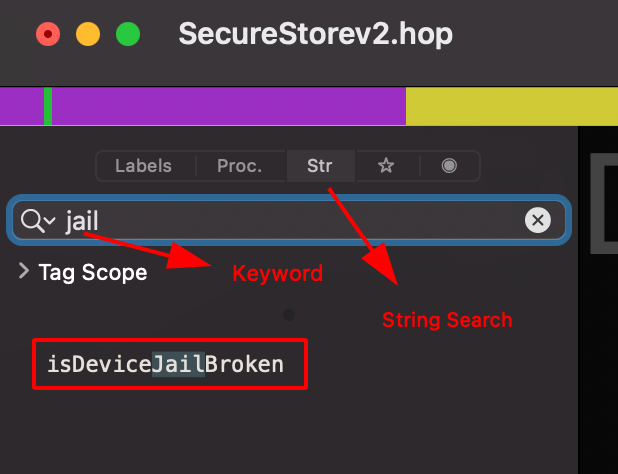
Step 5: Use str search functionality to check for jailbreak keyword.
Step 6: Double clicking on the search result,it will take you directly to the Assesmbly Instruction Set as shown below.
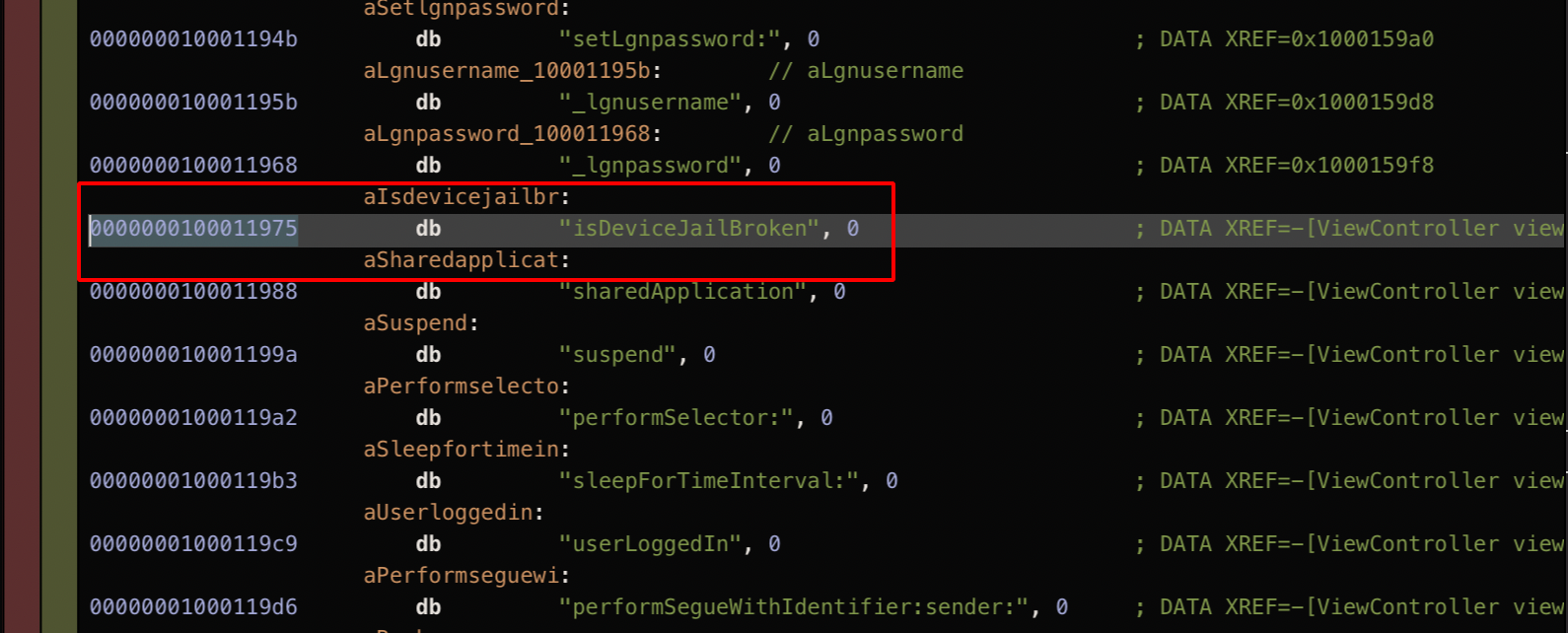
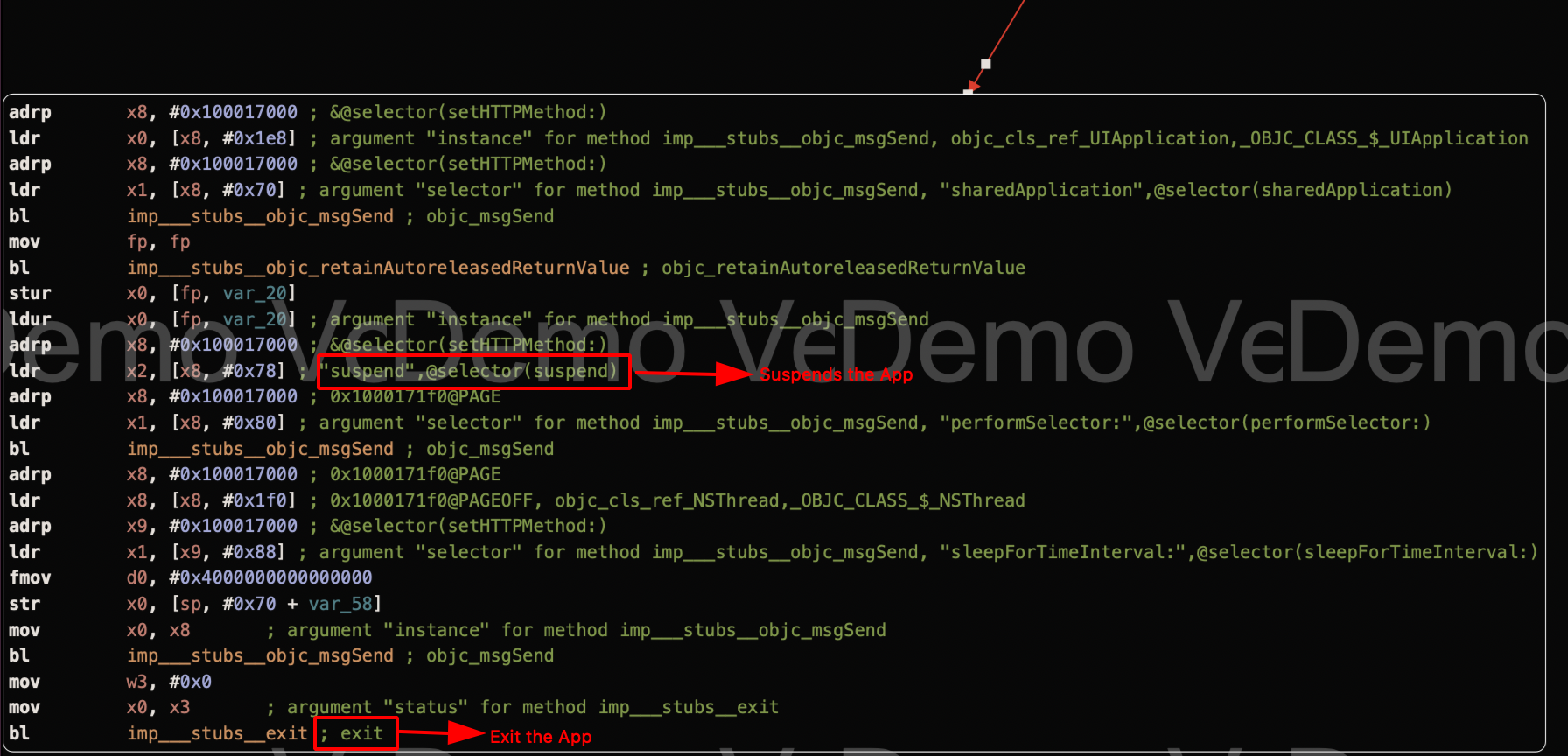
Step 7: Right click and choose isDeviceJailBroken -> References to “alsdevicejailbr”.
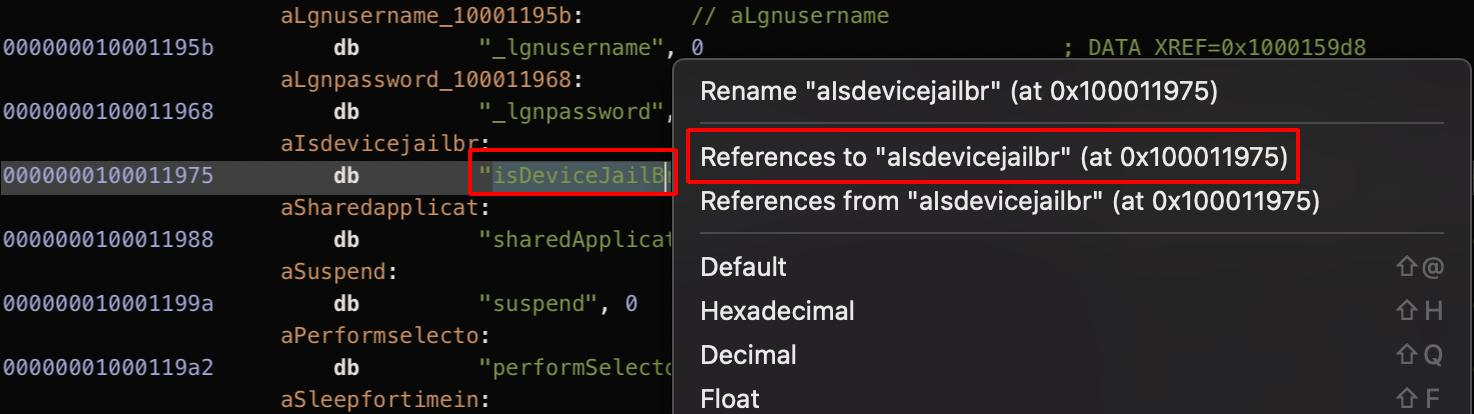
Step 8: Choose the first option from the dropdown list that appears.
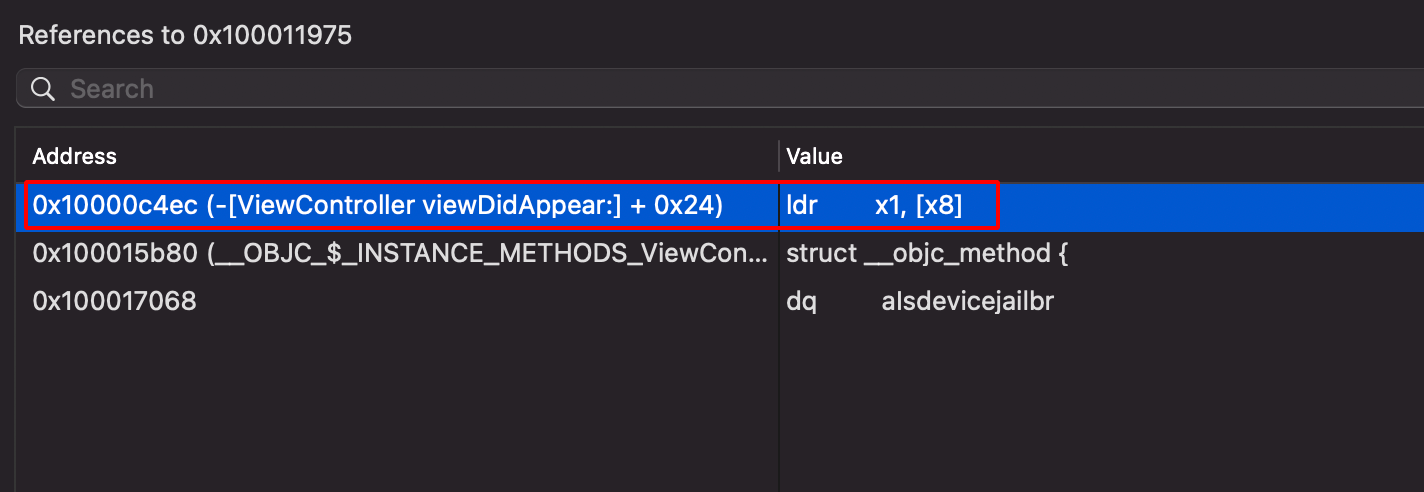
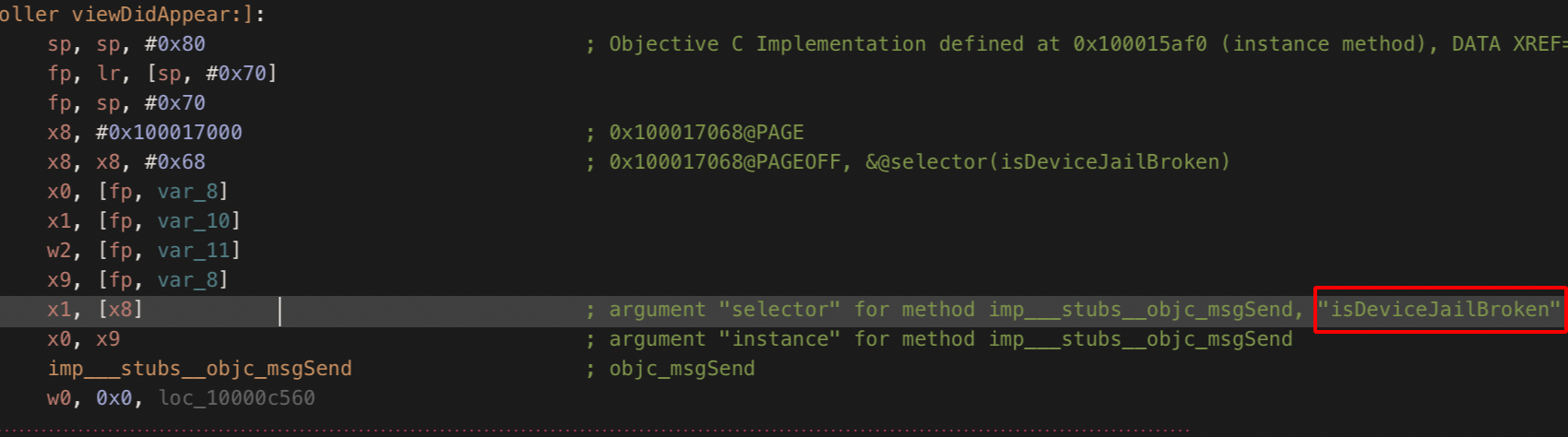
Step 9: Use the Graph View to see how the instructions sets works in details.
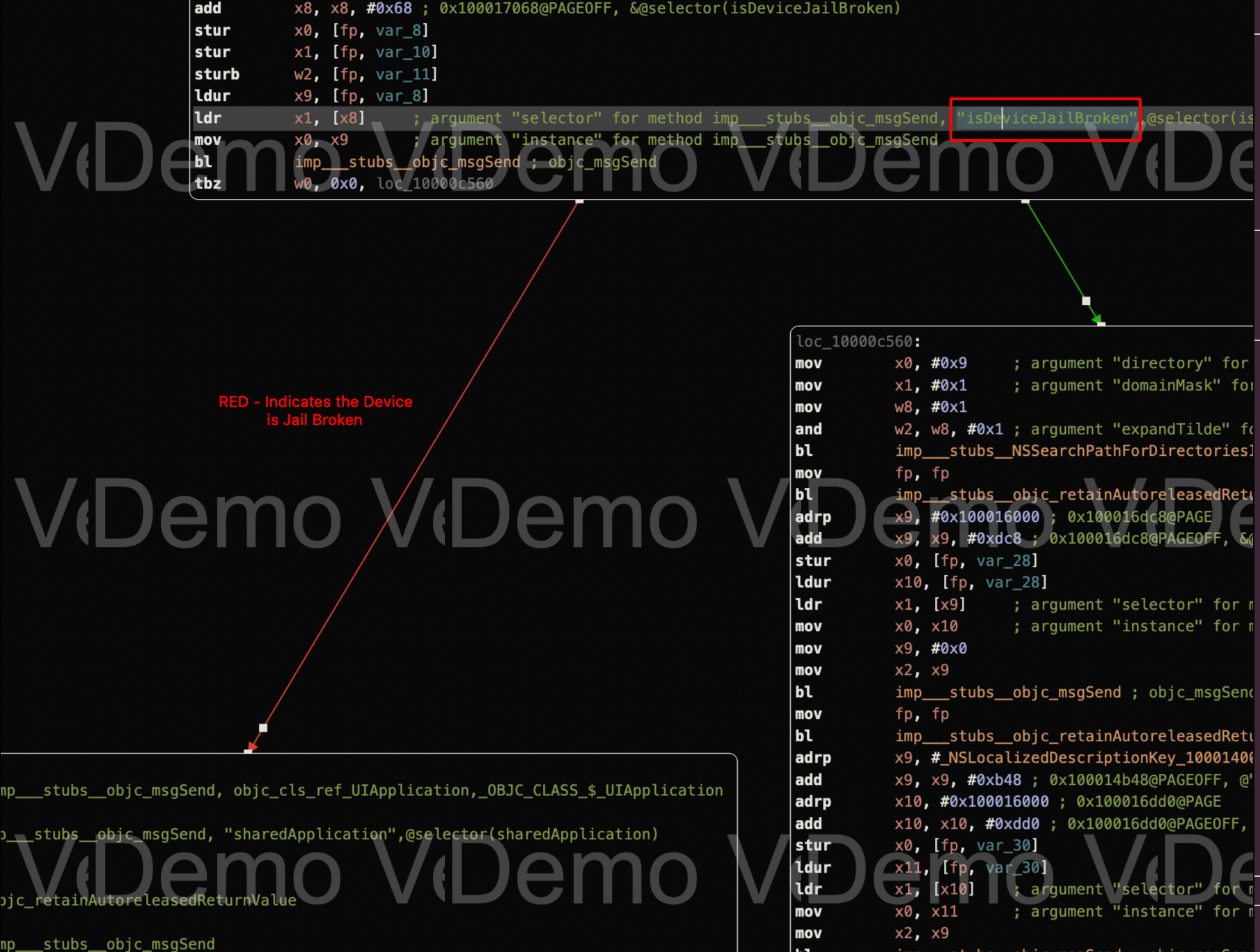
Step 10: From the red line, it can be observed that it executes the suspend and exit instruction set which causes the crash and closure of the application.
Step 11: The last Instruction tbz (Test bit and branch), it specifically test for a particular bit and takes a jump.
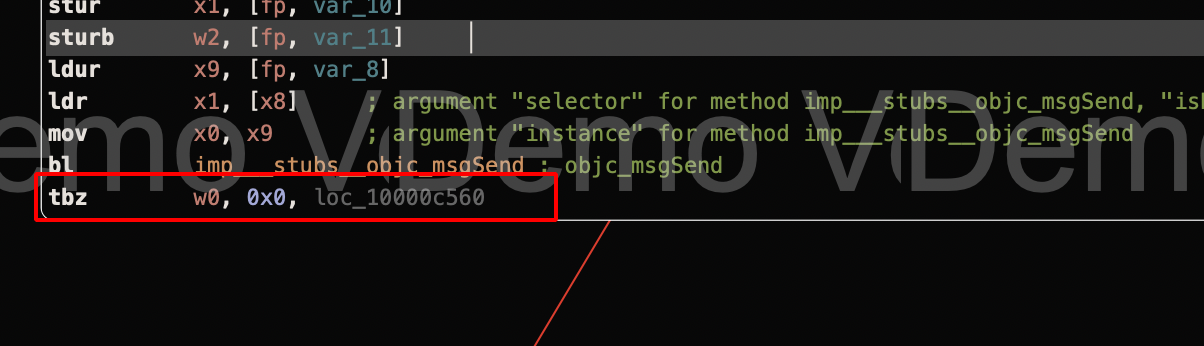
Step 12: We need to change the tbz -> tbnz which is the exact opposite of tbz instruction, so that the particular check will be skipped.
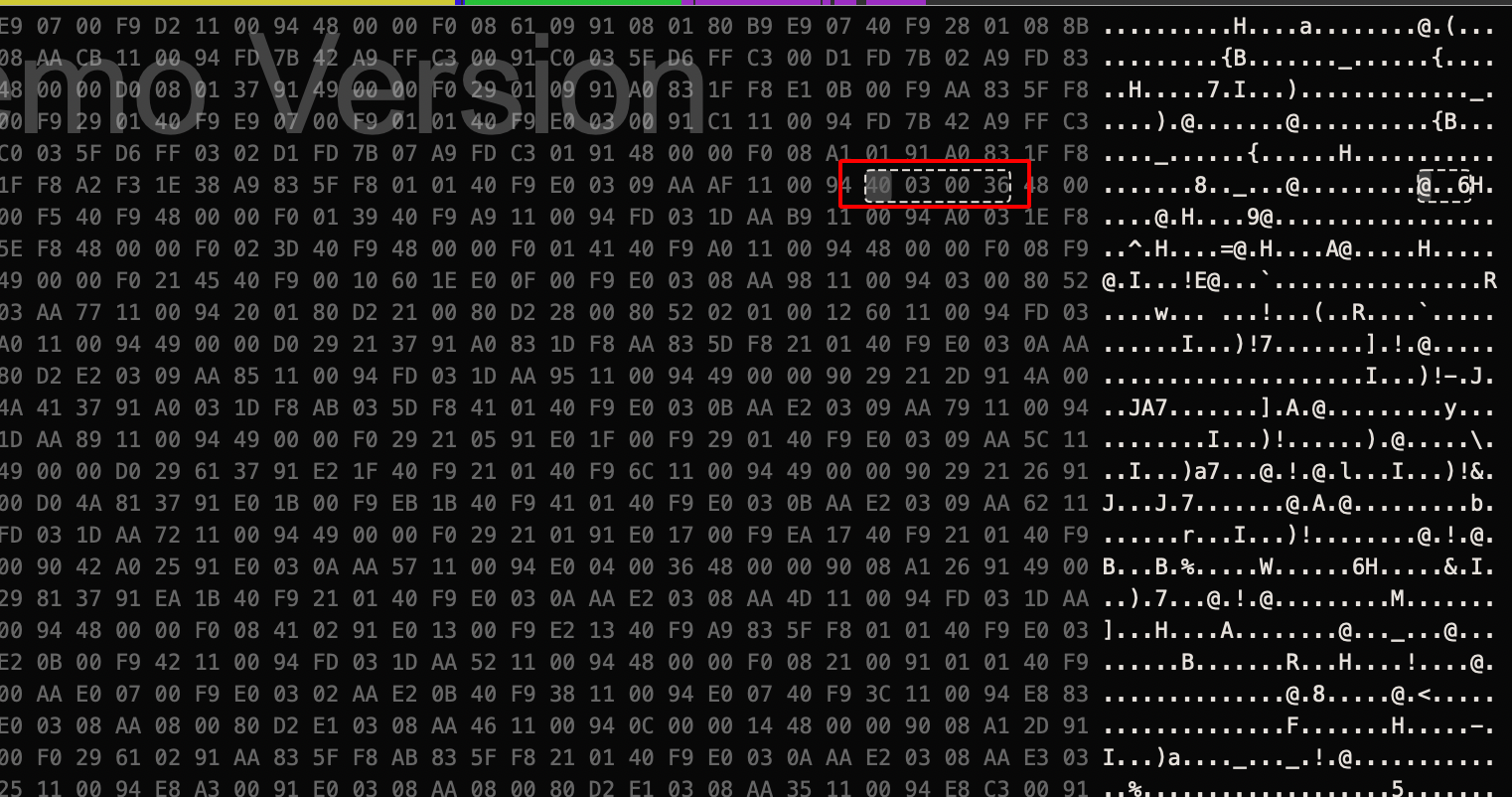
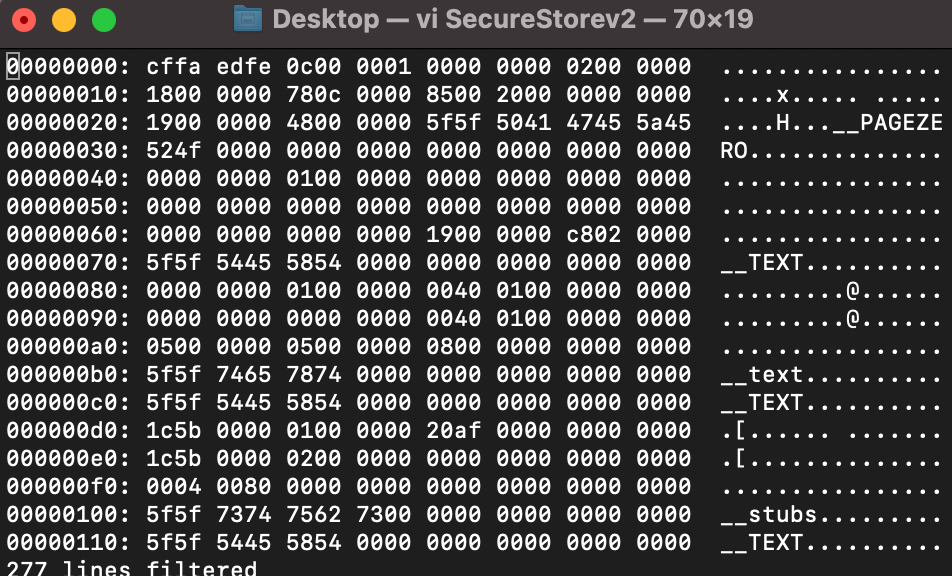
Step 13: Use hex option to view the arm instructions in Hex Format as shown below.
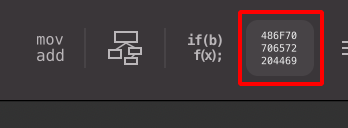
Note: Hopper Disassembler Free Demo version does not allow to save file and create a new executable.
Step 14: Use vi & xxd (hexeditor) to edit the binary file.
vi SecureStorev2
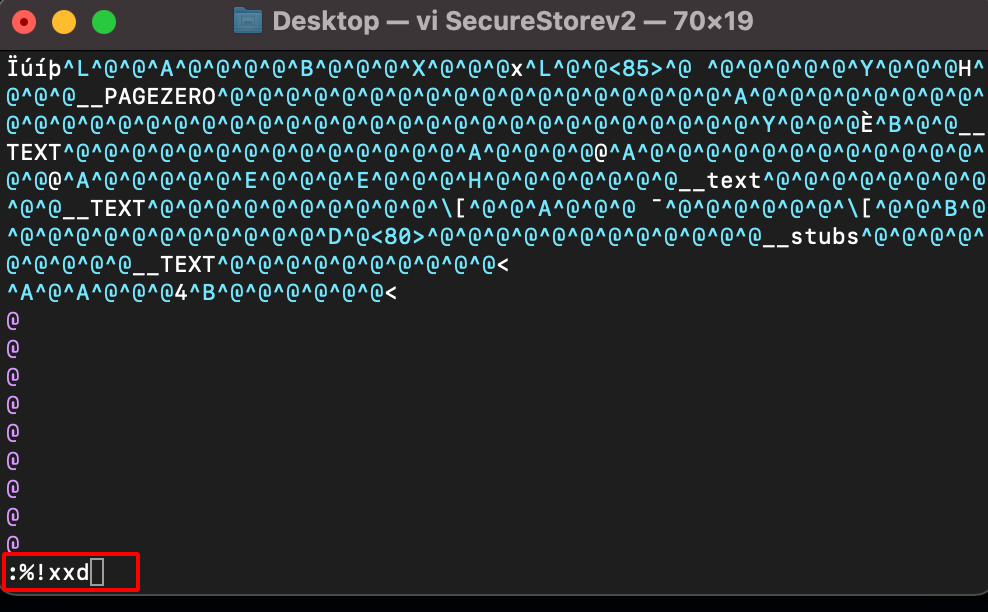
:%!xxd #covert the binary into hex
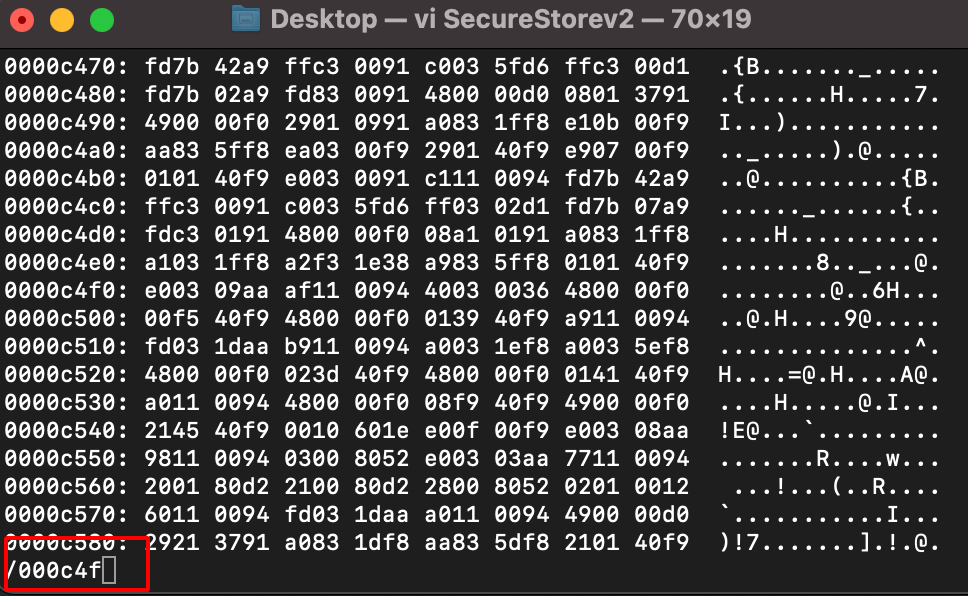
/00c4f #search for 40 03 00 36 hex value
Step 15: Find and replace the 40 03 00 36 –> 40 03 00 37 which will result in tbnz instruction set.
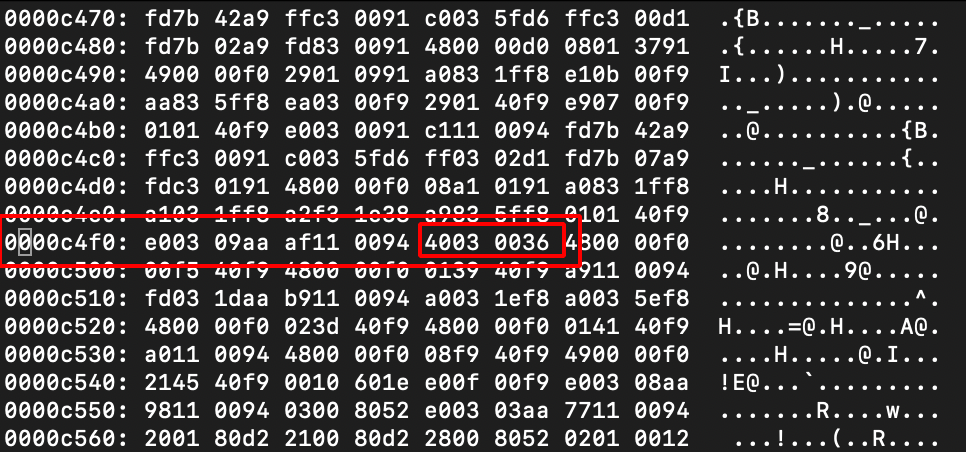
Before Changes
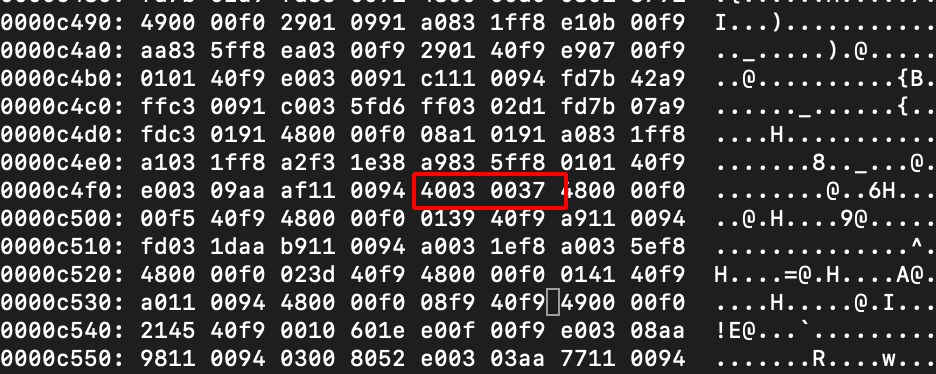
After Changes
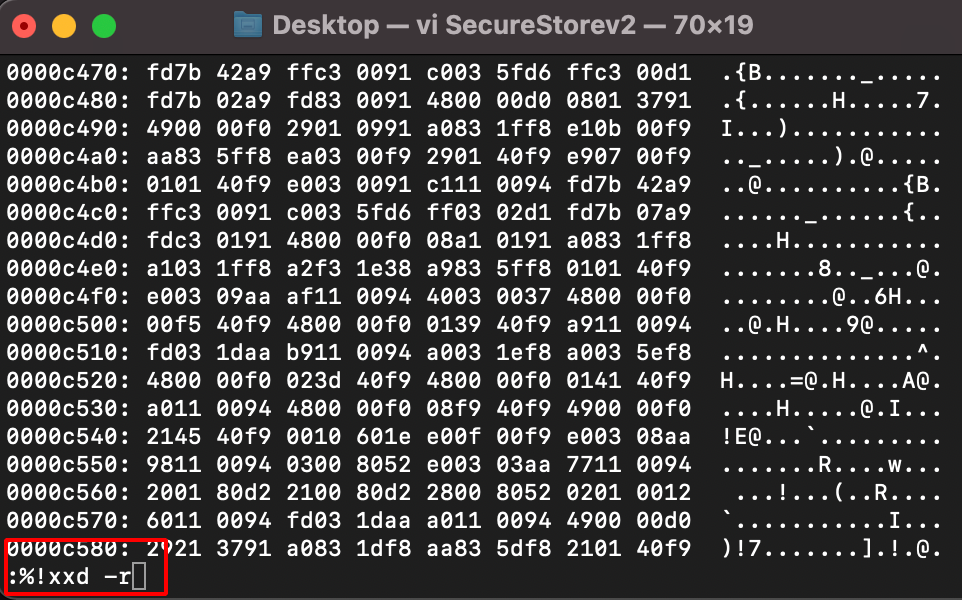
Step 16: Save the Binary using the following command.
:%!xxd -r
:wq! #save the binary file
Note : Make sure you remove the Old Binary and replace with the Edited One in the Payload Folder.
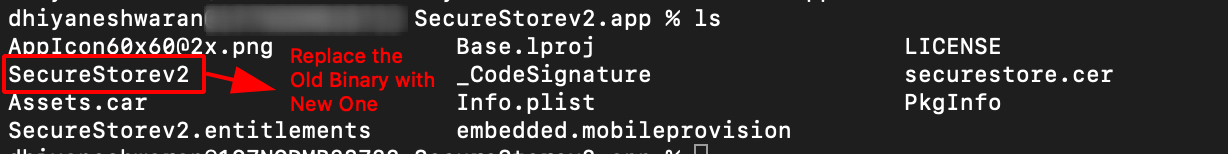
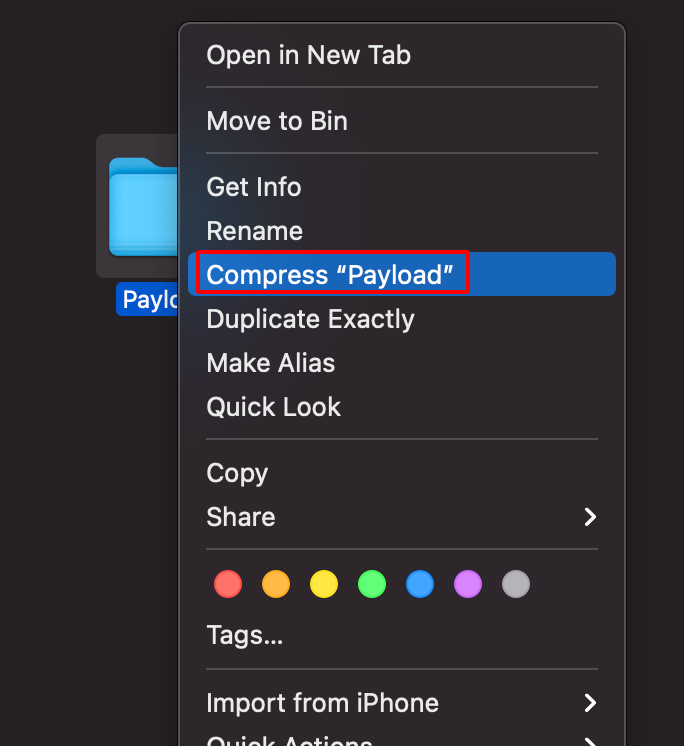
Step 17: Zip the Payload folder as shown below.
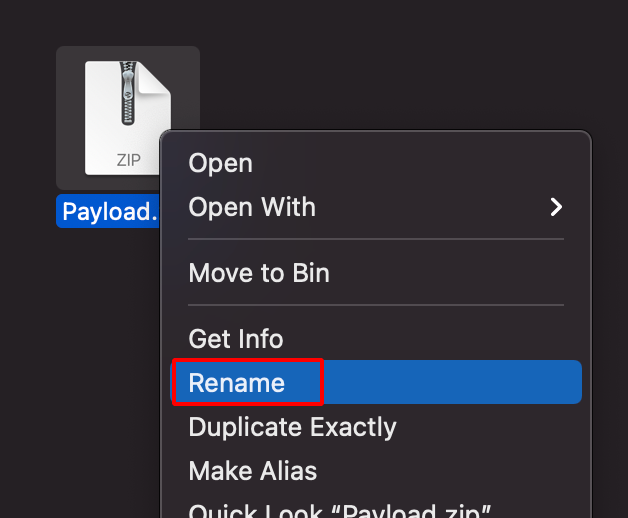
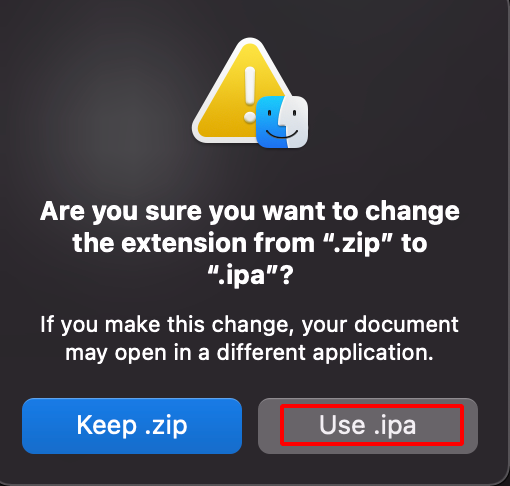
Step 18: Rename the .zip file to .ipa
Step 19: Install the Patched(Edited) app in the Jail Broken Iphone.

Step 20: From the below image, it can be observed that the application doesn’t crash and Bypasses the Jail Break Detection Successfully.
Reference:-
How to bypass Jailbreak detection using Hopper Disassembler in iOS apps
Jailbreak Detection and Bypass Techniques [iOS 12.2]
How to Hack/Patch Any iOS AppStore App | Reverse Engineering & ARM64 Assembly Tutorial
iOS Tampering and Reverse Engineering

Thanks a lot for reading !!!.